1、PAM和google模块实现ssh双因子安全验证
pam_google_authenticator模块
功能:实现SSH登录的两次身份验证,先验证APP的数字码,再验证root用户的密码,都通过才可以登录。目前只支持口令验证,不支持基于key验证官方网站:https://github.com/google/google-authenticator-android范例:1、 在手机应用市场搜索:身份验证器或authenticator,并安装APP2、 运行脚本(需要联网EPEL源),本质是修改了/etc/pam.d/sshd文件,将google的PAM模块加入进去实现
[root@CentOS8 scripts]#cat google-authenticator.sh #安装epel #yum install -y epel-release.noarch #yum makecache #安装google authenticator yum install -y google-authenticator.x86_64 echo -e "\033[31mDo you want me to update your "/root/.google_authenticator" file? (y/n) y" echo -e "\033[31m你希望我更新你的“/root/.google_authenticator”文件吗(y/n)?\033[0m" echo -e "\033[31mDo you want to disallow multiple uses of the same authentication" echo -e "\033[31mtoken? This restricts you to one login about every 30s, but it increases" echo -e "\033[31myour chances to notice or even prevent man-in-the-middle attacks (y/n) y" echo -e "\033[31m你希望禁止多次使用同一个验证令牌吗?这限制你每次登录的时间大约是30秒, 但是这加大了发现或甚至防止中间人的可能性(y/n)?\033[0m" echo -e "\033[31mBy default, a new token is generated every 30 seconds by the mobile app." echo -e "\033[31mIn order to compensate for possible time-skew between the client and the server," echo -e "\033[31mwe allow an extra token before and after the current time. This allows for a" echo -e "\033[31mtime skew of up to 30 seconds between authentication server and client. If you" echo -e "\033[31mexperience problems with poor time synchronization, you can increase the window" echo -e "\033[31mfrom its default size of 3 permitted codes (one previous code, the current" echo -e "\033[31mcode, the next code) to 17 permitted codes (the 8 previous codes, the current" echo -e "\033[31mcode, and the 8 next codes). This will permit for a time skew of up to 4 minutes" echo -e "\033[31mbetween client and server." echo -e "\033[31mDo you want to do so? (y/n) y" echo -e "\033[31m默认情况下,令牌保持30秒有效;为了补偿客户机与服务器之间可能存在的时滞,\033[0m" echo -e "\033[31m我们允许在当前时间前后有一个额外令牌。如果你在时间同步方面遇到了问题, 可以增加窗口从默认的3个可通过验证码增加到17个可通过验证码,\033[0m" echo -e "\033[31m这将允许客户机与服务器之间的时差增加到4分钟。你希望这么做吗(y/n)?\033[0m" echo -e "\033[31mIf the computer that you are logging into isn't hardened against brute-force" echo -e "\033[31mlogin attempts, you can enable rate-limiting for the authentication module." echo -e "\033[31mBy default, this limits attackers to no more than 3 login attempts every 30s." echo -e "\033[31mDo you want to enable rate-limiting? (y/n) y" echo -e "\033[31m如果你登录的那台计算机没有经过固化,以防范运用蛮力的登录企图,可以对验证模块\033[0m" echo -e "\033[31m启用尝试次数限制。默认情况下,这限制访问者每30秒试图登录的次数只有3次。 你希望启用尝试次数限制吗(y/n)?\033[0m" echo -e "\033[32m 在App Store 搜索Google Authenticator 进行App安装 \033[0m" google-authenticator #/etc/pam.d/sshd文件,修改或添加下行保存 #auth required pam_google_authenticator.so sed -i '1a\auth required pam_google_authenticator.so' /etc/pam.d/sshd #编辑/etc/ssh/sshd_config找到下行 #ChallengeResponseAuthentication no #更改为 #ChallengeResponseAuthentication yes sed -i 's/.*ChallengeResponseAuthentication.