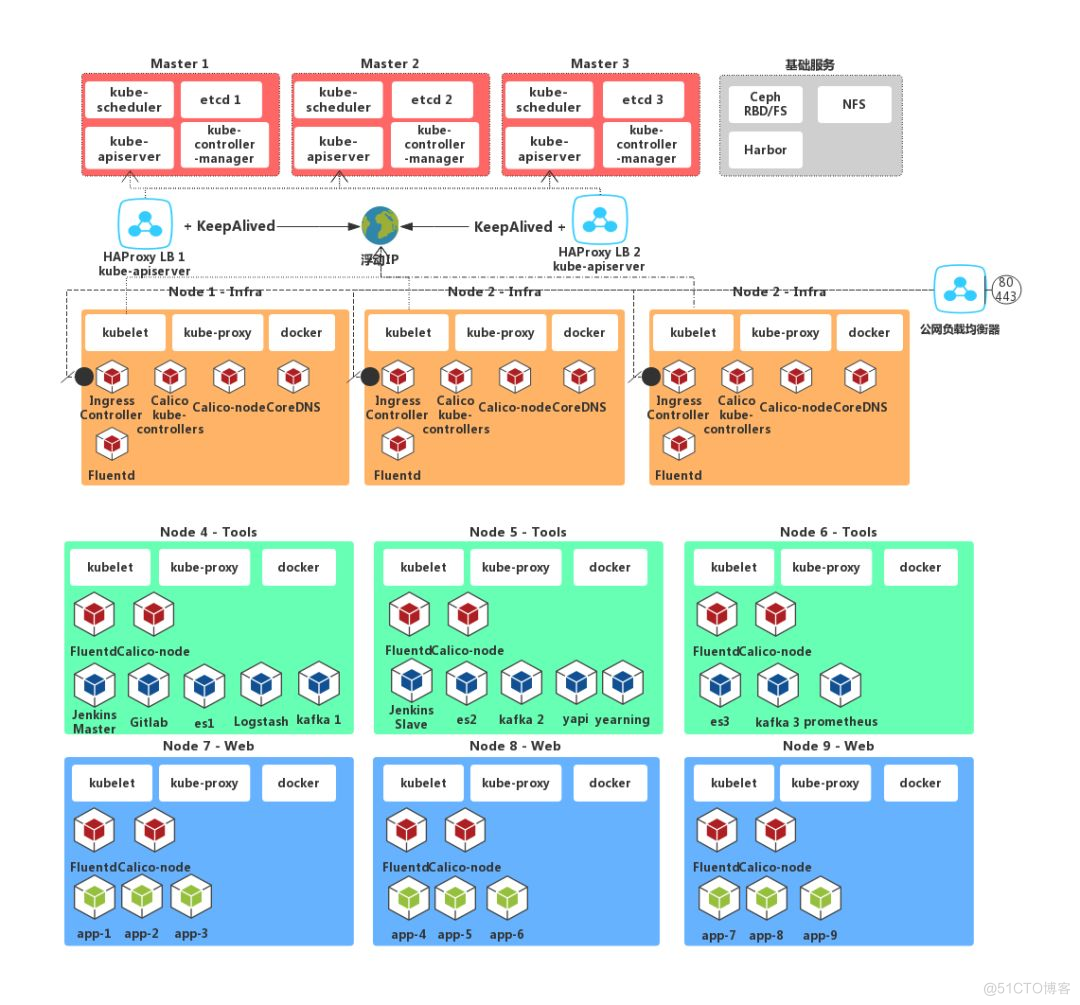
接着上一篇文档今天继续更新第二部分:证书部分也是K8S重点中的重点
上一篇文档路径:https://blog.51cto.com/linhuchong/5201329
开始正题,本次证书基本都是在master节点进行安装
1配置证书
1.1 下载自签名证书生成工具
#在分发机器Master-1上操作
[root@master-1 ~]# mkdir /soft && cd /soft[root@master-1 ~]# wget https://pkg.cfssl.org/R1.2/cfssl_linux-amd64[root@master-1 ~]# wget https://pkg.cfssl.org/R1.2/cfssljson_linux-amd64[root@master-1 ~]# wget https://pkg.cfssl.org/R1.2/cfssl-certinfo_linux-amd64[root@master-1 ~]# chmod +x cfssl_linux-amd64 cfssljson_linux-amd64 cfssl-certinfo_linux-amd64[root@master-1 ~]# mv cfssl_linux-amd64 /usr/local/bin/cfssl[root@master-1 ~]# mv cfssljson_linux-amd64 /usr/local/bin/cfssljson[root@master-1 ~]# mv cfssl-certinfo_linux-amd64 /usr/bin/cfssl-certinfo1.2 生成ETCD证书
#创建目录(Master-1)
[root@master-1 ~]# mkdir /root/etcd && cd /root/etcd1.2.1 CA 证书配置(Master-1)
[root@master-1 ~]# cat << EOF | tee ca-config.json{ "signing": { "default": { "expiry": "87600h" }, "profiles": { "www": { "expiry": "87600h", "usages": [ "signing", "key encipherment", "server auth", "client auth" ] } } }}EOF1.2.2 创建CA证书请求文件(Master-1)
[root@master-1 ~]# cat << EOF | tee ca-csr.json{ "CN": "etcd CA", "key": { "algo": "rsa", "size": 2048 }, "names": [ { "C": "CN", "L": "Beijing", "ST": "Beijing" } ]}EOF1.2.3 创建ETCD证书请求文件
#可以把所有的master IP 加入到csr文件中(Master-1)
[root@master-1 ~]# cat << EOF | tee server-csr.json{ "CN": "etcd", "hosts": [ "master-1", "master-2", "master-3", "192.168.91.18", "192.168.91.19", "192.168.91.20" ], "key": { "algo": "rsa", "size": 2048 }, "names": [ { "C": "CN", "L": "Beijing", "ST": "Beijing" } ]}EOF1.2.4 生成 ETCD CA 证书和ETCD公私钥(Master-1)
[root@master-1 ~]# cd /root/etcd/#生成ca证书(Master-1)
[root@master-1 ~]# cfssl gencert -initca ca-csr.json | cfssljson -bare ca –[root@master-1 etcd]# lltotal 24-rw-r--r-- 1 root root 287 Apr 5 11:23 ca-config.json #ca 的配置文件-rw-r--r-- 1 root root 956 Apr 5 11:26 ca.csr #ca 证书生成文件-rw-r--r-- 1 root root 209 Apr 5 11:23 ca-csr.json #ca 证书请求文件-rw------- 1 root root 1679 Apr 5 11:26 ca-key.pem #ca 证书key-rw-r--r-- 1 root root 1265 Apr 5 11:26 ca.pem #ca 证书-rw-r--r-- 1 root root 338 Apr 5 11:26 server-csr.json#生成etcd证书(Master-1)
