一、概述
Openssh作为一个非常流行的安全远程服务器,也备受黑客照顾,每隔一段时间会爆出问题,但是Centos7已经处于停服的边缘,也没有提供新版的yum源直接安装的方式,只能采用编译的方式安装,但是对于编译的方式可移植性较为复杂,需要能够提供编译环境和需要耗费很长的时间,所以想要做一个RPM包的方式来方便升级和管理。网上很多都是使用官方SYSV的方式来实现启动。本次使用systemd的Unit管理方式来实现。
二、实践过程
1、准备封包环境
在普通用户家目录执行创建目录和安装对应包。
mkdir -p rpmbuild/{SOURCES,RPMS,SPECS,BUILD,BUILDROOT,SRPMS} sudo yum install -y gcc make perl rpm-build rpmlint perl-WWW-Curl libXt-devel imake \ gtk2-devel krb5-devel pam-devel2、准备源码包
目前官网的最新版版本就是9.0p1版本。https://ftp.openbsd.org/pub/OpenBSD/OpenSSH/openssh-9.0.tar.gz 下载需要依赖的x11-askpass软件包https://src.fedoraproject.org/repo/pkgs/openssh/x11-ssh-askpass-1.2.4.1.tar.gz/8f2e41f3f7eaa8543a2440454637f3c3/x11-ssh-askpass-1.2.4.1.tar.gz下载依赖的pam包http://prdownloads.sourceforge.net/pamsshagentauth/pam_ssh_agent_auth/pam_ssh_agent_auth-0.10.3.tar.bz2
下载需要依赖的x11-askpass软件包https://src.fedoraproject.org/repo/pkgs/openssh/x11-ssh-askpass-1.2.4.1.tar.gz/8f2e41f3f7eaa8543a2440454637f3c3/x11-ssh-askpass-1.2.4.1.tar.gz下载依赖的pam包http://prdownloads.sourceforge.net/pamsshagentauth/pam_ssh_agent_auth/pam_ssh_agent_auth-0.10.3.tar.bz2
3、上传两个源码包到SOURCES目录中
同时在SOURCES目录下创建SPEC文件需要的几个文件
cat <<EOF > sshd.service [Unit] Description=OpenSSH server daemon Documentation=man:sshd(8) man:sshd_config(5) After=network.target sshd-keygen.service Wants=sshd-keygen.service [Service] Type=simple EnvironmentFile=/etc/sysconfig/sshd ExecStart=/usr/sbin/sshd -D $OPTIONS ExecReload=/bin/kill -HUP $MAINPID KillMode=process Restart=on-failure RestartSec=42s [Install] WantedBy=multi-user.target EOF cat <<EOF > sshd-keygen.service [Unit] Description=OpenSSH Server Key Generation ConditionFileNotEmpty=|!/etc/ssh/ssh_host_rsa_key ConditionFileNotEmpty=|!/etc/ssh/ssh_host_ecdsa_key ConditionFileNotEmpty=|!/etc/ssh/ssh_host_ed25519_key PartOf=sshd.service sshd.socket [Service] ExecStart=/usr/sbin/sshd-keygen Type=oneshot RemainAfterExit=yes EOF cat <<EOF > sshd@.service [Unit] Description=OpenSSH per-connection server daemon Documentation=man:sshd(8) man:sshd_config(5) Wants=sshd-keygen.service After=sshd-keygen.service [Service] EnvironmentFile=-/etc/sysconfig/sshd ExecStart=-/usr/sbin/sshd -i $OPTIONS StandardInput=socket cat <<EOF > sshd.socket [Unit] Description=OpenSSH Server Socket Documentation=man:sshd(8) man:sshd_config(5) Conflicts=sshd.service [Socket] ListenStream=22 Accept=yes [Install] WantedBy=sockets.target EOF下面的文件较大,如果不能使用cat添加成功,可以复制后使用vi粘贴写入。