*/ChallengeResponseAuthentication yes/' /etc/ssh/sshd_config #重启SSH服务 service sshd restart [root@centos8 ~]#dnf info google-authenticator BaseOS 3.3 MB/s | 3.9 kB 00:00 AppStream 2.9 MB/s | 4.3 kB 00:00 EPEL 34 kB/s | 4.7 kB 00:00 extras 7.3 kB/s | 1.5 kB 00:00 Available Packages Name : google-authenticator Version : 1.07 Release : 1.el8 Architecture : x86_64 Size : 57 k Source : google-authenticator-1.07-1.el8.src.rpm Repository : epel Summary : One-time pass-code support using open standards URL : https://github.com/google/google-authenticator-libpam/ License : ASL 2.0 Description : The Google Authenticator package contains a plug-able authentication : module (PAM) which allows login using one-time pass-codes conforming to : the open standards developed by the Initiative for Open Authentication : (OATH) (which is unrelated to OAuth). : : Pass-code generators are available (separately) for several mobile : platforms. : : These implementations support the HMAC-Based One-time Password (HOTP) : algorithm specified in RFC 4226 and the Time-based One-time Password : (TOTP) algorithm currently in draft. [root@centos8 ~]#bash google-authenticator.sh Installed: google-authenticator-1.07-1.el8.x86_64 Complete! Do you want me to update your /root/.google_authenticator file? (y/n) y 你希望我更新你的“/root/.google_authenticator”文件吗(y/n)? Do you want to disallow multiple uses of the same authentication token? This restricts you to one login about every 30s, but it increases your chances to notice or even prevent man-in-the-middle attacks (y/n) y 你希望禁止多次使用同一个验证令牌吗?这限制你每次登录的时间大约是30秒, 但是这加大了发现或甚 至防止中间人的可能性(y/n)? By default, a new token is generated every 30 seconds by the mobile app. In order to compensate for possible time-skew between the client and the server, we allow an extra token before and after the current time. This allows for a time skew of up to 30 seconds between authentication server and client. If you3. 访问生成的url: experience problems with poor time synchronization, you can increase the window from its default size of 3 permitted codes (one previous code, the current code, the next code) to 17 permitted codes (the 8 previous codes, the current code, and the 8 next codes). This will permit for a time skew of up to 4 minutes between client and server. Do you want to do so? (y/n) y 默认情况下,令牌保持30秒有效;为了补偿客户机与服务器之间可能存在的时滞, 我们允许在当前时间前后有一个额外令牌。如果你在时间同步方面遇到了问题, 可以增加窗口从默认的 3个可通过验证码增加到17个可通过验证码, 这将允许客户机与服务器之间的时差增加到4分钟。你希望这么做吗(y/n)? If the computer that you are logging into isn't hardened against brute-force login attempts, you can enable rate-limiting for the authentication module. By default, this limits attackers to no more than 3 login attempts every 30s. Do you want to enable rate-limiting? (y/n) y 如果你登录的那台计算机没有经过固化,以防范运用蛮力的登录企图,可以对验证模块 启用尝试次数限制。默认情况下,这限制访问者每30秒试图登录的次数只有3次。 你希望启用尝试次数 限制吗(y/n)? 在App Store 搜索Google Authenticator 进行App安装 Do you want authentication tokens to be time-based (y/n) y Warning: pasting the following URL into your browser exposes the OTP secret to Google: https://www.google.com/chart? chs=200x200&chld=M|0&cht=qr&chl=otpauth://totp/root@centos8.localdomain%3Fse cret%3D7YTAL4GW3TND7BICUMJGJLIFVE%26issuer%3Dcentos8.localdomain #浏览器打开 此地址 Failed to use libqrencode to show QR code visually for scanning. Consider typing the OTP secret into your app manually. Your new secret key is: 7YTAL4GW3TND7BICUMJGJLIFVE Enter code from app (-1 to skip):3、访问生成的url
