脚本内容 代码如下: from mitmproxy import http, ctxfrom multiprocessing import Lockclass Filter: def __init__(self, filter_info): self.log_info = "" self.mutex = Lock() self.filter_info = filter_info self.response_file = None self.
脚本内容
代码如下:
from mitmproxy import http, ctx
from multiprocessing import Lock
class Filter:
def __init__(self, filter_info):
self.log_info = ""
self.mutex = Lock()
self.filter_info = filter_info
self.response_file = None
self.switch_on = False
self.log_file = "log.txt"
def log(self, info) -> None:
self.log_info += f"{info}\n\n"
def write_log(self, mode="w+") -> None:
self.mutex.acquire()
with open(self.log_file, mode) as f:
f.write(self.log_info)
self.mutex.release()
def is_target_flow(self, flow: http.HTTPFlow) -> bool:
for info in self.filter_info:
if info["str_in_url"] in flow.request.url:
self.log_file = info["log_file"]
self.switch_on = info["switch_on"]
if info["response_file"] != None:
self.response_file = info["response_file"]
return True
else:
return False
def modify_response(self, flow: http.HTTPFlow) -> http.HTTPFlow:
if self.switch_on and self.response_file:
with open(self.response_file, "r") as f:
flow.response.content = f.read().encode()
return flow
def request(self, flow: http.HTTPFlow) -> None:
if self.is_target_flow(flow):
self.log_info = ""
self.log(f"——METHOD——\n{flow.request.method}")
self.log(f"——HOST——\n{flow.request.pretty_host}")
self.log(f"——URL——\n{flow.request.pretty_url}")
query = [i + ":" + flow.request.query[i] + "\n" for i in flow.request.query]
self.log(f"——QUERY STRING——\n{''.join(query)}")
if flow.request.urlencoded_form:
form = [i + ":" + flow.request.urlencoded_form[i] + "\n" for i in flow.request.urlencoded_form]
self.log(f"——FORM——\n{''.join(form)}")
self.write_log()
def response(self, flow: http.HTTPFlow) -> None:
if self.is_target_flow(flow):
self.log_info = ""
self.log(f"——RESPONSE before modified——\n{flow.response.content.decode()}")
flow = self.modify_response(flow)
self.log(f"——RESPONSE after modified——\n{flow.response.content.decode()}")
self.write_log(mode="a")
filter_info = [
{
"str_in_url": "getSimpleNews",
"log_file": "getSimpleNews_log.txt",
"switch_on": True,
"response_file": "getSimpleNews_response.txt",
},
{
"str_in_url": "getQQNewsComment",
"log_file": "getQQNewsComment_log.txt",
"switch_on": True,
"response_file": None,
}
]
addons = [
Filter(filter_info)
]
使用方法
运行mitmproxy指定使用该脚本和端口号即可:
mitmproxy -p 6666 -s xxx.py
在mitmproxy运行时:
1. 会拦截url中包含str_in_url字符串的请求
2. 会把response.content修改为当前mitm运行所在目录下的response_file文件中的内容
3. 打印信息在当前mitm运行所在目录下的log_file文件中
4. 如果无需修改response设置switch_on为False即为开关关闭
5. 如果不修改response的话response_file需要写None
补充知识:mitmproxy 监听指定端口
安装
使用python3的安装方式
https://mitmproxy.org/
监听指定端口
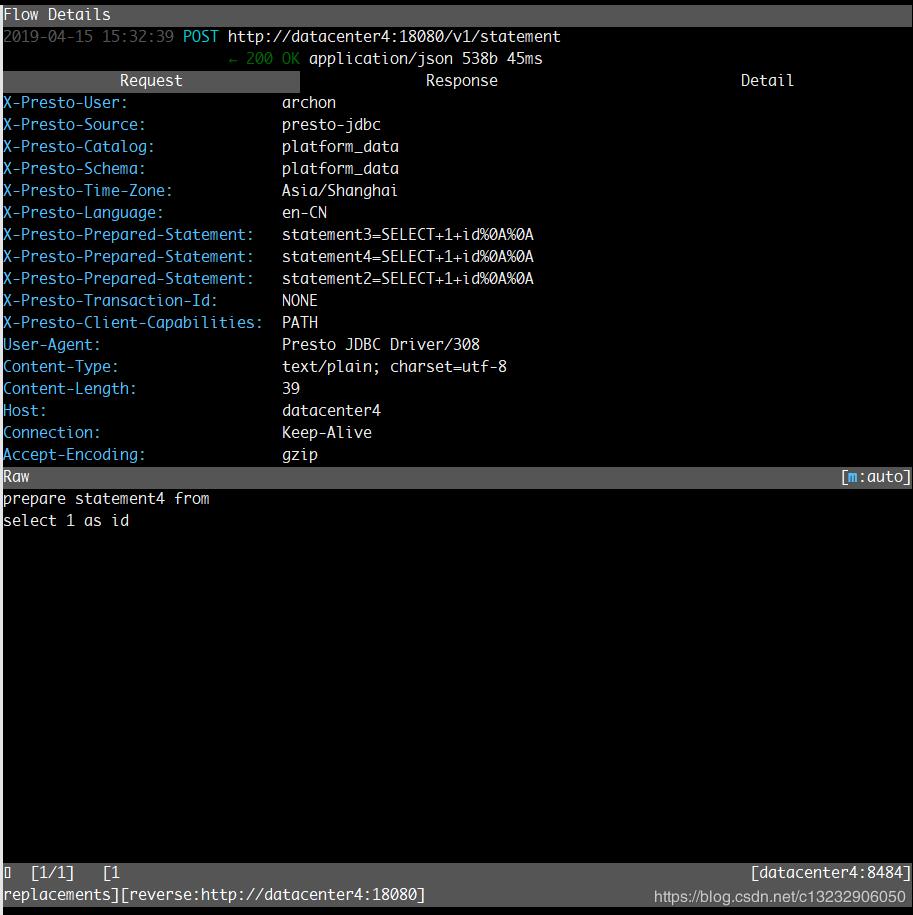
例子:Presto SQL请求的监听
Presto地址:http://datacenter4:18080
mitmproxy命令(端口8484)
mitmproxy \
--mode reverse:http://datacenter4:18080 \
--listen-host datacenter4 \
--listen-port 8484 \
--replacements :~s:\/\/datacenter4/:\/\/datacenter4:18080/
然后JDBC访问Presto使用:jdbc:presto://datacenter4:8484
效果
以上这篇Python3自定义http/https请求拦截mitmproxy脚本实例就是小编分享给大家的全部内容了,希望能给大家一个参考,也希望大家多多支持易盾网络。