cat <<EOF > sshd-keygen #!/bin/bash # Create the host keys for the OpenSSH server. # # The creation is controlled by the $AUTOCREATE_SERVER_KEYS environment # variable. AUTOCREATE_SERVER_KEYS="RSA ECDSA ED25519" # source function library . /etc/rc.d/init.d/functions # Some functions to make the below more readable KEYGEN=/usr/bin/ssh-keygen RSA1_KEY=/etc/ssh/ssh_host_key RSA_KEY=/etc/ssh/ssh_host_rsa_key DSA_KEY=/etc/ssh/ssh_host_dsa_key ECDSA_KEY=/etc/ssh/ssh_host_ecdsa_key ED25519_KEY=/etc/ssh/ssh_host_ed25519_key # pull in sysconfig settings [ -f /etc/sysconfig/sshd ] && . /etc/sysconfig/sshd fips_enabled() { if [ -r /proc/sys/crypto/fips_enabled ]; then cat /proc/sys/crypto/fips_enabled else echo 0 fi } do_rsa1_keygen() { if [ ! -s $RSA1_KEY -a `fips_enabled` -eq 0 ]; then echo -n $"Generating SSH1 RSA host key: " rm -f $RSA1_KEY if test ! -f $RSA1_KEY && $KEYGEN -q -t rsa1 -f $RSA1_KEY -C '' -N '' >&/dev/null; then chgrp ssh_keys $RSA1_KEY chmod 640 $RSA1_KEY chmod 644 $RSA1_KEY.pub if [ -x /sbin/restorecon ]; then /sbin/restorecon $RSA1_KEY{,.pub} fi success $"RSA1 key generation" echo else failure $"RSA1 key generation" echo exit 1 fi fi } do_rsa_keygen() { if [ ! -s $RSA_KEY ]; then echo -n $"Generating SSH2 RSA host key: " rm -f $RSA_KEY if test ! -f $RSA_KEY && $KEYGEN -q -t rsa -f $RSA_KEY -C '' -N '' >&/dev/null; then chgrp ssh_keys $RSA_KEY chmod 640 $RSA_KEY chmod 644 $RSA_KEY.pub if [ -x /sbin/restorecon ]; then /sbin/restorecon $RSA_KEY{,.pub} fi success $"RSA key generation" echo else failure $"RSA key generation" echo exit 1 fi fi } do_dsa_keygen() { if [ ! -s $DSA_KEY -a `fips_enabled` -eq 0 ]; then echo -n $"Generating SSH2 DSA host key: " rm -f $DSA_KEY if test ! -f $DSA_KEY && $KEYGEN -q -t dsa -f $DSA_KEY -C '' -N '' >&/dev/null; then chgrp ssh_keys $DSA_KEY chmod 640 $DSA_KEY chmod 644 $DSA_KEY.pub if [ -x /sbin/restorecon ]; then /sbin/restorecon $DSA_KEY{,.pub} fi success $"DSA key generation" echo else failure $"DSA key generation" echo exit 1 fi fi } do_ecdsa_keygen() { if [ ! -s $ECDSA_KEY ]; then echo -n $"Generating SSH2 ECDSA host key: " rm -f $ECDSA_KEY if test ! -f $ECDSA_KEY && $KEYGEN -q -t ecdsa -f $ECDSA_KEY -C '' -N '' >&/dev/null; then chgrp ssh_keys $ECDSA_KEY chmod 640 $ECDSA_KEY chmod 644 $ECDSA_KEY.pub if [ -x /sbin/restorecon ]; then /sbin/restorecon $ECDSA_KEY{,.pub} fi success $"ECDSA key generation" echo else failure $"ECDSA key generation" echo exit 1 fi fi } do_ed25519_keygen() { if [ ! -s $ED25519_KEY -a `fips_enabled` -eq 0 ]; then echo -n $"Generating SSH2 ED25519 host key: " rm -f $ED25519_KEY if test ! -f $ED25519_KEY && $KEYGEN -q -t ed25519 -f $ED25519_KEY -C '' -N '' >&/dev/null; then chgrp ssh_keys $ED25519_KEY chmod 640 $ED25519_KEY chmod 644 $ED25519_KEY.pub if [ -x /sbin/restorecon ]; then /sbin/restorecon $ED25519_KEY{,.pub} fi success $"ED25519 key generation" echo else failure $"ED25519 key generation" echo exit 1 fi fi } if [ "x${AUTOCREATE_SERVER_KEYS}" == "xNO" ]; then exit 0 fi # legacy options case $AUTOCREATE_SERVER_KEYS in NODSA) AUTOCREATE_SERVER_KEYS="RSA ECDSA