1、提前准备好docker环境 安装好openssl 后面使用 yum install openssl openssl-devel -y 2、下载harbor包 并解压 我这边直接官网找到 2.7.0比较新的版本 https://github.com/goharbor/harbor/releases/tag/v2.7.
1、提前准备好docker环境
安装好openssl 后面使用
yum install openssl openssl-devel -y
2、下载harbor包 并解压
我这边直接官网找到 2.7.0比较新的版本
https://github.com/goharbor/harbor/releases/tag/v2.7.0
操作命令
wget "https://github.com/goharbor/harbor/releases/download/v2.7.0/harbor-offline-installer-v2.7.0.tgz"
# 若是下载慢,直接电脑下载后上传到服务器。
tar xvf harbor-offline-installer-v2.7.0.tgz -C /usr/local/
cd /usr/local/harbor/
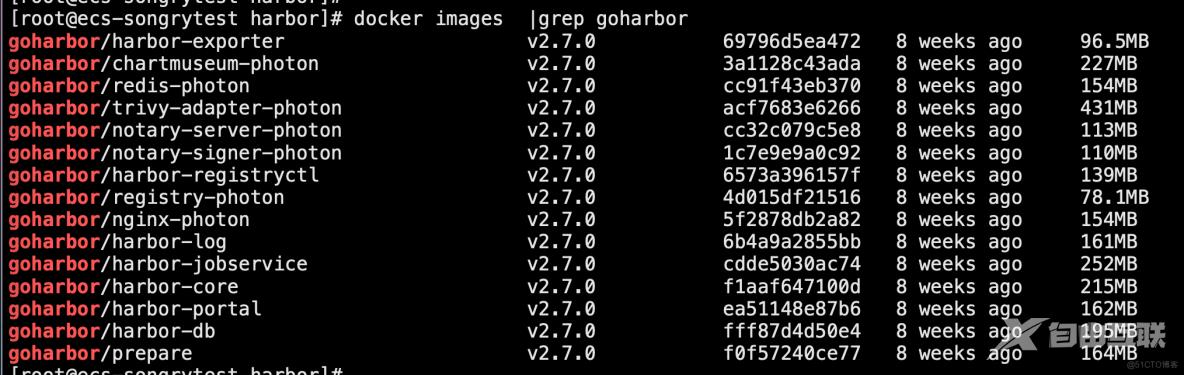
3、加载镜像
加载镜像
[root@localhost harbor]# docker load <harbor.v2.7.0.tar.gz
4、生成ca证书
# mkdir /opt/ssl
# cd /opt/ssl
# pwd #当前目录:/opt/ssl
[root@ecs-songrytest /opt/ssl]# openssl genrsa -out ca.key 4096