[root@master-1 etcd]# cfssl gencert -ca=ca.pem -ca-key=ca-key.pem -config=ca-config.json -profile=www server-csr.json | cfssljson -bare server[root@master-1 etcd]# lltotal 36-rw-r--r-- 1 root root 287 Apr 5 11:23 ca-config.json-rw-r--r-- 1 root root 956 Apr 5 11:26 ca.csr-rw-r--r-- 1 root root 209 Apr 5 11:23 ca-csr.json-rw------- 1 root root 1679 Apr 5 11:26 ca-key.pem-rw-r--r-- 1 root root 1265 Apr 5 11:26 ca.pem-rw-r--r-- 1 root root 1054 Apr 5 11:31 server.csr-rw-r--r-- 1 root root 338 Apr 5 11:26 server-csr.json-rw------- 1 root root 1675 Apr 5 11:31 server-key.pem #etcd客户端使用-rw-r--r-- 1 root root 1379 Apr 5 11:31 server.pem1.3 创建 Kubernetes 相关证书
#此证书用于Kubernetes节点直接的通信, 与之前的ETCD证书不同. (Master-1)
[root@master-1 ~]# mkdir /root/kubernetes/ && cd /root/kubernetes/1.3.1 配置ca 文件(Master-1)
[root@master-1 ~]# cat << EOF | tee ca-config.json{ "signing": { "default": { "expiry": "87600h" }, "profiles": { "kubernetes": { "expiry": "87600h", "usages": [ "signing", "key encipherment", "server auth", "client auth" ] } } }}EOF1.3.2 创建ca证书申请文件(Master-1)
[root@master-1 ~]# cat << EOF | tee ca-csr.json{ "CN": "kubernetes", "key": { "algo": "rsa", "size": 2048 }, "names": [ { "C": "CN", "L": "Beijing", "ST": "Beijing", "O": "k8s", "OU": "System" } ]}EOF1.3.3 生成API SERVER证书申请文件(Master-1)
#注意要修改VIP的地址(阿里云配置SLB地址如果没有SLB配置任意一个master节点最好是mater-1节点)
[root@master-1 ~]# cat << EOF | tee server-csr.json{ "CN": "kubernetes", "hosts": [ "10.0.0.1", "127.0.0.1","10.0.0.2","192.168.91.18","192.168.91.19","192.168.91.20","192.168.91.21","192.168.91.22","192.168.91.254","master-1","master-2","master-3","node-1","node-2", "kubernetes", "kubernetes.default", "kubernetes.default.svc", "kubernetes.default.svc.cluster", "kubernetes.default.svc.cluster.local" ], "key": { "algo": "rsa", "size": 2048 }, "names": [ { "C": "CN", "L": "Beijing", "ST": "Beijing", "O": "k8s", "OU": "System" } ]}EOF1.3.4 创建 Kubernetes Proxy 证书申请文件(Master-1)