ED25519";; RSAONLY) AUTOCREATE_SERVER_KEYS="RSA";; YES) AUTOCREATE_SERVER_KEYS="DSA RSA ECDSA ED25519";; esac for KEY in $AUTOCREATE_SERVER_KEYS; do case $KEY in DSA) do_dsa_keygen;; RSA) do_rsa_keygen;; ECDSA) do_ecdsa_keygen;; ED25519) do_ed25519_keygen;; esac done EOF cat <<EOF >sshd.sysconfig # Configuration file for the sshd service. # The server keys are automatically generated if they are missing. # To change the automatic creation uncomment and change the appropriate # line. Accepted key types are: DSA RSA ECDSA ED25519. # The default is "RSA ECDSA ED25519" # AUTOCREATE_SERVER_KEYS="" # AUTOCREATE_SERVER_KEYS="RSA ECDSA ED25519" # Do not change this option unless you have hardware random # generator and you REALLY know what you are doing SSH_USE_STRONG_RNG=0 # SSH_USE_STRONG_RNG=1 EOF cat <<EOF > sshd.pam #%PAM-1.0 auth required pam_sepermit.so auth substack password-auth auth include postlogin # Used with polkit to reauthorize users in remote sessions -auth optional pam_reauthorize.so prepare account required pam_nologin.so account include password-auth password include password-auth # pam_selinux.so close should be the first session rule session required pam_selinux.so close session required pam_loginuid.so # pam_selinux.so open should only be followed by sessions to be executed in the user context session required pam_selinux.so open env_params session required pam_namespace.so session optional pam_keyinit.so force revoke session include password-auth session include postlogin # Used with polkit to reauthorize users in remote sessions -session optional pam_reauthorize.so prepare EOF cat <<EOF > sshd@.service [Unit] Description=OpenSSH per-connection server daemon Documentation=man:sshd(8) man:sshd_config(5) Wants=sshd-keygen.service After=sshd-keygen.service [Service] EnvironmentFile=-/etc/sysconfig/sshd ExecStart=-/usr/sbin/sshd -i $OPTIONS StandardInput=socket EOF cat <<EOF > pam_ssh_agent-rmheaders authfd.c authfd.h atomicio.c atomicio.h bufaux.c bufbn.c buffer.h buffer.c cleanup.c cipher.h compat.h defines.h entropy.c entropy.h fatal.c includes.h kex.h key.c key.h log.c log.h match.h misc.c misc.h pathnames.h platform.h rsa.h ssh-dss.c ssh-rsa.c ssh.h ssh2.h uidswap.c uidswap.h uuencode.c uuencode.h xmalloc.c xmalloc.h EOF完成所有软件包上传和写入后如下图所示: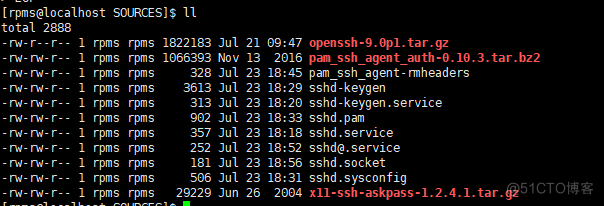
4、上传spec文件,使用rpmbuild制作RPM包
openssh的SPEC文件举例
%global ver 9.0p1 %global rel 1%{?dist} # OpenSSH privilege separation requires a user & group ID %global sshd_uid 74 %global sshd_gid 74 # Version of ssh-askpass %global aversion 1.2.4.1 # Do we want to disable building of x11-askpass? (1=yes 0=no) %global no_x11_askpass 0 # Do we want to disable building of gnome-askpass? (1=yes 0=no) %global no_gnome_askpass 0 # Do we want to link against a static libcrypto? (1=yes 