https://www.google.com/chart? chs=200x200&chld=M|0&cht=qr&chl=otpauth://totp/root@centos8.localdomain%3Fse cret%3D7YTAL4GW3TND7BICUMJGJLIFVE%26issuer%3Dcentos8.localdomain #浏览器打开 此地址4、打开用身份验证器APP,扫网页上的二维码,进行绑定手机
5、继续上面的安装配置向导,输入手机APP上的数字,后续都回答 y 即可
Failed to use libqrencode to show QR code visually for scanning. Consider typing the OTP secret into your app manually. Your new secret key is: 7YTAL4GW3TND7BICUMJGJLIFVE Enter code from app (-1 to skip): 224421 #手机APP上的数字 Code confirmed Your emergency scratch codes are: 68820657 77385307 50928320 41000243 54628309 Do you want me to update your "/root/.google_authenticator" file? (y/n) y Do you want to disallow multiple uses of the same authentication token? This restricts you to one login about every 30s, but it increases your chances to notice or even prevent man-in-the-middle attacks (y/n) y By default, a new token is generated every 30 seconds by the mobile app. In order to compensate for possible time-skew between the client and the server, we allow an extra token before and after the current time. This allows for a time skew of up to 30 seconds between authentication server and client. If you experience problems with poor time synchronization, you can increase the window from its default size of 3 permitted codes (one previous code, the current code, the next code) to 17 permitted codes (the 8 previous codes, the current code, and the 8 next codes). This will permit for a time skew of up to 4 minutes between client and server. Do you want to do so? (y/n) y If the computer that you are logging into isn't hardened against brute-force login attempts, you can enable rate-limiting for the authentication module. By default, this limits attackers to no more than 3 login attempts every 30s. Do you want to enable rate-limiting? (y/n) y Redirecting to /bin/systemctl restart sshd.service [root@centos8 ~]#6、ssh 当前主机,可看到提示,输入手机APP上显示的数字码和root密码,可以登录,否则失败
[root@centos7 ~]#ssh 10.0.0.8 Verification code: Password: Last failed login: Fri Feb 7 12:11:12 CST 2020 from 10.0.0.7 on ssh:notty There were 6 failed login attempts since the last successful login. Last login: Fri Feb 7 12:09:47 2020 from 10.0.0.7 [root@centos8 ~]#7、临时口令存放在/root/.google_authenticator中,用一次删除一个,可手动加入使用
[root@centos8 ~]#cat .google_authenticator 7YTAL4GW3TND7BICUMJGJLIFVE " RATE_LIMIT 3 30 " WINDOW_SIZE 17 " DISALLOW_REUSE " TOTP_AUTH 68820657 77385307 50928320 41000243 54628309 [root@centos8 ~]#2、时间同步服务
加密和安全当前都离不开时间的同步,否则各种网络服务可能不能正常运行 。
时间同步服务多主机协作工作时,各个主机的时间同步很重要,时间不一致会造成很多重要应用的故障,如:加密协议,日志,集群等, 利用NTP(Network Time Protocol) 协议使网络中的各个计算机时间达到同步。目前NTP协议属于运维基础架构中必备的基本服务之一
时间同步软件实现:
- ntp
- chrony
ntp:
将系统时钟和世界协调时UTC同步,精度在局域网内可达0.1ms,在互联网上绝大多数的地方精度可以达到1-50ms项目官网:http://www.ntp.org
chrony:
实现NTP协议的的自由软件。可使系统时钟与NTP服务器,参考时钟(例如GPS接收器)以及使用手表和键盘的手动输入进行同步。还可以作为NTPv4(RFC 5905)服务器和对等体运行,为网络中的计算机提供时间服务。设计用于在各种条件下良好运行,包括间歇性和高度拥挤的网络连接,温度变化(计算机时钟对温度敏感),以及不能连续运行或在虚拟机上运行的系统。通过Internet同步的两台机器之间的典型精度在几毫秒之内,在LAN上,精度通常为几十微秒。利用硬件时间戳或硬件参考时钟,可实现亚微秒的精度 。
2.1 使用chrony实现内网时间同步(一台node1从外网同步时间,其余机器从node1同步时间)
#修改chrony.conf文件 [root@CentOS8 ~]#vim /etc/chrony.conf [root@CentOS8 ~]#grep -v "^#" /etc/chrony.conf pool ntp.aliyun.com iburst #修改ntp服务地址池 pool s1b.time.edu.cn iburst allow 0.0.0.0/0 #允许同步的客户端网段 local stratum 10 #即使互联网同步失败,也允许其它客户端同步时间 [root@CentOS8 ~]#systemctl restart chronyd.service #修改客户端chrony.conf文件 [root@Centos7 ~]#vim /etc/chrony.conf server 10.0.0.8 iburst #修改为chrony服务器地址 [root@Centos7 ~]#chronyc sources -v 210 Number of sources = 1 .-- Source mode '^' = server, '=' = peer, '#' = local clock. / .- Source state '*' = current synced, '+' = combined , '-' = not combined, | / '?' = unreachable, 'x' = time may be in error, '~' = time too variable. || .- xxxx [ yyyy ] +/- zzzz || Reachability register (octal) -. | xxxx = adjusted offset, || Log2(Polling interval) --. | | yyyy = measured offset, || \ | | zzzz = estimated error. || | | \ MS Name/IP address Stratum Poll Reach LastRx Last sample =============================================================================== ^* localhost 3 6 17 9 +26us[ -23us] +/- 103ms3、利用cobbler实现系统自动化安装
3.1 Cobbler简介
-
Cobbler是一款Linux生态的自动化运维工具,基于Python2开发,用于自动化批量部署安装操作系统;其提供基于CLI的管理方式和WEB配置界面,其中WEB配置界面是基于Python2和Django框架开发。另外,cobbler还提供了API,方便二次开发。Cobbler属于C/S模型(客户端/服务器模型)
- Cobbler主要用于快速网络安装linux操作系统,支持众多的Linux发行版如:Red Hat、Fedora、CentOS、Debian、Ubuntu和SuSE等,甚至支持windows的安装
- Cobbler实质是PXE的二次封装,将多种安装参数封装到一起,并提供统一的管理方法
3.2 Cobbler相关服务
- 使用Cobbler安装系统需要一台专门提供各种服务的服务器,提供的服务包括(HTTP/FTP/NFS,TFTP,DHCP),也可以将这几个服务分别部署到不同服务器。事实上在实际应用中,总是将不同的服务分别部署到专门的服务器 。
- Cobbler是在HTTP、TFTP、DHCP等各种服务的基础上进行相关操作的,实际安装的大体过程类似于基于PXE的网络安装:客户端(裸机)开机使用网卡引导启动,其请求DHCP分配一个地址后从TFTP服务器获取启动文件,加载到客户端本地内存中运行,并显示出可安装的系统列表;在人为的选定安装的操作系统类型后,客服端会到HTTP服务器下载相应的系统安装文件并执行自动安装 。
3.3 Cobbler工作原理
- client裸机配置了从网络启动后,开机后会广播包请求DHCP服务器(cobbler server)发送其分配好的一个IP
- DHCP服务器(cobbler server)收到请求后发送responese,包括其ip地址
- client裸机拿到ip后再向cobbler server发送请求OS引导文件的请求
- cobbler server告诉裸机OS引导文件的名字和TFTP server的ip和port
- client裸机通过上面告知的TFTP server地址通信,下载引导文件
- client裸机执行执行该引导文件,确定加载信息,选择要安装的os,期间会再向cobbler server请求kickstart文件和os image
- cobbler server发送请求的kickstart和os iamge
- client裸机加载kickstart文件
- client裸机接收os image,安装该os image
3.4 安装Cobbler及相关服务和组件
Cobbler所依赖的服务包括HTTPD,TFTP,DHCP等,如果有web界面要求,还需要安装相关的组件CentOS 8目前还没有提供Cobbler相关包
[root@centos7 ~]#yum -y install dhcp cobbler cobbler-web pykickstart [root@centos7 ~]#systemctl enable --now cobbler httpd tftp dhcpd相关包说明:
- httpd:提供yum源,并配合cobbler-web使得cobbler可以通过web网页界面进行配置管理
- tftp-server:提供启动和菜单等相关文件网络下载功能
- cobbler-web : 提供基于web的cobbler管理界面
- pykickstart.noarch : 基于python的管理kickstart文件的库
说明:
- Cobbler依赖于epel源,在安装cobbler之前需要配置epel源