[root@master-1 ~]# cat << EOF | tee kube-proxy-csr.json{ "CN": "system:kube-proxy", "hosts": [], "key": { "algo": "rsa", "size": 2048 }, "names": [ { "C": "CN", "L": "Beijing", "ST": "Beijing", "O": "k8s", "OU": "System" } ]}EOF1.3.5 生成 kubernetes CA 证书和公私钥
# 生成ca证书(Master-1)
[root@master-1 ~]# cfssl gencert -initca ca-csr.json | cfssljson -bare ca –# 生成 api-server 证书(Master-1)
[root@master-1 ~]# cfssl gencert -ca=ca.pem -ca-key=ca-key.pem -config=ca-config.json -profile=kubernetes server-csr.json | cfssljson -bare server# 生成 kube-proxy 证书(Master-1)
[root@master-1 ~]# cfssl gencert -ca=ca.pem -ca-key=ca-key.pem -config=ca-config.json \-profile=kubernetes kube-proxy-csr.json | cfssljson -bare kube-proxy2 部署ETCD
#下载etcd二进制安装文件(所有master)
[root@master-1 ~]# mkdir -p /soft && cd /soft[root@master-1 ~]# wget https://github.com/etcd-io/etcd/releases/download/v3.3.10/etcd-v3.3.10-linux-amd64.tar.gz[root@master-1 ~]# tar -xvf etcd-v3.3.10-linux-amd64.tar.gz[root@master-1 ~]# cd etcd-v3.3.10-linux-amd64/[root@master-1 ~]# cp etcd etcdctl /usr/local/bin/2.1 编辑etcd配置文件(所有master)
#注意修改每个节点的ETCD_NAME
#注意修改每个节点的监听地址
[root@master-1 ~]# mkdir -p /etc/etcd/{cfg,ssl}[root@master-1 ~]# cat >/etc/etcd/cfg/etcd.conf<<EOFL#[Member]ETCD_NAME="master-1"ETCD_DATA_DIR="/var/lib/etcd/default.etcd"ETCD_LISTEN_PEER_URLS="https://192.168.91.18:2380"ETCD_LISTEN_CLIENT_URLS="https://192.168.91.18:2379,http://192.168.91.18:2390"#[Clustering]ETCD_INITIAL_ADVERTISE_PEER_URLS="https://192.168.91.18:2380"ETCD_ADVERTISE_CLIENT_URLS="https://192.168.91.18:2379"ETCD_INITIAL_CLUSTER="master-1=https://192.168.91.18:2380,master-2=https://192.168.91.19:2380,master-3=https://192.168.91.20:2380"ETCD_INITIAL_CLUSTER_TOKEN="etcd-cluster"ETCD_INITIAL_CLUSTER_STATE="new"EOFL2.2创建ETCD的系统启动服务(所有master)