0=no) %global static_libcrypto 0 # Do we want smartcard support (1=yes 0=no) %global scard 0 # Use GTK2 instead of GNOME in gnome-ssh-askpass %global gtk2 1 # Use build6x options for older RHEL builds # RHEL 7 not yet supported %if 0%{?rhel} > 6 %global build6x 0 %else %global build6x 1 %endif %if 0%{?fedora} >= 26 %global compat_openssl 1 %else %global compat_openssl 0 %endif # Do we want kerberos5 support (1=yes 0=no) %global kerberos5 1 # Reserve options to override askpass settings with: # rpm -ba|--rebuild --define 'skip_xxx 1' %{?skip_x11_askpass:%global no_x11_askpass 1} %{?skip_gnome_askpass:%global no_gnome_askpass 1} # Add option to build without GTK2 for older platforms with only GTK+. # RedHat <= 7.2 and Red Hat Advanced Server 2.1 are examples. # rpm -ba|--rebuild --define 'no_gtk2 1' %{?no_gtk2:%global gtk2 0} # Is this a build for RHL 6.x or earlier? %{?build_6x:%global build6x 1} # If this is RHL 6.x, the default configuration has sysconfdir in /usr/etc. %if %{build6x} %global _sysconfdir /etc %endif # Options for static OpenSSL link: # rpm -ba|--rebuild --define "static_openssl 1" %{?static_openssl:%global static_libcrypto 1} # Options for Smartcard support: (needs libsectok and openssl-engine) # rpm -ba|--rebuild --define "smartcard 1" %{?smartcard:%global scard 1} # Is this a build for the rescue CD (without PAM)? (1=yes 0=no) %global rescue 0 %{?build_rescue:%global rescue 1} # Turn off some stuff for resuce builds %if %{rescue} %global kerberos5 0 %endif %define pam_ssh_agent_ver 0.10.3 Summary: The OpenSSH implementation of SSH protocol version 2. Name: openssh Version: %{ver} %if %{rescue} Release: %{rel}rescue %else Release: %{rel} %endif URL: https://www.openssh.com/portable.html Source0: https://ftp.openbsd.org/pub/OpenBSD/OpenSSH/portable/openssh-%{version}.tar.gz Source1: http://www.jmknoble.net/software/x11-ssh-askpass/x11-ssh-askpass-%{aversion}.tar.gz Source2: sshd.pam #Source3: sshd.init Source4: http://prdownloads.sourceforge.net/pamsshagentauth/pam_ssh_agent_auth/pam_ssh_agent_auth-%{pam_ssh_agent_ver}.tar.bz2 Source5: pam_ssh_agent-rmheaders #Source6: ssh-keycat.pam Source7: sshd.sysconfig Source9: sshd@.service Source10: sshd.socket Source11: sshd.service Source12: sshd-keygen.service Source13: sshd-keygen License: BSD Group: Applications/Internet BuildRoot: %{_tmppath}/%{name}-%{version}-buildroot Obsoletes: ssh %if %{build6x} PreReq: initscripts >= 5.00 %else Requires: initscripts >= 5.20 %endif BuildRequires: perl %if %{compat_openssl} BuildRequires: compat-openssl10-devel %else BuildRequires: openssl-devel >= 1.0.1 #BuildRequires: openssl-devel < 1.2 %endif BuildRequires: /bin/login %if ! %{build6x} BuildRequires: glibc-devel, pam %else BuildRequires: /usr/include/security/pam_appl.h %endif %if ! %{no_x11_askpass} BuildRequires: /usr/include/X11/Xlib.h # Xt development tools BuildRequires: libXt-devel # Provides xmkmf BuildRequires: imake # Rely on relatively recent gtk BuildRequires: gtk2-devel %endif %if ! %{no_gnome_askpass} BuildRequires: pkgconfig %endif %if %{kerberos5} BuildRequires: krb5-devel BuildRequires: krb5-libs %endif %package clients Summary: OpenSSH clients. Requires: openssh = %{version}-%{release} Group: Applications/Internet Obsoletes: ssh-clients %package server Summary: The OpenSSH server daemon. Group: System Environment/Daemons Obsoletes: ssh-server Requires: openssh = %{version}-%{release}, chkconfig >= 0.9 %if ! %{build6x} Requires: /etc/pam.d/system-auth %endif %package askpass Summary: A passphrase dialog for OpenSSH and X. Group: Applications/Internet Requires: openssh = %{version}-%{release} Obsoletes: ssh-extras %package askpass-gnome Summary: A passphrase dialog for OpenSSH, X, and GNOME. Group: Applications/Internet Requires: openssh = %{version}-%{release} Obsoletes: ssh-extras %description SSH (Secure SHell) is a program for logging into and executing commands on a remote machine. SSH is intended to replace rlogin and rsh, and to provide secure encrypted communications between two untrusted hosts over an insecure network. X11 connections and arbitrary TCP/IP ports can also be forwarded over the secure channel. OpenSSH is OpenBSD's version of the last free version of SSH, bringing it up to date in terms of security and features, as well as removing all patented algorithms to separate libraries. This package includes the core files necessary for both the OpenSSH client and server. To make this package useful, you should also install openssh-clients, openssh-server, or both. %description clients OpenSSH is a free version of SSH (Secure SHell), a program for logging into and executing commands on a remote machine. This package includes the clients necessary to make encrypted connections to SSH servers. You'll also need to install the openssh package on OpenSSH clients. %description server OpenSSH is a free version of SSH (Secure SHell), a program for logging into and executing commands on a remote machine. This package contains the secure shell daemon (sshd). The sshd daemon allows SSH clients to securely connect to your SSH server. You also need to have the openssh package installed. %description askpass OpenSSH is a free version of SSH (Secure SHell), a program for logging into and executing commands on a remote machine. This package contains an X11 passphrase dialog for OpenSSH. %description askpass-gnome OpenSSH is a free version of SSH (Secure SHell), a program for logging into and executing commands on a remote machine. This package contains an