0x01. 进入环境,下载附件 题目给出的一个压缩包,解压压缩包后,发现是一个无后缀文件,放入kali中查看: 0x02. 问题分析 0x02_1. 得到套娃文件 修改文件的后缀为.tar,并进行压缩,得
0x01. 进入环境,下载附件
题目给出的一个压缩包,解压压缩包后,发现是一个无后缀文件,放入kali中查看:
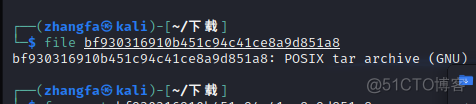
0x02. 问题分析
0x02_1. 得到套娃文件
修改文件的后缀为.tar,并进行压缩,得到两个文件:
0x02_2. 拿到公钥信息
from Crypto.PublicKey import RSAwith open('pic/key.pub', 'rb') as file:
f = file.read()
pub = RSA.importKey(f)
n = pub.n
e = pub.e
其中
n=833810193564967701912362955539789451139872863794534923259743419423089229206473091408403560311191545764221310666338878019
尝试在线进行大素数分解:大素数分解,得到分解后的 和
,其中:
p = 863653476616376575308866344984576466644942572246900013156919
q = 965445304326998194798282228842484732438457170595999523426901
0x02_3. 得到e
由p,q,e得到d
from gmpy2 import invertp = 863653476616376575308866344984576466644942572246900013156919
q = 965445304326998194798282228842484732438457170595999523426901
d = int(invert(e, (p - 1) * (q - 1)))
0x02_4. 得到私钥
rsa库的PrivateKey生成私钥
import rsakey = rsa.PrivateKey(n, e, d, p, q)
0x02_5. 对flag.b64用base64解码,再用key解密
from base64 import b64decodewith open('pic/flag.b64', 'r') as file:
f = file.read()
c = b64decode(f)
flag = rsa.decrypt(c, key).decode()
print(flag)
最终答案为:ALEXCTF{SMALL_PRIMES_ARE_BAD}
0x02_6. 总体代码
代码整理如下:
from Crypto.PublicKey import RSAfrom base64 import b64decode
from gmpy2 import invert
import rsa
with open('pic/key.pub', 'rb') as file:
f = file.read()
pub = RSA.importKey(f)
n = pub.n
e = pub.e
p = 863653476616376575308866344984576466644942572246900013156919
q = 965445304326998194798282228842484732438457170595999523426901
d = int(invert(e, (p - 1) * (q - 1)))
key = rsa.PrivateKey(n, e, d, p, q)
with open('pic/flag.b64', 'r') as file:
f = file.read()
c = b64decode(f)
flag = rsa.decrypt(c, key).decode()
print(flag)
RSA还是重中之重,长时间未接触,有点忘记,对于公钥私钥的加解密需要重新整理。