[root@master-1 ~]# cat > /usr/lib/systemd/system/etcd.service<<EOFL[Unit]Description=Etcd ServerAfter=network.targetAfter=network-online.targetWants=network-online.target[Service]Type=notifyEnvironmentFile=/etc/etcd/cfg/etcd.confExecStart=/usr/local/bin/etcd \--name=\${ETCD_NAME} \--data-dir=\${ETCD_DATA_DIR} \--listen-peer-urls=\${ETCD_LISTEN_PEER_URLS} \--listen-client-urls=\${ETCD_LISTEN_CLIENT_URLS},http://127.0.0.1:2379 \--advertise-client-urls=\${ETCD_ADVERTISE_CLIENT_URLS} \--initial-advertise-peer-urls=\${ETCD_INITIAL_ADVERTISE_PEER_URLS} \--initial-cluster=\${ETCD_INITIAL_CLUSTER} \--initial-cluster-token=\${ETCD_INITIAL_CLUSTER_TOKEN} \--initial-cluster-state=new \--cert-file=/etc/etcd/ssl/server.pem \--key-file=/etc/etcd/ssl/server-key.pem \--peer-cert-file=/etc/etcd/ssl/server.pem \--peer-key-file=/etc/etcd/ssl/server-key.pem \--trusted-ca-file=/etc/etcd/ssl/ca.pem \--peer-trusted-ca-file=/etc/etcd/ssl/ca.pemRestart=on-failureLimitNOFILE=65536[Install]WantedBy=multi-user.targetEOFL2.3 复制etcd证书到指定目录
[root@master-1 ~]# mkdir -p /etc/etcd/ssl/[root@master-1 ~]# \cp /root/etcd/*pem /etc/etcd/ssl/ -rf#复制etcd证书到每个节点
[root@master-1 ~]# for i in master-2 master-3 node-1 node-2;do ssh $i mkdir -p /etc/etcd/{cfg,ssl};done[root@master-1 ~]# for i in master-2 master-3 node-1 node-2;do scp /etc/etcd/ssl/* $i:/etc/etcd/ssl/;done[root@master-1 ~]# for i in master-2 master-3 node-1 node-2;do echo $i "------>"; ssh $i ls /etc/etcd/ssl;done2.4 启动etcd (所有节点)
[root@master-1 ~]# chkconfig etcd on[root@master-1 ~]# service etcd start[root@master-1 ~]# service etcd status2.5 检查etcd 集群是否运行正常
[root@master-1 ~]# etcdctl --ca-file=/etc/etcd/ssl/ca.pem --cert-file=/etc/etcd/ssl/server.pem \--key-file=/etc/etcd/ssl/server-key.pem --endpoints="https://192.168.91.18:2379" cluster-healthmember bcef4c3b581e1d2e is healthy: got healthy result from https://192.168.91.18:2379member d99a26304cec5ace is healthy: got healthy result from https://192.168.91.19:2379member fc4e801f28271758 is healthy: got healthy result from https://192.168.91.20:2379cluster is healthy到此证书安装以及etcd已安装完毕。回顾一下证书需要安装什么首先是etcd的ca证书安装安装创建etcd证书 然后呢第二步创建kubernetes的ca证书生成api server证书后创建 Kubernetes Proxy证书去生成kubernetes证书。然后部署etcd服务配置到所有节点上,同步etcd证书到所有节点,启动服务后查看所有master服务的etcd集群的服务状态。
本篇到此结束,接下来我们会安装docker后配置k8s网络。这是重点的重点。
