re1 逆向签到题 直接ida打开就可以看到flag。可以直接找main函数。 flag{7ujm8ikhy6} re2 用ollydebug打开,我的ida不好使了。。。。 这里是简单的异或 DH m qq vqxB^||zll@Jq jkwpmvez{ 脚本得到密钥 s
re1 逆向签到题
直接ida打开就可以看到flag。可以直接找main函数。
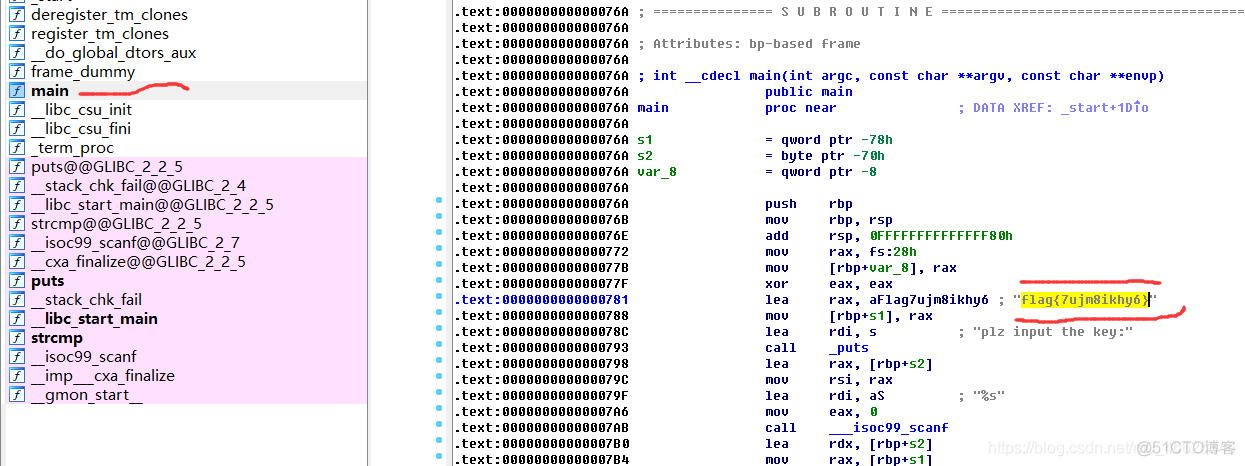
flag{7ujm8ikhy6}
re2
用ollydebug打开,我的ida不好使了。。。。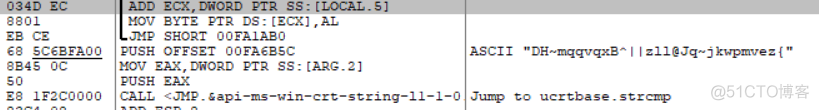
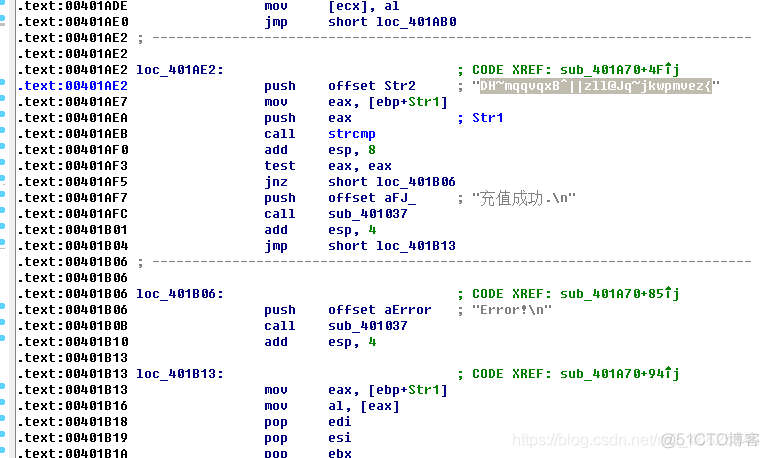
这里是简单的异或
DHmqqvqxB^||zll@Jqjkwpmvez{
脚本得到密钥
s="DH~mqqvqxB^||zll@Jq~jkwpmvez{"key=""
for c in s:
key+=chr(ord(c)^0x1f)
print(key)
#[Warnning]Access_Unauthorized
[Warnning]Access_Unauthorized
程序用密钥对明文flag进行RC4加密,现已知密文和密钥,写RC4解密脚本即可得到flag
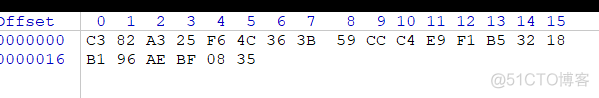
用winhex查看那个被加密的txt文档,这就是被加密的数据,放到代码的data中。
C++代码:
void rc4_init(unsigned char* s, unsigned char* key, unsigned long Len_k) //初始化函数
{
int i = 0, j = 0;
char k[256] = { 0 };
unsigned char tmp = 0;
for (i = 0; i < 256; i++) {
s[i] = i;
k[i] = key[i % Len_k];
}
for (i = 0; i < 256; i++) {
j = (j + s[i] + k[i]) % 256;
tmp = s[i];
s[i] = s[j];
s[j] = tmp;
}
}
void rc4_crypt(unsigned char* Data, unsigned long Len_D, unsigned char* key, unsigned long Len_k) //加解密
{
unsigned char s[256];
rc4_init(s, key, Len_k);
int i = 0, j = 0, t = 0;
unsigned long k = 0;
unsigned char tmp;
for (k = 0; k < Len_D; k++) {
i = (i + 1) % 256;
j = (j + s[i]) % 256;
tmp = s[i];
s[i] = s[j];
s[j] = tmp;
t = (s[i] + s[j]) % 256;
Data[k] = Data[k] ^ s[t];
}
}
int main()
{
unsigned char key[] = "[Warnning]Access_Unauthorized";
unsigned long key_len = sizeof(key) - 1;
unsigned char data[] = { 0xC3,0x82,0xA3,0x25,0xF6,0x4C,
0x36,0x3B,0x59,0xCC,0xC4,0xE9,0xF1,0xB5,0x32,0x18,0xB1,
0x96,0xAe,0xBF,0x08,0x35};
rc4_crypt(data, sizeof(data), key, key_len);
for (int i = 0; i < sizeof(data); i++)
{
printf("%c", data[i]);
}
printf("\n");
}
//flag{RC4&->ENc0d3F1le}
flag{RC4&->ENc0d3F1le}