- 在安装cobbler时会因为依赖而安装httpd,tftp-server相关包
3.5 Cobbler配置文件及各目录情况
3.5.1 配置文件
/etc/cobbler/settings #cobbler 主配置文件 /etc/cobbler/iso/ #iso模板配置文件 /etc/cobbler/pxe #pxe模板文件 /etc/cobbler/power #电源配置文件 /etc/cobbler/user.conf #web服务授权配置文件 /etc/cobbler/users.digest #web访问的用户名密码配置文件 /etc/cobbler/dhcp.template #dhcp服务器的的配置模板 /etc/cobbler/dnsmasq.template #dns服务器的配置模板 /etc/cobbler/tftpd.template #tftp服务的配置模板 /etc/cobbler/modules.conf #cobbler模块的配置文件3.5.2 数据目录
/var/lib/cobbler/config/ #用于存放distros,system,profiles 等信息的配置文件 /var/lib/cobbler/triggers/ #用于存放用户定义的cobbler命令 /var/lib/cobbler/kickstarts/ # 默认存放kickstart文件 /var/lib/cobbler/loaders/ #存放各种引导程序3.5.3 镜像目录
/var/www/cobbler/ks_mirror/ #导入的发行版系统的所有数据 /var/www/cobbler/images/ #导入发行版kernel和initrd镜像用于远程网络启动 /var/www/cobbler/repo_mirror/ #yum 仓库存储目录3.5.4 日志目录
/var/log/cobbler/installing #客户端安装日志 /var/log/cobbler/cobbler.log #cobbler日志3.6 配置及启动cobblerd服务
cobbler check The following are potential configuration items that you may want to fix: 1 : The 'server' field in /etc/cobbler/settings must be set to something other than localhost, or kickstarting features will not work. This should be a resolvable hostname or IP for the boot server as reachable by all machines that will use it. 2 : For PXE to be functional, the 'next_server' field in /etc/cobbler/settings must be set to something other than 127.0.0.1, and should match the IP of the boot server on the PXE network. 3 : change 'disable' to 'no' in /etc/xinetd.d/tftp7.7 cobbler命令用法 4 : Some network boot-loaders are missing from /var/lib/cobbler/loaders, you may run 'cobbler get-loaders' to download them, or, if you only want to handle x86/x86_64 netbooting, you may ensure that you have installed a *recent* version of the syslinux package installed and can ignore this message entirely. Files in this directory, should you want to support all architectures, should include pxelinux.0, menu.c32, elilo.efi, and yaboot. The 'cobbler get-loaders' command is the easiest way to resolve these requirements. 5 : enable and start rsyncd.service with systemctl 6 : debmirror package is not installed, it will be required to manage debian deployments and repositories 7 : ksvalidator was not found, install pykickstart 8 : The default password used by the sample templates for newly installed machines (default_password_crypted in /etc/cobbler/settings) is still set to 'cobbler' and should be changed, try: "openssl passwd -1 -salt 'random-phrasehere' 'your-password-here'" to generate new one 9 : fencing tools were not found, and are required to use the (optional) power management features. install cman or fence-agents to use them Restart cobblerd and then run 'cobbler sync' to apply changes. 1.更改/etc/xinetd.d/tftp配置文件 vim /etc/xinetd.d/tftp disable = yes --> disable = no systemctl restart xinetd 2.联网下载boot引导程序文件 cobbler get-loaders 3.没有网络情况下拷贝启动文件到TFTP服务文件夹 cp -a /usr/share/syslinux/{pxelinux.0,menu.c32} /var/lib/tftpboot 4.