[root@ecs-songrytest /opt/ssl]# openssl req -x509 -new -nodes -sha512 -days 36500 \
-subj "/C=CN/ST=ShangHai/L=ShangHai/O=Oldboy/OU=Linux/CN=192.168.0.3" \
-key ca.key \
-out ca.crt
#### 上述 ip换成自己的ip
# O代表组织
# OU代表组织别名
# CN代表域名,没有的可以用IP
5、生成服务器端证书
ssl]# openssl genrsa -out 192.168.0.3.key 4096
ssl]# openssl req -sha512 -new \
-subj "/C=CN/ST=ShangHai/L=ShangHai/O=Oldboy/OU=Linux/CN=192.168.0.3" \
-key 192.168.0.3.key \
-out 192.168.0.3.csr
6、生成x509 v3服务文件
# cat > v3.ext <<-EOF
authorityKeyIdentifier=keyid,issuer
basicConstraints=CA:FALSE
keyUsage = digitalSignature, nonRepudiation, keyEncipherment, dataEncipherment
extendedKeyUsage = serverAuth
subjectAltName = IP:192.168.0.3
EOF
7、使用该v3.ext文件为您的 Harbor 主机生成证书。
将192.168.0.3 CRS 和 CRT 文件名中的 替换为 Harbor 主机名
openssl x509 -req -sha512 -days 36500 \
-extfile v3.ext \
-CA ca.crt -CAkey ca.key -CAcreateserial \
-in 192.168.0.3.csr \
-out 192.168.0.3.crt
8、将192.168.0.3.csr转换成192.168.0.3.cert,给予docker使用
openssl x509 -inform PEM -in 192.168.0.3.crt -out 192.168.0.3.cert
9、创建docker证书存放目录
ssl]# mkdir -p /etc/docker/certs.d/192.168.0.3
ssl]# cp 192.168.0.3.key /etc/docker/certs.d/192.168.0.3/
ssl]# cp 192.168.0.3.cert /etc/docker/certs.d/192.168.0.3/
ssl]# cp ca.crt /etc/docker/certs.d/192.168.0.3/
ssl]# systemctl restart docker
[root@ecs-songrytest ssl]# ll
total 32
-rw-r--r-- 1 root root 2061 Feb 12 18:31 192.168.0.3.cert
-rw-r--r-- 1 root root 2061 Feb 12 18:30 192.168.0.3.crt