X11 passphrase dialog for OpenSSH and the GNOME GUI desktop environment. %prep %if ! %{no_x11_askpass} %setup -q -a 1 %else %setup -q %endif %build %if %{rescue} CFLAGS="$RPM_OPT_FLAGS -Os"; export CFLAGS %endif %configure \ --sysconfdir=%{_sysconfdir}/ssh \ --libexecdir=%{_libexecdir}/openssh \ --datadir=%{_datadir}/openssh \ --with-default-path=/usr/local/bin:/bin:/usr/bin \ --with-superuser-path=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin \ --with-privsep-path=%{_var}/empty/sshd \ --mandir=%{_mandir} \ --with-ssl-dir=/usr/openssl \ --with-mantype=man \ --disable-strip \ %if %{scard} --with-smartcard \ %endif %if %{rescue} --without-pam \ %else --with-pam \ %endif %if %{kerberos5} --with-kerberos5=$K5DIR \ %endif %if %{static_libcrypto} perl -pi -e "s|-lcrypto|%{_libdir}/libcrypto.a|g" Makefile %endif make %if ! %{no_x11_askpass} pushd x11-ssh-askpass-%{aversion} %configure --libexecdir=%{_libexecdir}/openssh xmkmf -a make popd %endif # Define a variable to toggle gnome1/gtk2 building. This is necessary # because RPM doesn't handle nested %if statements. %if %{gtk2} gtk2=yes %else gtk2=no %endif %if ! %{no_gnome_askpass} pushd contrib if [ $gtk2 = yes ] ; then make gnome-ssh-askpass2 mv gnome-ssh-askpass2 gnome-ssh-askpass else make gnome-ssh-askpass1 mv gnome-ssh-askpass1 gnome-ssh-askpass fi popd %endif %install rm -rf $RPM_BUILD_ROOT mkdir -p -m755 $RPM_BUILD_ROOT%{_sysconfdir}/ssh mkdir -p -m755 $RPM_BUILD_ROOT%{_libexecdir}/openssh mkdir -p -m755 $RPM_BUILD_ROOT%{_var}/empty/sshd make install DESTDIR=$RPM_BUILD_ROOT install -d $RPM_BUILD_ROOT/etc/pam.d/ install -d $RPM_BUILD_ROOT/etc/rc.d/init.d install -d $RPM_BUILD_ROOT/etc/sysconfig install -d $RPM_BUILD_ROOT%{_libexecdir}/openssh install -m644 %{SOURCE2} $RPM_BUILD_ROOT/etc/pam.d/sshd #install -m644 %{SOURCE6} $RPM_BUILD_ROOT/etc/pam.d/ssh-keycat #install -m755 %{SOURCE3} $RPM_BUILD_ROOT/etc/rc.d/init.d/sshd install -m644 %{SOURCE7} $RPM_BUILD_ROOT/etc/sysconfig/sshd install -m755 %{SOURCE13} $RPM_BUILD_ROOT/%{_sbindir}/sshd-keygen %if %{build6x} install -m644 contrib/redhat/sshd.pam.old $RPM_BUILD_ROOT/etc/pam.d/sshd %else install -m644 %{SOURCE2} $RPM_BUILD_ROOT/etc/pam.d/sshd %endif install -d -m755 $RPM_BUILD_ROOT/%{_unitdir} install -m644 %{SOURCE9} $RPM_BUILD_ROOT/%{_unitdir}/sshd@.service install -m644 %{SOURCE10} $RPM_BUILD_ROOT/%{_unitdir}/sshd.socket install -m644 %{SOURCE11} $RPM_BUILD_ROOT/%{_unitdir}/sshd.service install -m644 %{SOURCE12} $RPM_BUILD_ROOT/%{_unitdir}/sshd-keygen.service install -m755 contrib/ssh-copy-id $RPM_BUILD_ROOT%{_bindir}/ install contrib/ssh-copy-id.1 $RPM_BUILD_ROOT%{_mandir}/man1/ %if ! %{no_x11_askpass} install x11-ssh-askpass-%{aversion}/x11-ssh-askpass $RPM_BUILD_ROOT%{_libexecdir}/openssh/x11-ssh-askpass