更改/etc/cobbler/settings配置文件的server项为提供cobblerd服务的主机地址,也就是本机地址 sed -nri 's#server:127.0.0.1#server:192.168.100.100#' /etc/cobbler/settings 更改后的整行内容:server:192.168.100.100 5.更改/etc/cobbler/settings配置文件的next_server项,指明tftp服务器地址,使得客户端能够找 到TFTP服务器 sed -i 's/next_server: 127.0.0.1/next_server: 192.168.100.100/' /etc/cobbler/settings 更改后的整行内容:next_server:192.168.100.100 6.配置相应的选项来使用cobbler管理dhcp服务和tftp服务 manage_dhcp:1 manage_tftpd:1 7.pxe_just_once选项,该选项置1表示在pxe安装块结束时在cobbler系统中做相应的记录,这样会避免 如果客户机的BIOS选项中PXE启动处于第一位导致的循环重启;如果第一个启动硬件不是PXE启动那就置0。 pxe_just_once:1 配置完成后重启 systemctl restart cobblerd3.7 常见用法
#列出当前导入的linux发行版条目 cobbler distro list #报告当前所有的linux发行版详细信息 cobbler distro report #导入系统源文件生成仓库 cobbler import --name=centos-8.0-x86_64 --path=/mnt --arch=x86_64 #将linux发行版系统镜像与其对应的ks文件建立关联 cobbler profile --name=centos7 --distro=centos7-x86_64 -kickstart=/var/lib/cobbler/kickstarts/ks7.cfg3.8 将linux发行版导入到cobbler在httpd服务的文件夹下
cobbler将系统yum源文件存放在 /var/www/cobbler/ks_mirror目录下
cobbler import --name=centos6 --path=/var/www/html/centos/6/isos/x86_64/ --arch=x86_64 cobbler import --name=centos7 --path=/var/www/html/centos/7/isos/x86_64/ --arch=x86_64 cobbler import --name=centos8 --path=/var/www/html/centos/8/isos/x86_64/ --arch=x86_64 #导入后重启并同步 systemctl restart cobblerd cobbler sync3.9 配置linux发行版和关联相应的ks文件
拷贝事先准备好的ks文件至/var/lib/cobbler/kickstarts目录下
[root@centos7 ~]#cp /var/www/html/ks/centos{6,7,8}.ks /var/lib/cobbler/kickstarts #将linux发行版系统镜像与其对应的ks文件建立关联 cobbler profile --name=centos6 --distro=centos6-x86_64 --kickstart=/var/lib/cobbler/kickstarts/centos6.cfg cobbler profile --name=centos7 --distro=centos7-x86_64 -- kickstart=/var/lib/cobbler/kickstarts/centos7.cfg cobbler profile --name=centos8 --distro=centos8-x86_64 -- kickstart=/var/lib/cobbler/kickstarts/centos8.cfg #注意,在导入distro时,cobbler会自动生成distro条目,这些并未和ks文件关联,可以使用 cobbler profile remove --name=PROFILE_NAME 删除后,再关联ks文件。 #建立关联后重启并同步 systemctl restart cobblerd cobbler sync3.10 CentOS 7 基于cobbler实现系统的自动化安装
3.10.1 环境准备
两台主机一台主机:CentOS 7 充当 Cobbler,http,dhcp,tftp 服务器,并关闭防火墙和SELinux一台主机:充当测试机,用于实现自动化安装Linux系统网络要求:关闭Vmware软件中的NAT模式中的DHCP服务,两个主机网卡基于NAT模式
3.10.2 配置epel仓库源
[root@Centos7 yum.repos.d]#cat Netinstall.repo [Base] name=Netinstall Base baseurl=https://mirrors.tuna.tsinghua.edu.cn/centos/7/os/x86_64/ gpgcheck=1 enabled=1 gpgkey=file:///etc/pki/rpm-gpg/RPM-GPG-KEY-centosofficial [Extras] name=Netinstall Extras baseurl=https://mirrors.tuna.tsinghua.edu.cn/centos/7/extras/x86_64/ gpgcheck=1 enabled=1 gpgkey=file:///etc/pki/rpm-gpg/RPM-GPG-KEY-centosofficial [Epel] name=Netinstall Epel baseurl=https://mirrors.tuna.tsinghua.edu.cn/epel/7/x86_64/ gpgcheck=1 enabled=1 gpgkey=file:///etc/pki/rpm-gpg/RPM-GPG-KEY-EPEL-73.10.3 安装相关包并启动服务
[root@Centos7 ~]#y install cobbler dhcpd [root@Centos7 ~]# enable --now cobblerd httpd tftp dhcpd3.10.4 修改cobbler相关配置