-rw-r--r-- 1 root root 1700 Feb 12 18:28 192.168.0.3.csr
-rw------- 1 root root 3243 Feb 12 18:27 192.168.0.3.key
-rw-r--r-- 1 root root 2049 Feb 12 18:22 ca.crt
-rw------- 1 root root 3243 Feb 12 18:19 ca.key
-rw-r--r-- 1 root root 41 Feb 12 18:30 ca.srl
-rw------- 1 root root 0 Feb 12 18:25 privkey.pem
-rw-r--r-- 1 root root 203 Feb 12 18:29 v3.ext
[root@ecs-songrytest ssl]# ll /etc/docker/certs.d/192.168.0.3/
total 12
-rw-r--r-- 1 root root 2061 Feb 12 18:32 192.168.0.3.cert
-rw------- 1 root root 3243 Feb 12 18:32 192.168.0.3.key
-rw-r--r-- 1 root root 2049 Feb 12 18:32 ca.crt
10、修改Harbor的配置文件
harbor]# pwd
/usr/local/harbor
[root@localhost harbor]# cp harbor.yml.tmpl harbor.yml
[root@localhost harbor]# vim harbor.yml
hostname: 192.168.0.3
port: 80 ##后面网站使用此端口
https:
# https port for harbor, default is 443
port: 443
certificate: /opt/ssl/192.168.0.3.crt
private_key: /opt/ssl/192.168.0.3.key
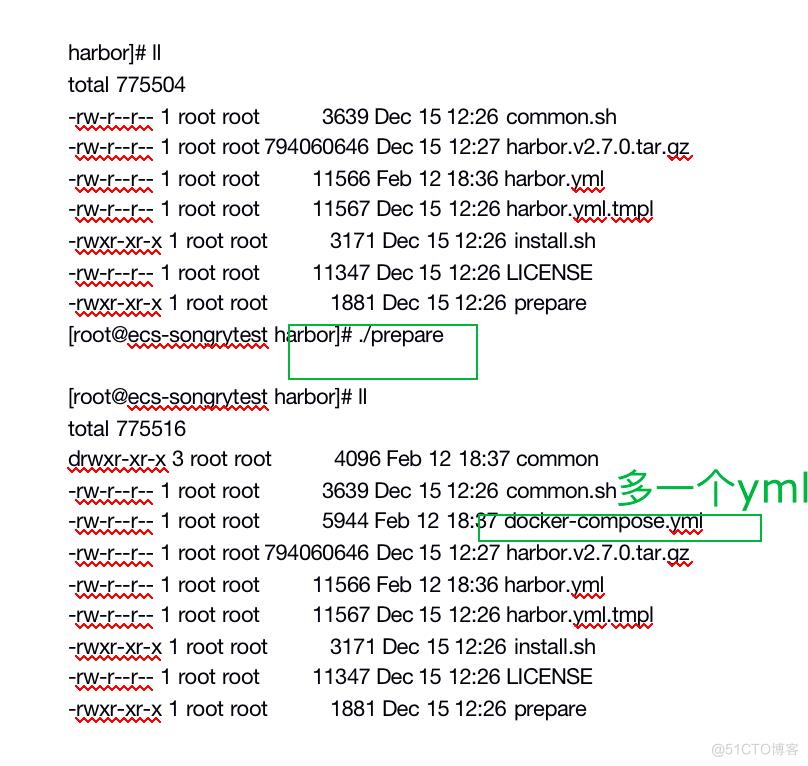
11、生成配置
harbor]# ./prepare
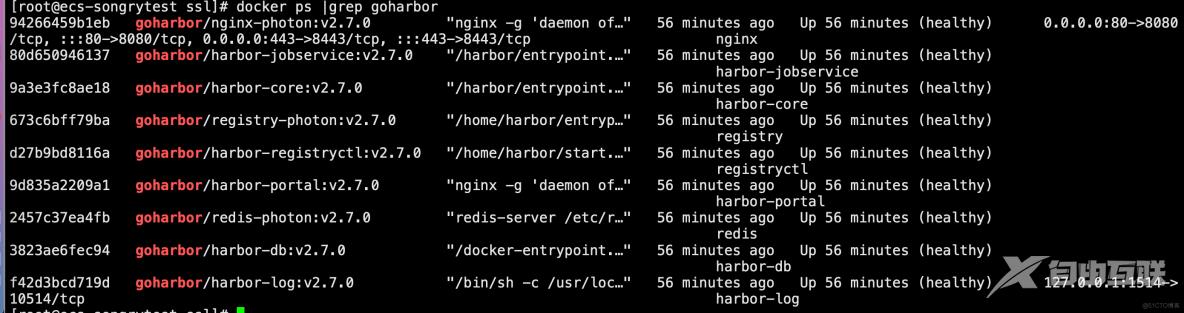
12、开始安装
harbor]# ./install.sh
注若是使用外包 redis :https://blog.51cto.com/lidabai/5296664
13、访问HTTPS
ip:80端口
用户名:admin
密码: Harbor12345
请记得及时修改默认密码
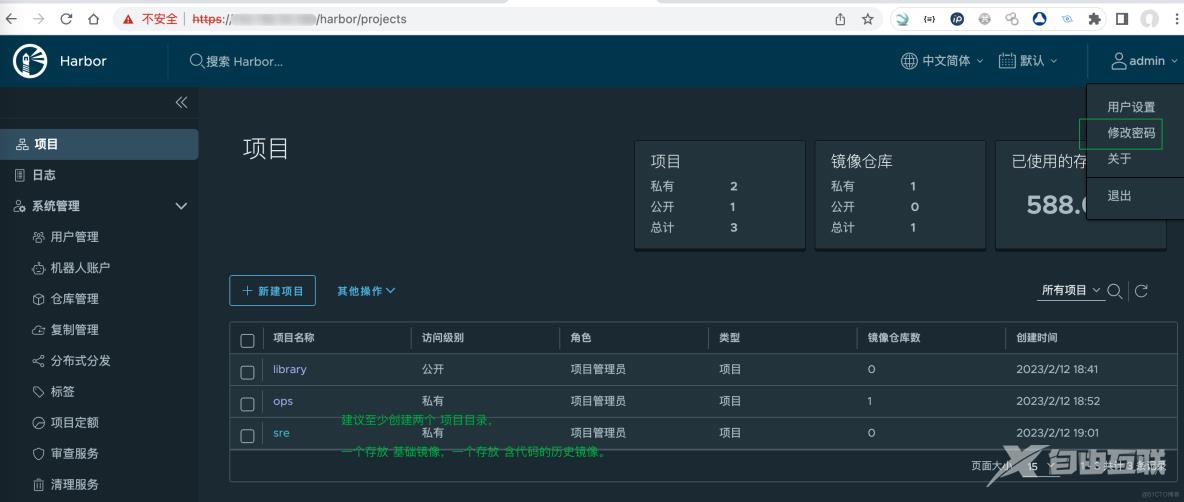
14、注册。
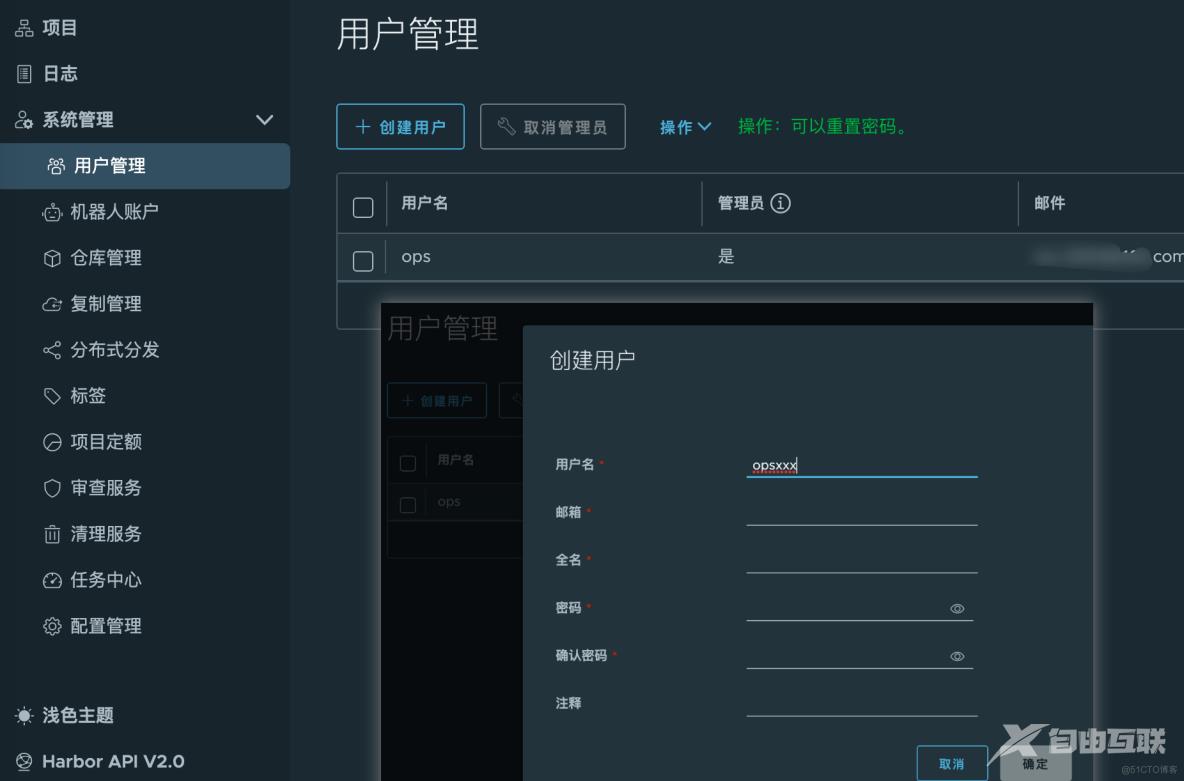
docker login 192.168.0.3
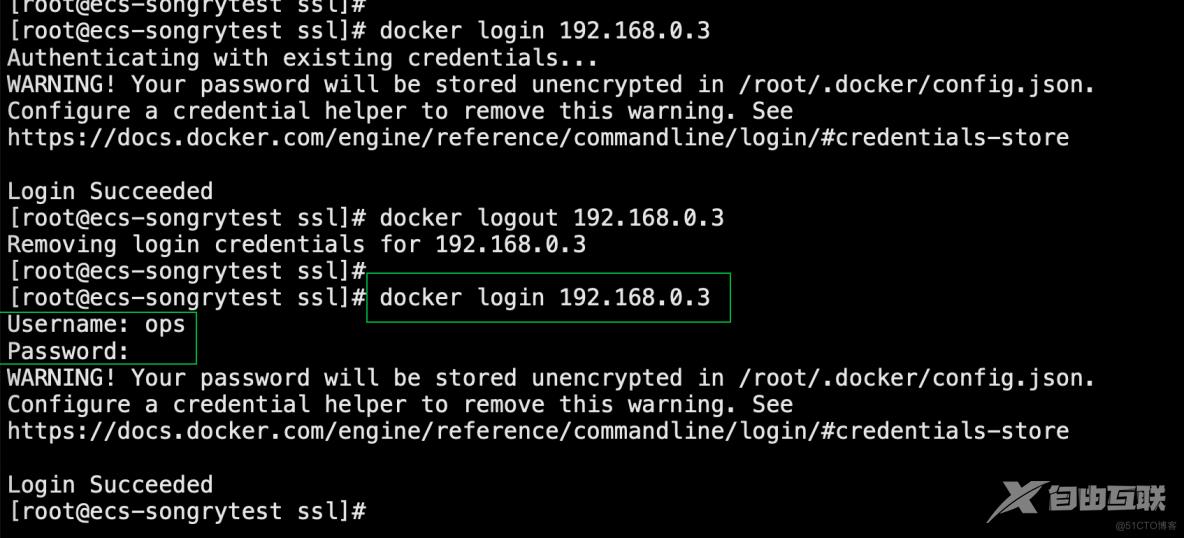
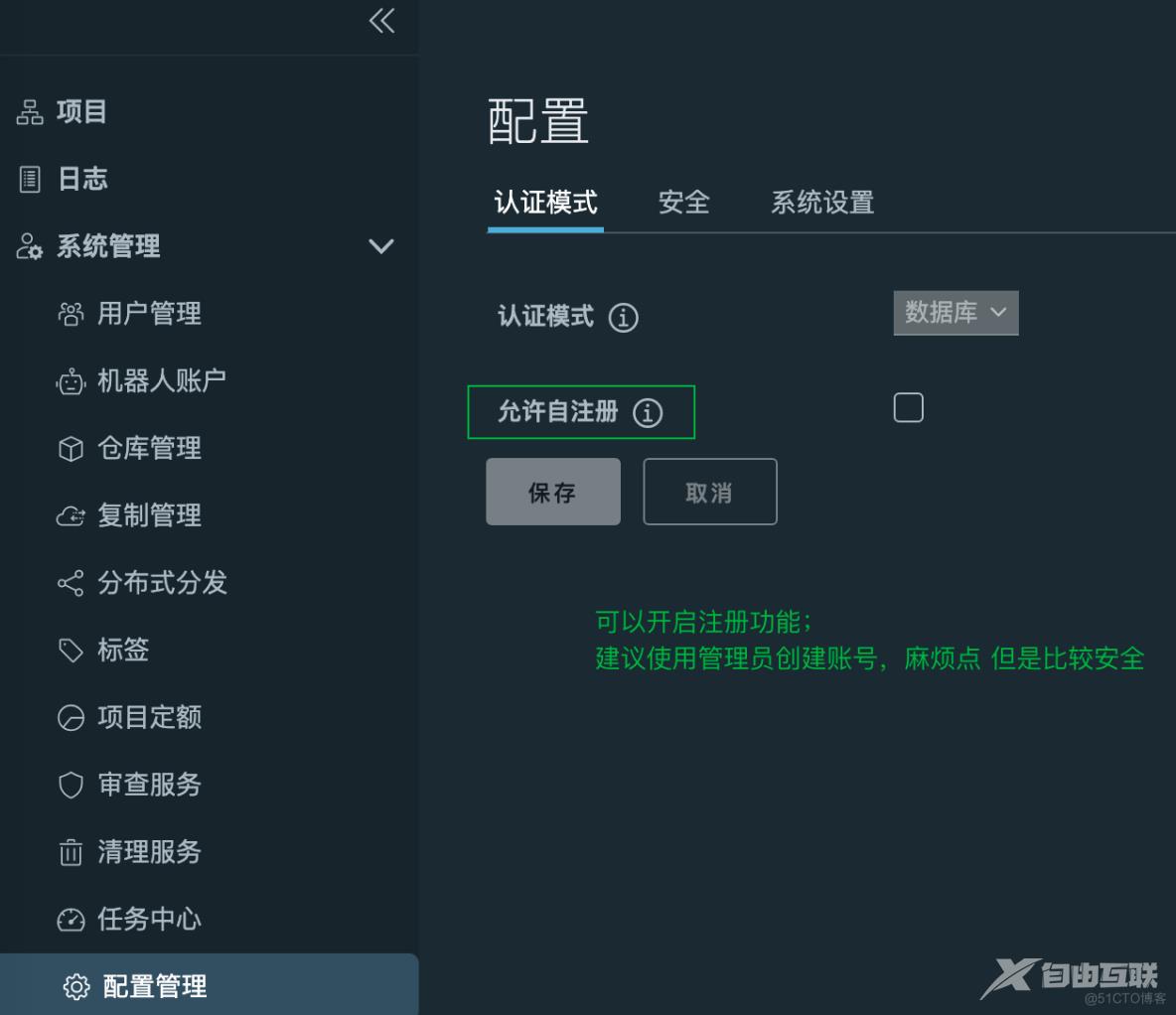
15、推送镜像测试
ssl]# docker login 192.168.0.3 #### 服务器登录harbor
Authenticating with existing credentials...