ln -s x11-ssh-askpass $RPM_BUILD_ROOT%{_libexecdir}/openssh/ssh-askpass %endif %if ! %{no_gnome_askpass} install contrib/gnome-ssh-askpass $RPM_BUILD_ROOT%{_libexecdir}/openssh/gnome-ssh-askpass %endif %if ! %{scard} rm -f $RPM_BUILD_ROOT/usr/share/openssh/Ssh.bin %endif %if ! %{no_gnome_askpass} install -m 755 -d $RPM_BUILD_ROOT%{_sysconfdir}/profile.d/ install -m 755 contrib/redhat/gnome-ssh-askpass.csh $RPM_BUILD_ROOT%{_sysconfdir}/profile.d/ install -m 755 contrib/redhat/gnome-ssh-askpass.sh $RPM_BUILD_ROOT%{_sysconfdir}/profile.d/ %endif perl -pi -e "s|$RPM_BUILD_ROOT||g" $RPM_BUILD_ROOT%{_mandir}/man*/* %clean rm -rf $RPM_BUILD_ROOT %pre getent group ssh_keys >/dev/null || groupadd -r ssh_keys || : %pre server getent group sshd >/dev/null || groupadd -g %{sshd_uid} -r sshd || : getent passwd sshd >/dev/null || \ useradd -c "Privilege-separated SSH" -u %{sshd_uid} -g sshd \ -s /sbin/nologin -r -d /var/empty/sshd sshd 2> /dev/null || : rm -rf %{_sysconfdir}/ssh/ssh_host* /bin/ssh-keygen -A %post server %systemd_post sshd.service sshd.socket sed -i 's/#UsePAM no/UsePAM\ yes/g' /etc/ssh/sshd_config sed -i 's/#PermitRootLogin prohibit-password/PermitRootLogin\ yes/g' /etc/ssh/sshd_config sed -i 's/#PermitEmptyPasswords\(.*\)/PermitEmptyPasswords\ no/g' /etc/ssh/sshd_config echo 'KexAlgorithms curve25519-sha256@libssh.org,ecdh-sha2-nistp256,ecdh-sha2-nistp384,ecdh-sha2-nistp521,diffie-hellman-group-exchange-sha256,diffie-hellman-group14-sha1,diffie-hellman-group-exchange-sha1,diffie-hellman-group1-sha1' >> /etc/ssh/sshd_config systemctl daemon-reload systemctl restart sshd %preun server %systemd_preun sshd.service sshd.socket %postun server %systemd_postun_with_restart sshd.service %files %defattr(-,root,root) %doc CREDITS ChangeLog INSTALL LICENCE OVERVIEW README* PROTOCOL* TODO %attr(0755,root,root) %{_bindir}/scp %attr(0644,root,root) %{_mandir}/man1/scp.1* %attr(0755,root,root) %dir %{_sysconfdir}/ssh %attr(0600,root,root) %config(noreplace) %{_sysconfdir}/ssh/moduli %if ! %{rescue} %attr(0755,root,root) %{_bindir}/ssh-keygen %attr(0644,root,root) %{_mandir}/man1/ssh-keygen.1* %attr(0755,root,root) %dir %{_libexecdir}/openssh %attr(4711,root,root) %{_libexecdir}/openssh/ssh-keysign %attr(0755,root,root) %{_libexecdir}/openssh/ssh-pkcs11-helper %attr(0755,root,root) %{_libexecdir}/openssh/ssh-sk-helper %attr(0755,root,root) %{_bindir}/ssh-copy-id %attr(0644,root,root) %{_mandir}/man8/ssh-keysign.8* %attr(0644,root,root) %{_mandir}/man8/ssh-pkcs11-helper.8* %attr(0644,root,root) %{_mandir}/man8/ssh-sk-helper.8* %attr(0644,root,root) %{_mandir}/man1/ssh-copy-id.1* %endif %if %{scard} %attr(0755,root,root) %dir %{_datadir}/openssh %attr(0644,root,root) %{_datadir}/openssh/Ssh.bin %endif %files clients %defattr(-,root,root) %attr(0755,root,root) %{_bindir}/ssh %attr(0644,root,root) %{_mandir}/man1/ssh.1* %attr(0644,root,root) %{_mandir}/man5/ssh_config.5* %attr(0644,root,root) %config(noreplace) %{_sysconfdir}/ssh/ssh_config %if ! %{rescue} %attr(2755,root,nobody) %{_bindir}/ssh-agent %attr(0755,root,root) %{_bindir}/ssh-add %attr(0755,root,root) %{_bindir}/ssh-keyscan %attr(0755,root,root) %{_bindir}/sftp %attr(0644,root,root) %{_mandir}/man1/ssh-agent.1* %attr(0644,root,root) %{_mandir}/man1/ssh-add.1* %attr(0644,root,root) %{_mandir}/man1/ssh-keyscan.1* %attr(0644,root,root) %{_mandir}/man1/sftp.1* %endif %if ! %{rescue} %files server %defattr(-,root,root) %dir %attr(0111,root,root) %{_var}/empty/sshd %attr(0755,root,root) %{_sbindir}/sshd %attr(0755,root,root) %{_sbindir}/sshd-keygen %attr(0755,root,root) %{_libexecdir}/openssh/sftp-server %attr(0644,root,root) %{_mandir}/man8/sshd.8* %attr(0644,root,root) %{_mandir}/man5/moduli.5* %attr(0644,root,root) %{_mandir}/man5/sshd_config.5* %attr(0644,root,root) %{_mandir}/man8/sftp-server.8* %attr(0755,root,root) %dir %{_sysconfdir}/ssh #%attr(0755,root,root) %{_libexecdir}/openssh/ssh-keycat #%attr(0644,root,root) %config(noreplace) /etc/pam.d/ssh-keycat %attr(0600,root,root) %config(noreplace) %{_sysconfdir}/ssh/sshd_config %attr(0600,root,root) %config(noreplace) /etc/pam.d/sshd %attr(0640,root,root) %config(noreplace) /etc/sysconfig/sshd %attr(0644,root,root) %{_unitdir}/sshd.service %attr(0644,root,root) %{_unitdir}/sshd@.service %attr(0644,root,root) %{_unitdir}/sshd.socket %attr(0644,root,root) %{_unitdir}/sshd-keygen.service %endif %if ! %{no_x11_askpass} %files askpass %defattr(-,root,root) %doc x11-ssh-askpass-%{aversion}/README %doc x11-ssh-askpass-%{aversion}/ChangeLog %doc x11-ssh-askpass-%{aversion}/SshAskpass*.ad %{_libexecdir}/openssh/ssh-askpass %attr(0755,root,root) %{_libexecdir}/openssh/x11-ssh-askpass %endif %if ! %{no_gnome_askpass} %files askpass-gnome %defattr(-,root,root) %attr(0755,root,root) %config %{_sysconfdir}/profile.d/gnome-ssh-askpass.* %attr(0755,root,root) %{_libexecdir}/openssh/gnome-ssh-askpass %endif %changelog * Sat Jul 23 2022 Ting - 9.0p1 - Update /etc/pam.d/sshd执行生成命令
rpmbuild -ba openssh5.spec 查看生成软件包
查看生成软件包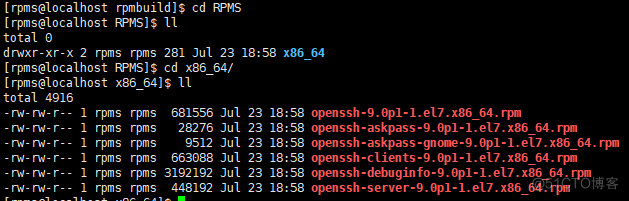
5、使用rpm包升级openssh
使用这三个包进行升级
-rw-rw-r-- 1 rpms rpms 681556 Jul 23 18:58 openssh-9.0p1-1.el7.x86_64.rpm -rw-rw-r-- 1 rpms rpms 663088 Jul 23 18:58 openssh-clients-9.0p1-1.el7.x86_64.rpm -rw-rw-r-- 1 rpms rpms 448192 Jul 23 18:58 openssh-server-9.0p1-1.el7.x86_64.rpm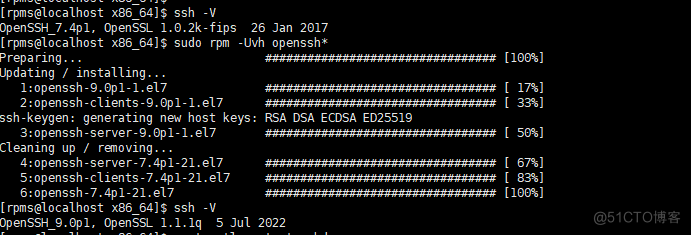 升级完成后确认服务状态
升级完成后确认服务状态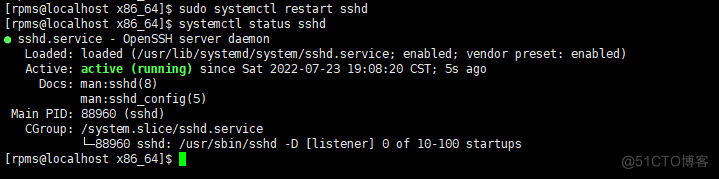
三、总结
通过以上的操作可以完成openssh的软件包制作,特别是在Unit文件的默认会卡在systemd响应上,此处只能换成simple模式来规避这个问题。在制作RPM包时最好先升级openssl。本环境是已经升级了openssl的。