[root@Centos7 ~]#cobbler check The following are potential configuration items that you may want to fix: 1 : The 'server' field in /etc/cobbler/settings must be set to something other than localhost, or kickstarting features will not work. This shesolvable hostname or IP for the boot server as reachable by all machines that will use it. 2 : For PXE to be functional, the 'next_server' field in /etc/cobbler/settings must be set to something other than 127.0.0.1, and should match he boot server on the PXE network. 3 : change 'disable' to 'no' in /etc/xinetd.d/tftp 4 : Some network boot-loaders are missing from /var/lib/cobbler/loaders, you may run 'cobbler get-loaders' to download them, or, if you only wae x86/x86_64 netbooting, you may ensure that you have installed a *recent* version of the syslinux package installed and can ignore this messag Files in this directory, should you want to support all architectures, should include pxelinux.0, menu.c32, elilo.efi, and yaboot. The 'cobblers' command is the easiest way to resolve these requirements. 5 : enable and start rsyncd.service with systemctl 6 : debmirror package is not installed, it will be required to manage debian deployments and repositories 7 : ksvalidator was not found, install pykickstart 8 : The default password used by the sample templates for newly installed machines (default_password_crypted in /etc/cobbler/settings) is stillbbler' and should be changed, try: "openssl passwd -1 -salt 'random-phrase-here' 'your-password-here'" to generate new one 9 : fencing tools were not found, and are required to use the (optional) power management features. install cman or fence-agents to use them Restart cobblerd and then run 'cobbler sync' to apply changes. #生成新密码,默认安装好的系统root密码为cobbler [root@centos7 ~]#openssl passwd -1 'magedu' $1$1spuisnh$j34LNmyTQWs3l6xKxCZY60 #根据以上提示,只需要做1,2,8这三项即可,修改下面四行 [root@centos7 ~]#vim /etc/cobbler/settings default_password_crypted: "$1$1spuisnh$j34LNmyTQWs3l6xKxCZY60" next_server:< tftp服务器的 IP 地址> server:<cobbler服务器的 IP 地址> manage_dhcp:1 #设置为1,表示通过cobbler生成dhcpd.conf配置文件 [root@centos7 ~]#systemctl restart cobblerd3.10.5 配置DHCP服务
#修改cobbler dhcp模板文件,用来生成dhcp的配置文件 [root@Centos7 cobbler]#cat /etc/cobbler/dhcp.template subnet 10.0.0.0 netmask 255.255.255.0 { option routers 10.0.0.2; option domain-name-servers 202.101.224.68,223.6.6.6; option subnet-mask 255.255.255.0; range dynamic-bootp 10.0.0.100 10.0.0.110; [root@Centos7 cobbler]#cobbler sync [root@Centos7 cobbler]#systemctl start dhcpd3.10.6 下载启动的相关文件
[root@Centos7 cobbler]#cobbler get-loaders3.10.7 修改菜单的标题信息(可选)
[root@Centos7 cobbler]#vim /etc/cobbler/pxe/pxedefault.template [root@Centos7 cobbler]#cobbler sync [root@Centos7 cobbler]#cat /etc/cobbler/pxe/pxedefault.template DEFAULT menu PROMPT 0 MENU TITLE Cobbler | http://www.magedu.org/ #默认为:http://cobbler.github.io/ TIMEOUT 200 TOTALTIMEOUT 6000 ONTIMEOUT $pxe_timeout_profile LABEL local MENU LABEL (local) MENU DEFAULT LOCALBOOT -1 $pxe_menu_items MENU end3.10.8 导入Centos系统的安装文件,生成相应的yum源
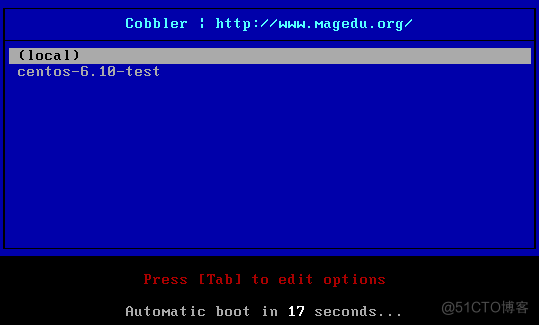