WARNING! Your password will be stored unencrypted in /root/.docker/config.json.
Configure a credential helper to remove this warning. See
https://docs.docker.com/engine/reference/commandline/login/#credentials-store
Login Succeeded
ssl]# docker images ##查看当前镜像
192.168.0.3/ops/centos8.4-py3.11.1-worker v1 c6f318dc97f7 44 hours ago 1.73GB
192.168.0.3/ops1/centos8.4-py3.11.1-worker v1 c6f318dc97f7 44 hours ago 1.73GB
centos8.4-py3.11.1-worker latest c6f318dc97f7 44 hours ago 1.73GB
[root@ecs-songrytest ssl]# docker tag centos8.4-py3.11.1-worker:latest 192.168.0.3/ops/centos8.4-py3.11.1-worker_ne1:v1
# 本地一个镜像,添加tag,到远程的harbor上标记
[root@ecs-songrytest ssl]# docker images
192.168.0.3/ops1/centos8.4-py3.11.1-worker v1 c6f318dc97f7 44 hours ago 1.73GB
centos8.4-py3.11.1-worker latest c6f318dc97f7 44 hours ago 1.73GB
192.168.0.3/ops/centos8.4-py3.11.1-worker v1 c6f318dc97f7 44 hours ago 1.73GB
192.168.0.3/ops/centos8.4-py3.11.1-worker_ne1 v1 ##已标记了。 c6f318dc97f7 44 hours ago 1.73GB
[root@ecs-songrytest ssl]#
#### 推送 标记的镜像到 远程 harbor
[root@ecs-songrytest ssl]# docker push 192.168.0.3/ops/centos8.4-py3.11.1-worker_ne1:v1
The push refers to repository [192.168.0.3/ops/centos8.4-py3.11.1-worker_ne1]
dcdba9dc9357: Pushed
08fd0aa2a842: Pushing [====================================> ] 1.104GB/1.498GB
命令格式:
login xxxxip:端口 ####服务器登录。
docker images 查看本地镜像。
docker tag 本地镜像id:版本 远程harbor_ip:port/项目名称/镜像名称:版本
docker push 远程harbor_ip:port/项目名称/镜像名称:版本
16、docker 登录信息在家目录下的~.docker/config.json文件中
[root@ecs-songrytest ssl]# cat ~/.docker/config.json
{
"auths": {
"192.168.0.3": {
"auth": "b3BzOjEyMxxxxxxxx"
},
"https://index.docker.io/v1/": {
"auth": "c29uZ3J5Oldxxxx5"
}
}
}[root@ecs-songrytest ssl]# docker logout 192.168.0.3
Removing login credentials for 192.168.0.3
[root@ecs-songrytest ssl]# cat ~/.docker/config.json
{
"auths": {
"https://index.docker.io/v1/": {
"auth": "c29uZ3J5Oldsaxxxx"
}
}
}[root@ecs-songrytest ssl]#