[root@Centos7 ~]#echo '- - -' > /sys/class/scsi_host/host0/scan [root@Centos7 ~]#echo '- - -' > /sys/class/scsi_host/host1/scan [root@Centos7 ~]#echo '- - -' > /sys/class/scsi_host/host2/scan [root@Centos7 ~]#lsblk NAME MAJ:MIN RM SIZE RO TYPE MOUNTPOINT sr0 11:0 1 9.5G 0 rom sr1 11:1 1 3.7G 0 rom [root@Centos7 ~]#mount /dev/sr1 /mnt [root@Centos7 ~]#cobbler import --name=centos-6.10-x86_64 --path=/mnt --arch=x86_64 task started: 2021-06-21_231232_import task started (id=Media import, time=Mon Jun 21 23:12:32 2021) Found a candidate signature: breed=redhat, version=rhel6 Found a matching signature: breed=redhat, version=rhel6 Adding distros from path /var/www/cobbler/ks_mirror/centos-6.10-x86_64: creating new distro: centos-6.10-x86_64 trying symlink: /var/www/cobbler/ks_mirror/centos-6.10-x86_64 -> /var/www/cobbler/links/centos-6.10-x86_64 creating new profile: centos-6.10-x86_64 associating repos checking for rsync repo(s) checking for rhn repo(s) checking for yum repo(s) starting descent into /var/www/cobbler/ks_mirror/centos-6.10-x86_64 for centos-6.10-x86_64 processing repo at : /var/www/cobbler/ks_mirror/centos-6.10-x86_64 need to process repo/comps: /var/www/cobbler/ks_mirror/centos-6.10-x86_64 looking for /var/www/cobbler/ks_mirror/centos-6.10-x86_64/repodata/*comps*.xml Keeping repodata as-is :/var/www/cobbler/ks_mirror/centos-6.10-x86_64/repodata *** TASK COMPLETE *** [root@Centos7 cobbler]#du -sh /var/www/cobbler/ks_mirror/* 3.8G /var/www/cobbler/ks_mirror/centos-6.10-x86_64 4.0K /var/www/cobbler/ks_mirror/config [root@Centos7 cobbler]#cobbler distro list centos-6.10-x86_64 [root@Centos7 cobbler]#cobbler profile list centos-6.10-x86_64 #默认生成的是最小化安装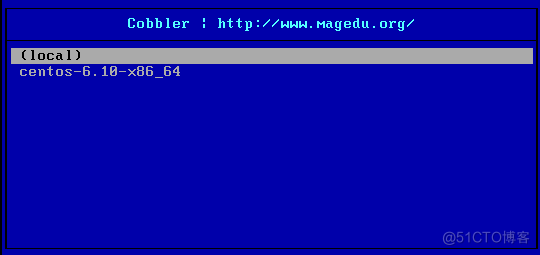
3.10.9 准备kickstart文件,并关联指定的YUM源
[root@Centos7 kickstarts]#vim /var/lib/cobbler/kickstarts/centos6.cfg [root@Centos7 kickstarts]#cat /var/lib/cobbler/kickstarts/centos6.cfg install text reboot url --url=$tree lang en_US.UTF-8 keyboard us network --onboot yes --device eth0 --bootproto dhcp --noipv6 rootpw --iscrypted $6$j9YhzDUnQVnxaAk8$qv7rkMcPAEbV5yvwsP666DXWYadd3jYjkA9fpxAo9qYotjGGBUclCGoP1TRvgHBpqgc5n0RypMsPTQnVDcpO01 firewall --disabled authconfig --enableshadow --passalgo=sha512 selinux --disabled timezone Asia/Shanghai bootloader --location=mbr --driveorder=sda --append="crashkernel=auto rhgb quiet" zerombr clearpart --all --initlabel part /boot --fstype=ext4 --size=1024 part / --fstype=ext4 --size=50000 part /data --fstype=ext4 --size=30000 part swap --size=2048 %packages @core @server-policy @workstation-policy autofs vim-enhanced %end %post useradd wang echo magedu | passwd --stdin wang &> /dev/null mkdir /etc/yum.repos.d/bak mv /etc/yum.repos.d/* /etc/yum.repos.d/bak cat > /etc/yum.repos.d/base.repo <<EOF [base] name=base baseurl=file:///misc/cd gpgcheck=0 EOF %end #关联kickstart文件,关联指定的yum源和生成菜单列表 [root@Centos7 kickstarts]#cobbler profile add --name=centos-6.10-test --distro=centos-6.10-x86_64 --kickstart=/var/lib/cobbler/kickstarts/centos6.cfg #删除默认生成的菜单 [root@Centos7 kickstarts]#cobbler profile remove --name=centos-6.10-x86_64 [root@Centos7 kickstarts]#cobbler profile list centos-6.10-test3.10.10 测试客户端基于cobbler实现自动安装